
The monthly security event highlights of Zero Hour Technology have begun! According to statistics from some blockchain security risk monitoring platforms, the cryptocurrency field lost about $ 357 million in April 2025 due to hacker attacks, fraud and vulnerability exploits, of which the vast majority ($318 million) were related to phishing attacks. A total of 17 hacker attacks occurred, causing a loss of about $ 92.5 million. Most of the losses came from the two platforms UPCX and KiloEx, and the latter recovered some funds.
Hacker attacks
7 typical safety incidents
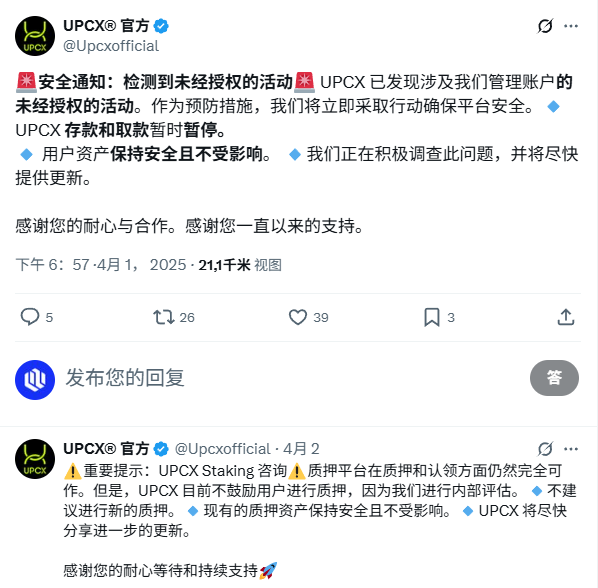
(1) On April 1, the official address of Upcx was suspected of being accessed without authorization. The attacker upgraded the "ProxyAdmin" contract and called the "withdrawByAdmin" function to transfer a total of 18.4 million UPCs (approximately US$70 million) from three management accounts. Currently, these funds are still stored in another address and have not been exchanged. Upcx officials have confirmed the incident and stated that "unauthorized activity has been detected."
(2) On April 8, according to monitoring, a MEV Bot (address: 0x49e27d11379f5208cbb2a4963b903fd65c95de09) lost approximately 116.7 ETH due to lack of access control.
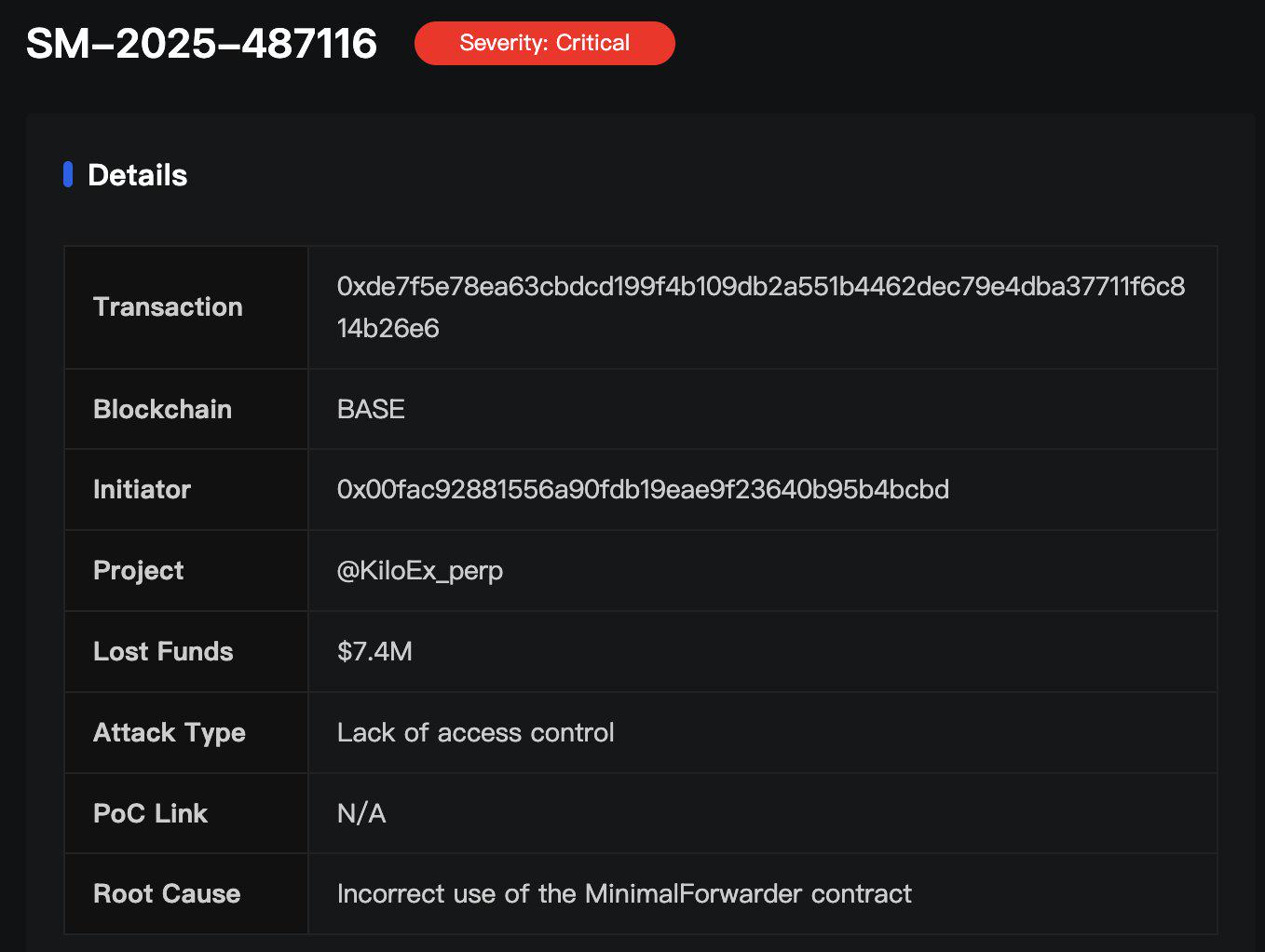
(3) On April 15, the decentralized perpetual futures exchange KiloEx was attacked, resulting in a loss of approximately US$7.4 million, involving multiple on-chain assets such as BNB and Base. According to the analysis of the SlowMist security team, the root cause of this incident was the lack of access control checks in the top-level contract (MinimalForwarder) of KiloEx, which led to the manipulation of the oracle price. With the collaboration of the project party and SlowMist and other parties, 100% of the funds affected in the event were successfully recovered.
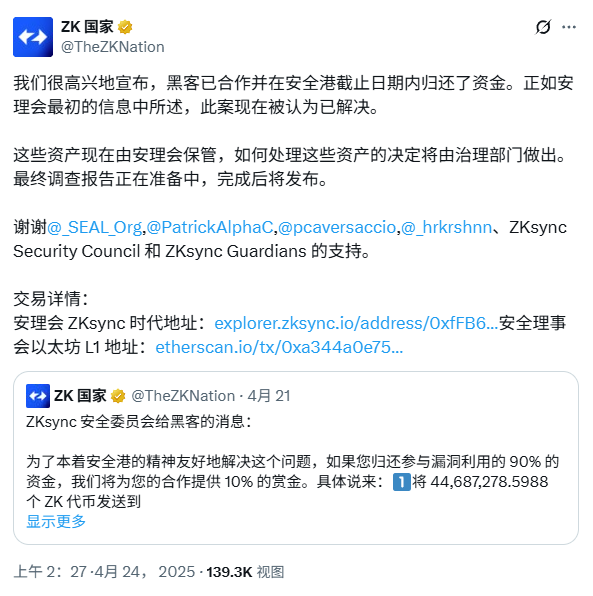
(4) On April 15, the ZKsync security team discovered a compromised administrator account that controlled approximately $5 million worth of ZK tokens (i.e., the remaining unclaimed tokens in the ZKsync airdrop). Investigations revealed that the administrator account for three airdrop distribution contracts had been compromised. The compromised account address is: 0x842822c797049269A3c29464221995C56da5587D.
On April 23, after the ZKsync Security Committee proposed a “safe harbor” agreement, the attacker returned all funds and the incident was resolved.
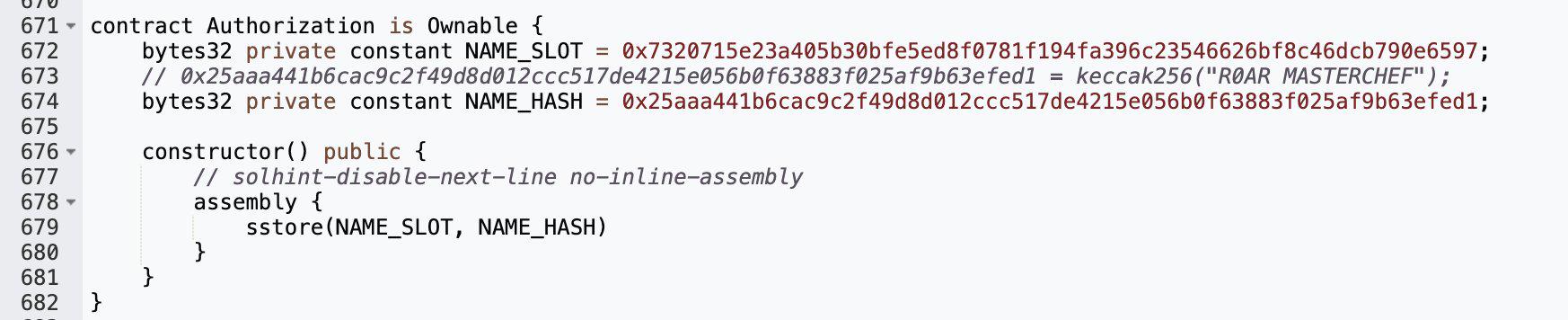
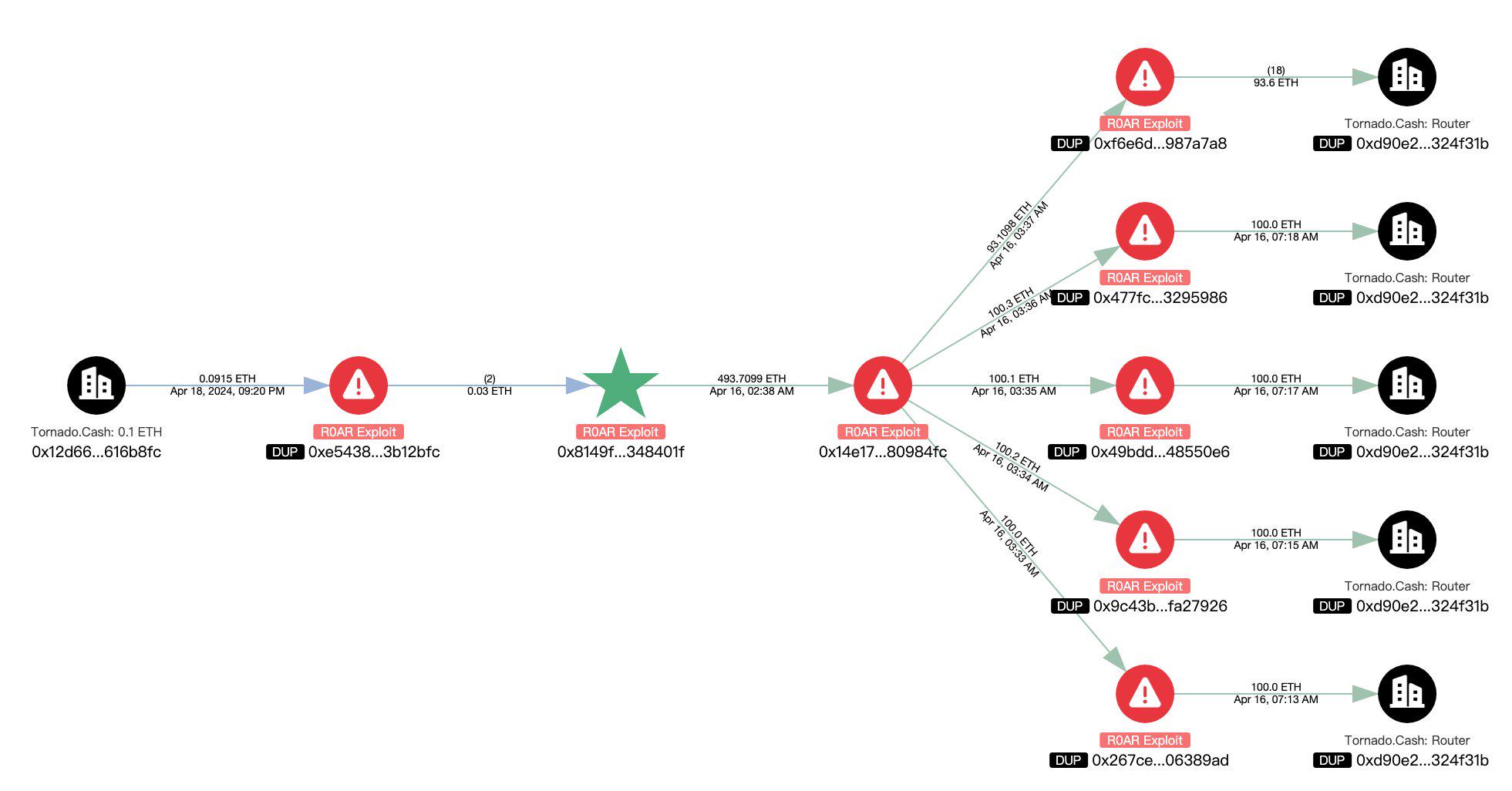
(5) On April 16, R0AR was attacked and lost approximately $780,000. According to analysis, the root cause of the attack was the existence of a backdoor in the contract. During the deployment process, the R0ARStaking contract tampered with the balance of a specified address (user.amount) by directly modifying the storage slot. Subsequently, the attacker used the emergency withdrawal function to withdraw all funds in the contract. R0AR tweeted: We currently believe that this is not an external attack. Preliminary investigations show that the theft of funds seems to be the work of a malicious developer who is not a member of the R0AR core team. He has been removed from the project and all permissions have been revoked.
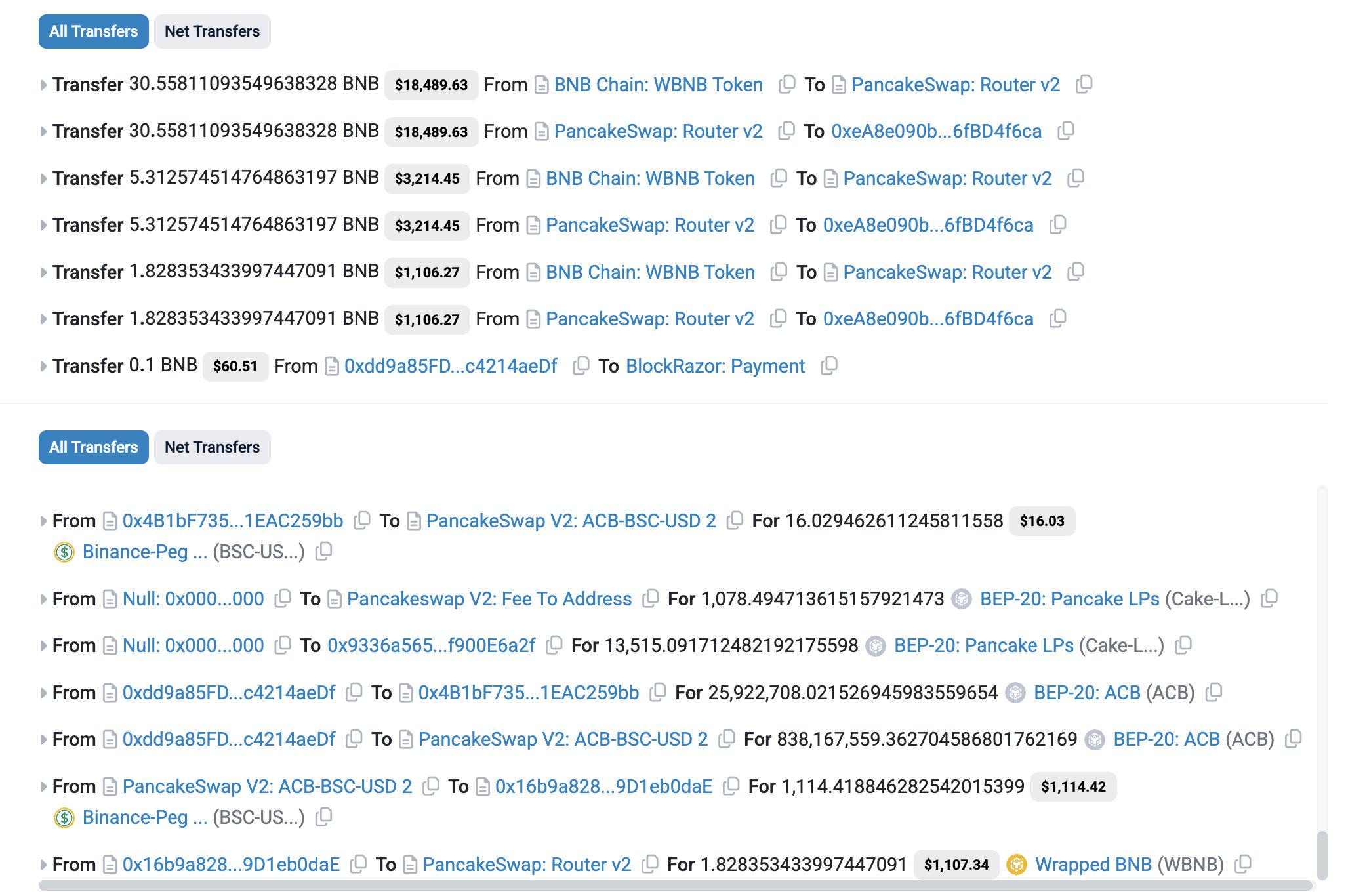
(6) On April 24, according to monitoring, ACB seemed to have been attacked on BSC, with losses of approximately US$22,000.
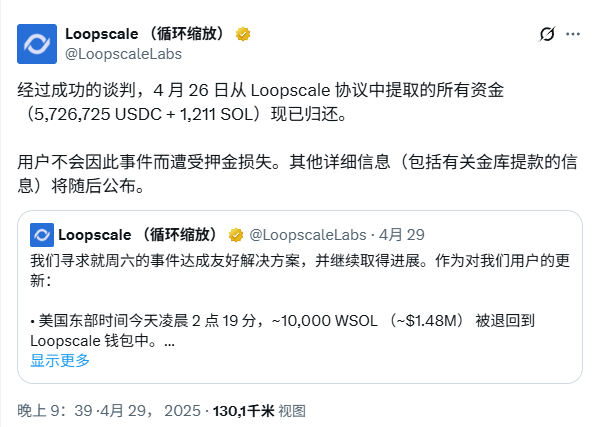
(7) On April 27, Loopscale, a modular DeFi lending market built on Solana, was attacked due to the manipulation of the RateX PT token pricing function, resulting in the theft of approximately 5.7 million USDC and 1,200 SOL, accounting for approximately 12% of the platform's total funds. The root cause of the attack has been confirmed to be an isolated issue with Loopscale's RateX-based collateral pricing mechanism. On April 29, Loopscale tweeted that after successful negotiations, all funds withdrawn from the Loopscale protocol on April 26 (5,726,725 USDC + 1,211 SOL) have now been returned.
Rug Pull / Phishing Scam
4 typical safety incidents
(1) On April 6, the address starting with 0x3822 lost $128,434 by signing an “approval” phishing transaction.
(2) On April 17, the address starting with 0xc1e lost $666,414 by signing multiple “allow” phishing signatures.
(3) On April 22, the address starting with 0x7C93 lost 234K USD (2.65 aArbWBTC) after signing a malicious “permission” signature.
(4) On April 22, the victim lost tokens worth $1.43M after the address starting with 0xa574 signed multiple phishing signatures.
Summarize
The losses in April increased significantly compared to March. Most of the illegal gains came from a single incident, where the attacker used complex social engineering methods to steal 3,520 bitcoins from the wallet. In addition, the decentralized exchange KiloEX lost $7.5 million due to a "price oracle vulnerability", Loopscale was stolen $5.8 million, and the Ethereum expansion protocol ZKsync airdrop contract was siphoned off nearly $5.3 million, but all three platforms have recovered funds from white hat hackers. Ethereum once again became the most attacked network, accounting for 60% of the total losses that month.
Phishing attacks are rampant at present. The Zero Hour Technology Security Team solemnly reminds: Crypto companies and investors must carefully verify the authenticity of the website and smart contract before making transfers. At the same time, it is recommended to use cold wallets to store assets and avoid exposing holdings on social media to build a solid asset security line. In addition, internal security training and authority management must be carried out well, and professional security companies must be found to conduct audits and conduct project background checks before the project goes online.













