Background
four.meme is a memecoin launchpad similar to pump.fun incubated by Binance Academy. The platform was hacked. The loss was about 180,000 USD. The attack transaction was:
https://bscscan.com/tx/0xd9177f643e29fea98a609a9a82cd97bb843f914e3eddf4fbaa6f0da7b5824f3d
Attack and incident analysis
The background knowledge has been described in detail in the previous analysis, and the specific details can be viewed in the previous article.
Zero Hour Technology || Analysis of the Four.meme attack
Attack Step 1:
The attack transaction hash is:
https://bscscan.com/tx/0x5a3abc55b60fbf73f186e153293325feaf06945f9033b7a11f07da6ff72554e4
In step 1, the attacker uses buyTokenAMAP to transfer the specified token to the PancakeSwap Pair WBNB-MubaraKing which has not been created yet. The description of buyTokenAMAP is as follows:
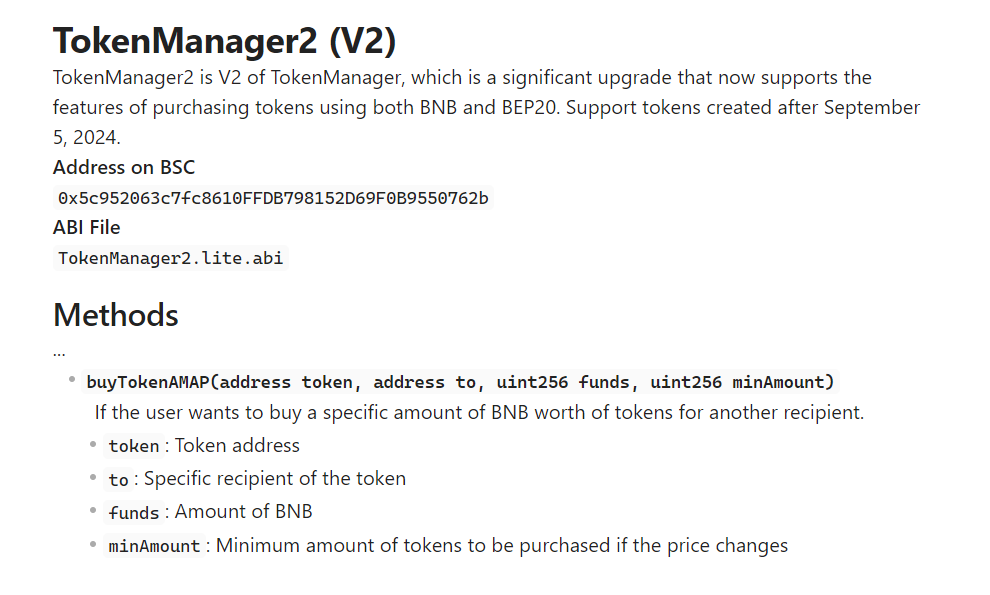
As you can see, this function can use BNB and BEP20 Token to buy meme coins for the specified address. The reason why the attacker used buyTokenAMAP is mainly because when the token is traded on the internal disk, it cannot be freely transferred through transfer. Moreover, since the address of PancakeSwap Pair is predictable, the attacker calculated the address of PancakeSwap PairWBNB-MubaraKing in advance. As a result, the attacker completed the operation of transferring meme coins to the Pair before the project was migrated to DEX.
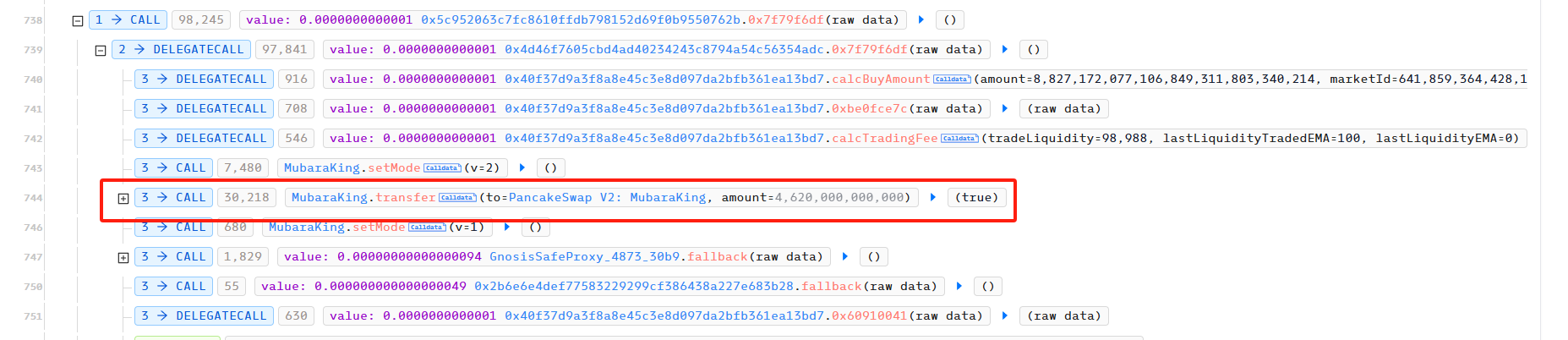
We can see that the block where this transaction is located is 47556809, and the block time is 2025-03-17 22:54:53 (UTC).
Attack Step 2:
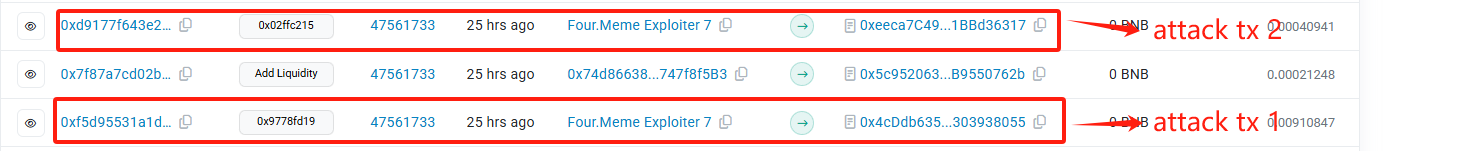
The attack transaction hash is:
https://bscscan.com/tx/0xf5d95531a1dd612f5e1c65b513d227360a66287e35f67e6e04a97321d3faae14
https://bscscan.com/tx/0xd9177f643e29fea98a609a9a82cd97bb843f914e3eddf4fbaa6f0da7b5824f3d
When the Token completes the transaction target in the internal disk, that is, the Bonding Curve Process reaches 100%, the internal disk will be migrated to PancakeSwap, that is, the external disk. The attacker uses MEV to perform a sandwich attack, sandwiching the migration transaction in the middle, adding liquidity to the Pair, and then withdrawing the liquidity after the official website has added liquidity, and then exchanging the MubaraKing in hand for WBNB to obtain huge profits.
In attack transaction 1, the attacker created the PancakeSwap Pair WBNBMubaraKing through PancakeSwap Factory. Since MubaraKing has been transferred to this Pair using buyTokenAMAP in attack step 1, the balance of MubaraKing in the Pair is 4,620,000,000,000.
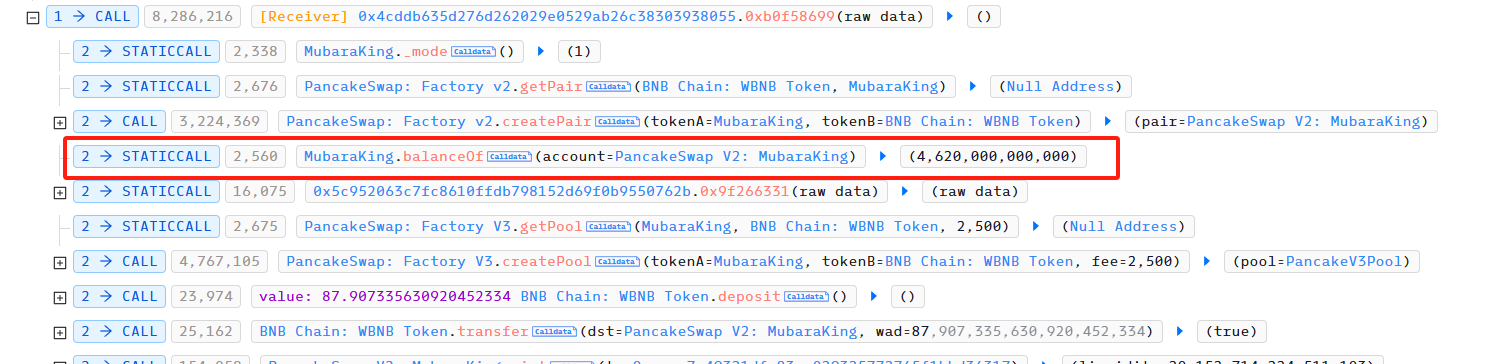
Afterwards, the attacker transferred 87.9 WBNB and used mint to obtain LP Token to add liquidity in advance.
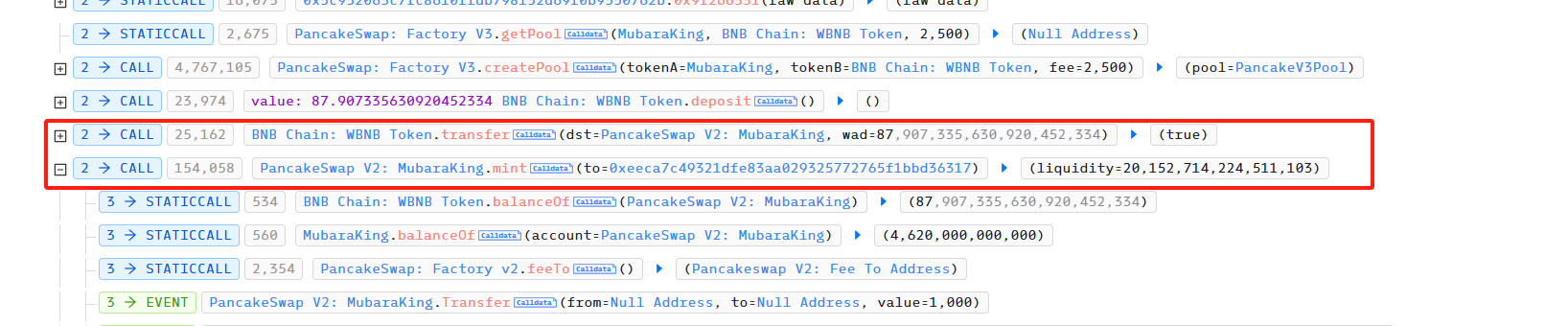
In attack transaction 2, the attacker first used burn to withdraw the liquidity he added, and obtained 87.9 WBNB and 157,784,147,190,821,450,996,866,034 MubaraKing.
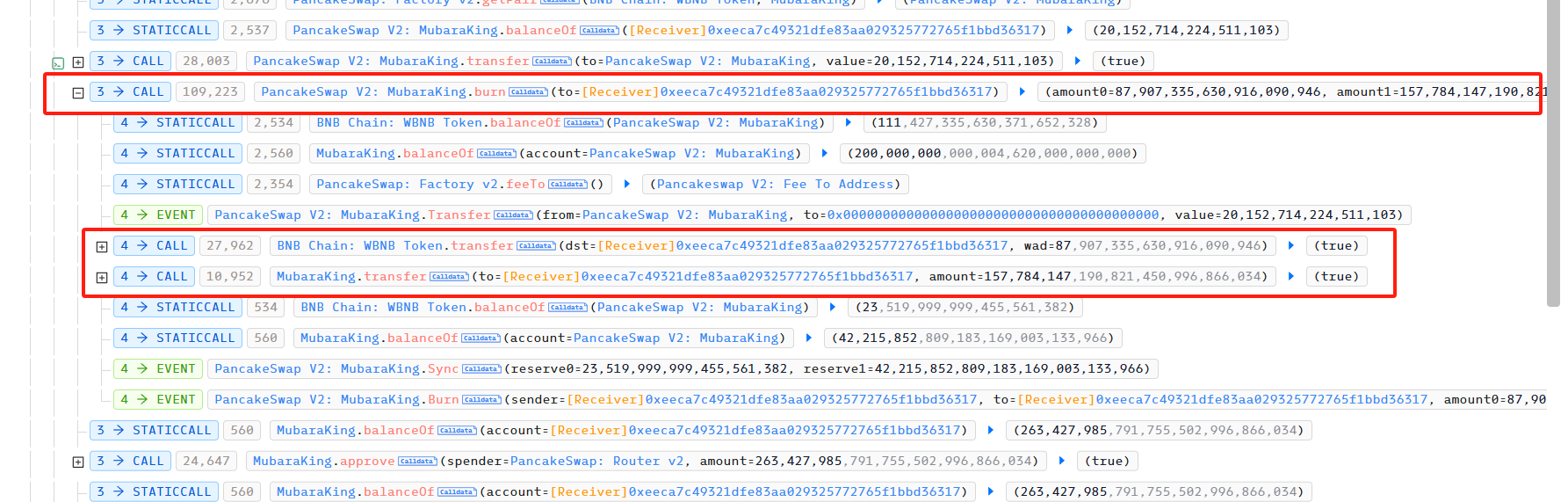
Afterwards, he used PancakeSwap to exchange the MubaraKing in his hands for 20 WBNB, and finally completed the attack.
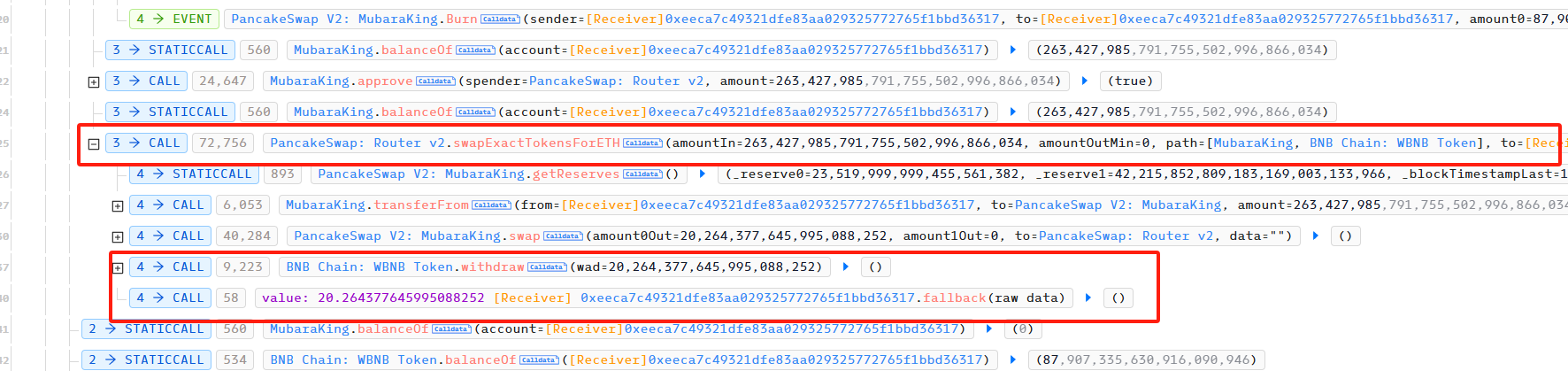
The block number of these transactions is 47561733 and the block time is 2025-03-18 03:01:05 (UTC ).
Summarize
The cause of this vulnerability is:
1. When trading in the internal market, you can use buyTokenAMAP to transfer funds to addresses that cannot initiate transactions, bypassing the restriction that internal transactions cannot be transferred, resulting in the addition of liquidity in advance.
2. The bonding curve process of Four.meme in the internal disk is 100%. When migrating to DEX, it did not take into account the situation that liquidity had been added in advance. As a result, after the migration, the attacker first withdrew the liquidity added in advance, and then used the memecoin in his hand to empty the WBNB in the pool to complete the attack. It is recommended that the project party should verify multiple parties when designing the economic model and code operation logic, and try to select multiple audit companies for cross-audit when auditing the contract before going online.












