
The report focuses on four major directions: Move, TON, Bitcoin expansion, and Cosmos application chain. It provides detailed interpretation from three aspects: technological innovation, security challenges, and historical security incidents, and provides some experience and thinking directions for investors, developers, and white hat hackers:
Move ecosystem (Aptos, Sui, etc.)
The report introduces how the Move language revolutionizes smart contract programming in terms of resource management, modular design, and built-in security mechanisms, and provides an in-depth analysis of the innovations and security architectures of Aptos and Sui.
Move was originally developed by Facebook (now Meta) for the Diem (Libra) project to address the performance and security bottlenecks of traditional smart contract languages. Move's design emphasizes the clarity and security of resources to ensure the controllability of each state change on the blockchain. This innovative programming language has the following significant advantages:
Resource management model: Move treats assets as resources, making them non-copyable or non-destructible. This unique resource management model avoids the common double-spending or accidental destruction of assets problems in smart contracts.
Modular design: Move allows smart contracts to be built in a modular way, improving code reusability and reducing development complexity.
High security: Move has a large number of built-in security check mechanisms at the language level to prevent common security vulnerabilities, such as reentrancy attacks.
In addition, the report also reviews typical security incidents that occurred in the Move virtual machine and the Aptos network from 2023 to the end of 2024, in order to remind the community to be vigilant about potential infinite recursive DoS vulnerabilities in the network, memory pool eviction mechanism defects and other problems.
For a detailed review of Move ecological safety incidents, please download the report to read
TON Ecosystem
TON (The Open Network) is a blockchain and digital communication protocol created by Telegram, aiming to build a fast, secure and scalable blockchain platform to provide users with decentralized applications and services. By combining blockchain technology and Telegram's communication capabilities, TON achieves high performance, high security and high scalability. It supports developers to build various decentralized applications and provides distributed storage solutions. Compared with traditional blockchain platforms, TON has faster processing speed and throughput, and adopts the Proof-of-Stake consensus mechanism.
TON uses a proof-of-stake consensus mechanism and achieves high performance and versatility through its Turing-complete smart contracts and asynchronous blockchain. TON's lightning-fast and low-cost transactions are supported by the chain's flexible and shardable architecture. This architecture allows it to scale easily without losing performance. Dynamic sharding involves the initial development of separate shards with their own purposes that can run simultaneously and prevent large-scale backlogs. TON has a block time of 5 seconds and a finalization time of less than 6 seconds.
The existing infrastructure is divided into two main parts:
●Masterchain: Responsible for handling all important and critical data of the protocol, including the addresses of validators and the amount of coins verified.
●Workchain: A secondary chain connected to the main chain, containing all transaction information and various smart contracts. Each workchain can have different rules.
The TON Foundation is a DAO operated by the TON core community, providing various support to projects in the TON ecosystem, including developer support and liquidity incentive programs. The report details the significant progress made by the TON community in many aspects in 2024. The report also reveals the recent vulnerability of malicious contracts that can cause virtual machine resource exhaustion through nested structures, warning all parties to continue to strengthen contract security audits.
For more details about the TON ecosystem, please download the report.
Bitcoin Ecosystem Expansion
Layer 2 and sidechain solutions, including Lightning Network, Liquid Network, Rootstock (RSK), B² Network, Stacks, etc., are driving breakthroughs in Bitcoin's transaction expansion and programmability. Lightning Network improves transaction efficiency, Liquid Network accelerates inter-institutional transactions, and Rootstock combines security and smart contracts to expand the dApp ecosystem. In addition, B² Network and Stacks further deepen Bitcoin's functions and application scenarios.
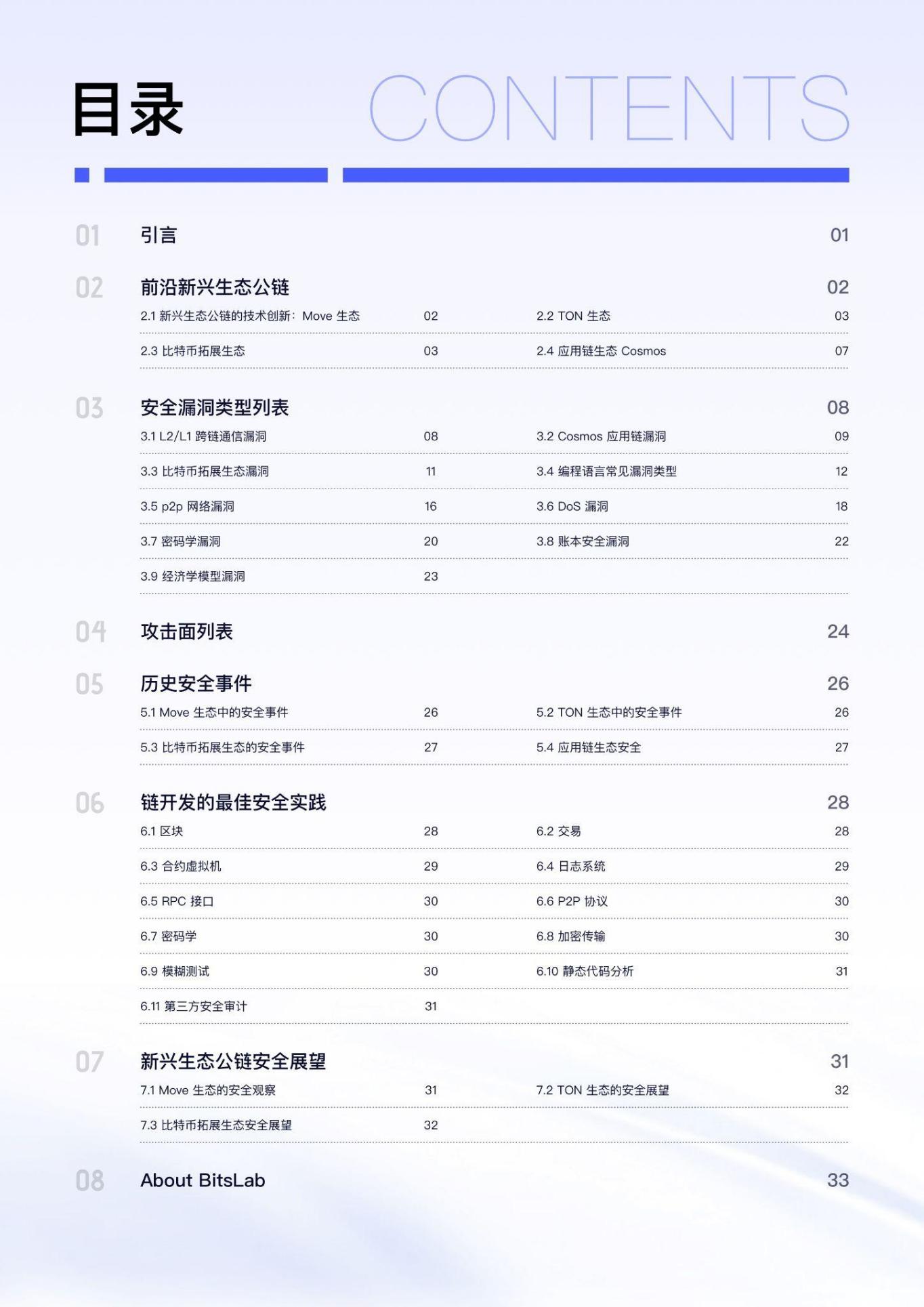
The Lightning Network is one of the most mature and widely used solutions for Bitcoin Layer 2. It establishes payment channels and moves a large number of small transactions from the main chain to the off-chain, thereby greatly increasing Bitcoin's transaction speed and reducing handling fees.
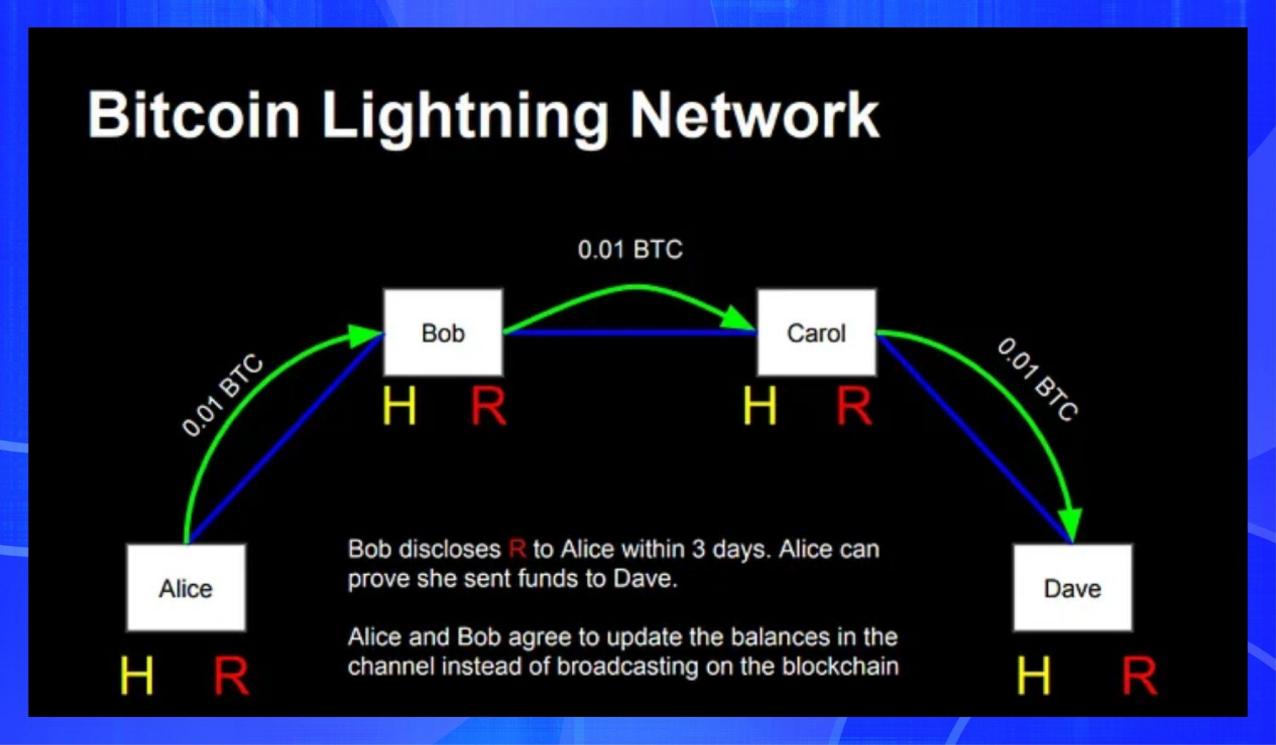
Image source: https://lightning.network/lightning-network-presentation-time-2015-07-06.pdf
Liquid Network is a sidechain running on the open source Elements blockchain platform, designed for faster transactions between exchanges and institutions. It is governed by a distributed alliance of Bitcoin companies, exchanges, and other stakeholders. Liquid uses a two-way peg mechanism to convert BTC to L-BTC and vice versa.
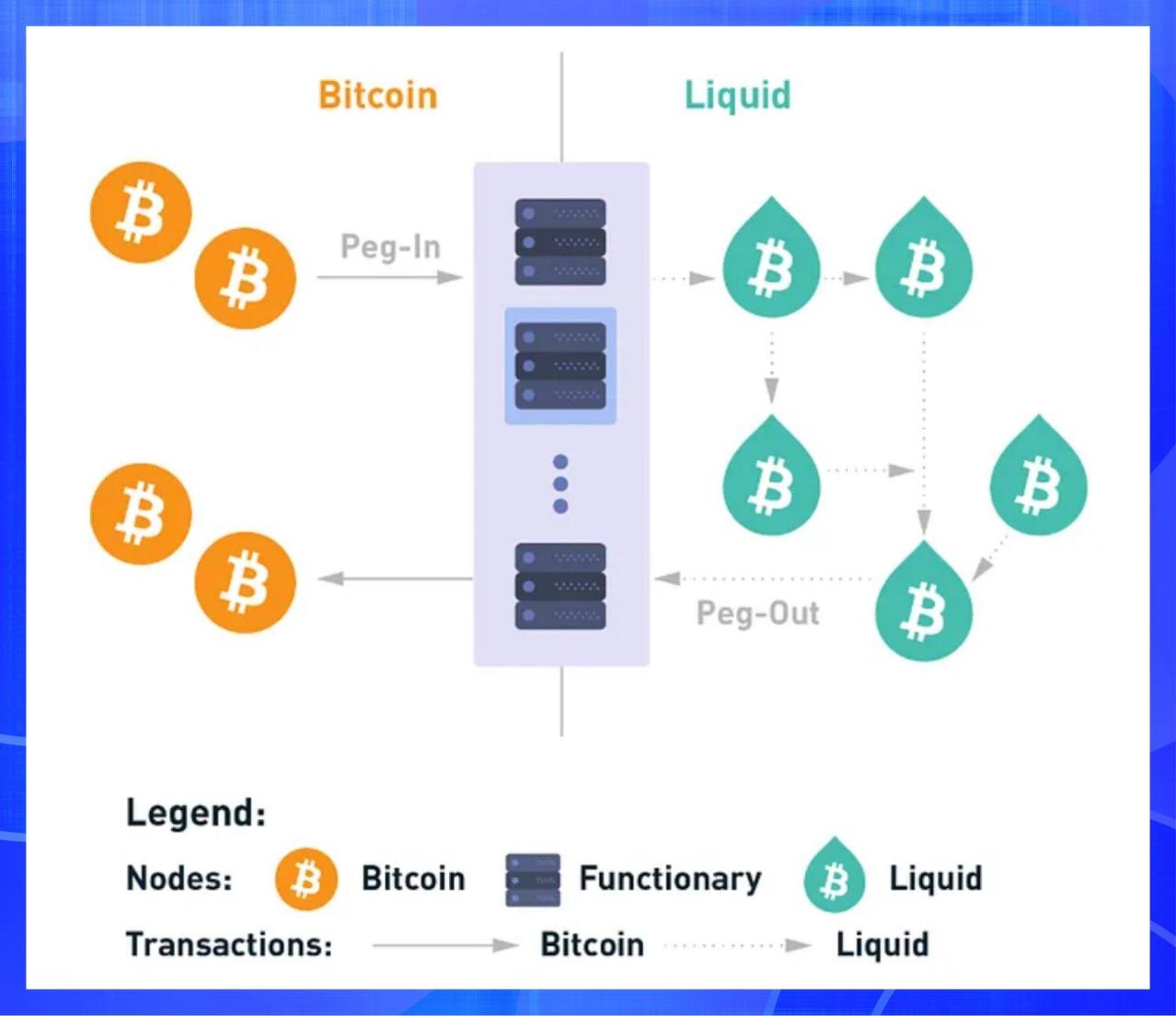
Image source: https://docs.liquid.net/docs/technical-overview
Rootstock is the longest-running Bitcoin sidechain since its creation in 2015, and launched its mainnet in 2018. It is unique in that it combines Bitcoin's Proof of Work (PoW) security with Ethereum's smart contracts. As an open source, EVM-compatible Bitcoin Layer 2 solution, Rootstock provides an entry point for the growing dApp ecosystem and is committed to achieving full trustlessness.
B² Network's technical architecture consists of two layers: Rollup layer and Data Availability (DA) layer. B² Network aims to redefine users' views on Bitcoin's second-layer solutions.
Since its launch on the mainnet in 2018 under the name Blockstack, Stacks has become the leading Bitcoin Layer 2 solution. Stacks connects directly to Bitcoin, allowing smart contracts, dApps, and NFTs to be built on Bitcoin, significantly expanding Bitcoin's functionality to more than just a store of value. It uses a unique Proof of Transfer (PoX) consensus mechanism that ties its security directly to Bitcoin without modifying Bitcoin itself.
Image source: https://docs.stacks.co/stacks-101/proof-of-transfer
Babylon's vision is to extend the security of Bitcoin to protect the decentralized world. By leveraging three aspects of Bitcoin - its timestamping service, block space, and asset value - Babylon is able to deliver Bitcoin's security to numerous Proof of Stake (PoS) chains, creating a more powerful, unified ecosystem.

Although these technologies bring more possibilities to the Bitcoin ecosystem, they also face challenges such as the Lightning Network "substitution cycle attack", UTXO calculation errors, and PoW rollback mechanism risks.
Read the full report to get more details about the Bitcoin ecosystem
Cosmos Application Chain Ecosystem
With Tendermint consensus, Cosmos SDK and IBC cross-chain communication as the core, it has many technological innovations in the design of blockchain Internet.
The Cosmos architecture adopts the Hub and Zone model. The Hub (center) serves as the core node of the cross-chain, connecting and coordinating multiple Zones (independent blockchains). The innovation of this architecture is:
Decentralized management: Each Zone is an independent, autonomous blockchain that does not need to rely on a single centralized management node.
Efficient cross-chain connection: Through the Hub, Zones can seamlessly communicate and transfer assets across chains, achieving true interconnection.
The report deeply analyzes the potential security risks of the Cosmos application chain, from the order of multi-module calls to cross-chain message transmission, and combines the security disputes and governance process issues of the Liquidity Staking Module (LSM) to provide warnings and inspiration for more application chain projects.
Read the full report to get more details about the Cosmos application chain ecosystem
Years of vulnerability research results
The report details the nine types of security vulnerabilities that are common in the blockchain industry. These vulnerabilities not only run through different technical levels, but also involve core components of multiple blockchain ecosystems, covering all aspects from cross-chain communication to economic model design.
1. L2/L1 cross-chain communication vulnerability: Cross-chain communication is an important means to improve the interoperability of the blockchain ecosystem, but there are also many security risks in its implementation. For example, L2 does not consider L1's block rollback, chain event forgery, and L2 does not detect whether the transaction sent to L1 is successful.
2. Cosmos application chain vulnerabilities: As an ecosystem with blockchain interoperability as its core, Cosmos allows different blockchains to be connected through IBC (inter-chain communication protocol). However, the Cosmos application chain may also have some vulnerabilities and security risks in the implementation process, such as BeginBlocker and EndBlocker crash vulnerabilities, incorrect use of local time, incorrect use of random numbers, and 11 other vulnerabilities and security risks.
3. Bitcoin expansion ecosystem vulnerabilities: including Bitcoin script construction vulnerabilities, vulnerabilities caused by not considering derivative assets, UTXO amount calculation errors, etc.
4. Common vulnerabilities in programming languages (such as dead loops, infinite recursion, integer overflows, race conditions, etc.)
5. P2P network vulnerabilities: P2P (peer-to-peer) networks are used for direct connection and communication between distributed nodes in blockchain systems. Although P2P networks provide a network foundation for decentralized systems, they also face a series of common vulnerability types such as alien attack vulnerabilities, lack of trust model mechanism, lack of node number limit mechanism, etc.
6. DoS attacks : including memory exhaustion attacks, hard disk exhaustion attacks, kernel handle exhaustion attacks, persistent memory leaks, etc.
7. Cryptography vulnerabilities: Cryptography vulnerabilities can undermine the confidentiality and integrity of data, posing potential security threats to the system. The main types of cryptography vulnerabilities include using hash algorithms that have been proven to be insecure, using insecure custom hash algorithms, and hash collisions caused by insecure use.
8. Ledger security vulnerabilities: (such as transaction memory pool vulnerabilities, block hash collision vulnerabilities, orphan block processing logic vulnerabilities, Merkle tree hash collision vulnerabilities, etc.)
9. Economic model loopholes: Economic models play a vital role in blockchain and distributed systems, affecting the network's incentive mechanism, governance structure and overall sustainability. The economic model loopholes listed in the report need special attention.
Read the full report to learn more about the types of security vulnerabilities
List of common attack surfaces
The report also lists 13 common attack surfaces. Each link may become a breakthrough for hacker attacks, which deserves extra attention from developers and project owners:
1. Virtual Machine
2. P2P node discovery and data synchronization module
3. Block parsing module
4. Transaction analysis module
5. Consensus protocol module
6. “Please check the report for other attack surfaces”
…
Best Practices for Secure Development
Through rich case reviews and attack and defense practices, the report distills a systematic security response approach.
In terms of security protection, this report specifically provides detailed suggestions on the best practices for chain development, covering block and transaction processing, smart contract virtual machines, logging systems and RPC interfaces, P2P protocol design to prevent DoS attacks, encryption and authentication at the transport layer, fuzz testing and static code analysis, third-party security audit processes, etc., striving to provide clear and feasible security guidance for the entire life cycle of blockchain projects.
Please download the report for detailed security development best practices.











