Author: Lisa & Aro
Editor: Liz
In today's Internet environment, threats such as malware, viruses, and phishing attacks emerge in an endless stream. Installing antivirus software (such as AVG, Bitdefender, Kaspersky, Malwarebytes and other internationally renowned products) can help users prevent malicious programs and improve system security. However, the role of antivirus software is to provide basic security protection. It can only reduce risks and cannot guarantee absolute security. Confrontation is a dynamic process, and installing antivirus software is only the first step to improve security. At the same time, antivirus software itself may also have false positives, bringing additional risks.
Recently, some users have reported that after using antivirus software, some browser extensions (especially cryptocurrency wallet extensions) were mistakenly reported as malware, causing the extension's JavaScript files to be isolated or deleted, and ultimately the extension wallet was damaged and could not be used normally.
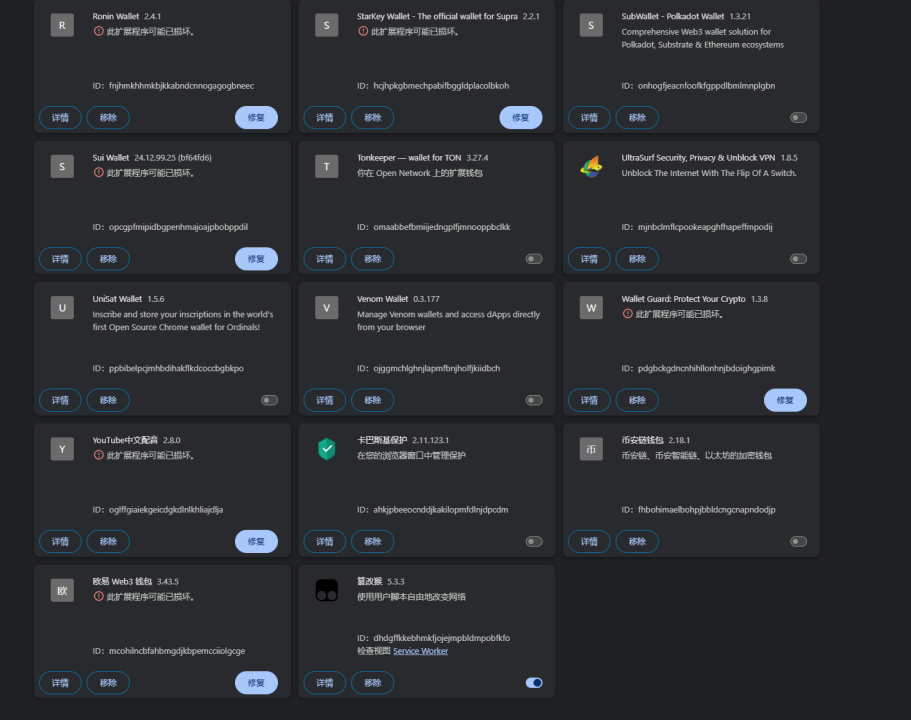
This situation is particularly serious for Web3 users, because crypto wallet extensions usually store private keys, and if not handled properly, it may lead to the loss of wallet data or even the inability to recover assets. Therefore, it is crucial to understand how to properly restore extension data that has been misreported and isolated.
HOW DOES IT HANDLE?
If you find that the browser extension is damaged due to false positives from the antivirus software, it is recommended to restore it by following the steps below:
1. Restore the file from quarantine and do not uninstall the extension
If you find that a software or extension cannot run, check the "Quarantine" or "History" of the antivirus software immediately to find the false positive files. Do not delete the quarantined files.
- If the file is still in quarantine, select Restore and add the file or extension to your trusted list to prevent false positives in the future.
- If the file has been deleted, check whether there is an automatic backup or use a data recovery tool to retrieve it.
- Remember: Do not uninstall the extension! Even if the extension is damaged, the encrypted private key files may still be stored locally, and it is still possible to recover them.
2. Back up and find local extension data
The data of the extension is usually stored on the local disk. Even if the extension cannot be opened, the relevant data can still be found for recovery (the extension ID takes MetaMask as an example: nkbihfbeogaeaoehlefnkodbefgpgknn):
- Windows path reference: C:\Users\USER_NAME\AppData\Local\Google\Chrome\User Data\Default\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
- Mac path reference:
~/Library/Application Support/Google/Chrome/Default/Local Extension Settings/nkbihfbeogaeaoehlefnkodbefgpgknn
It should be noted that if Chrome uses multiple account configurations, the Default in the path may become Profile 1/Profile 2. You need to check the specific Profile directory and adjust the path according to the actual situation. It is recommended to back up the complete directory of the target extension as soon as possible so that it can be restored in case of problems.
3. Rough recovery method: overwrite the local extension directory
If a false alarm causes the extension to be damaged, the most direct way is to overwrite the backed-up extension data directly to the extension directory corresponding to the local path in a new computer or new browser environment, and then reopen the extension.
4. Advanced recovery method: Manually decrypt private key data
If the extension still cannot be opened or data is missing, you can try a more advanced recovery method, which is to manually decrypt the private key data to recover. Take MetaMask as an example:
- Search for the MetaMask extension ID locally on your computer and find the following directory: C:\Users\[User]\AppData\Local\Google\Chrome\User Data\Default\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
- This directory may contain ldb/log files, which store encrypted private key data. You can use MetaMask's official Vault decryptor tool (https://metamask.github.io/vault-decryptor/) to decrypt it.
- Decryption steps: Open the MetaMask Vault decryption tool -> copy the encrypted content in the ldb/log file -> use the extended original password to decrypt -> after obtaining the private key, re-import the wallet.
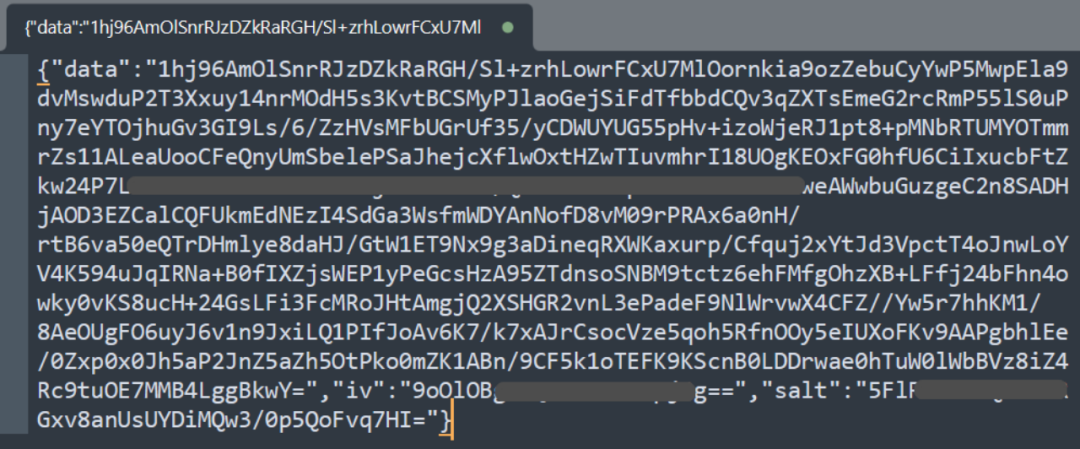
If the MetaMask extension can still open certain pages (such as chrome-extension://nkbihfbeogaeaoehlefnkodbefgpgknn/home.html), you can try running the following code to obtain the encrypted private key data:
chrome.storage.local.get('data', result => { var vault = result.data.KeyringController.vault; console.log(vault);});
Then, copy the vault data to the MetaMask Vault decryption tool for decryption.
5. Writing a custom recovery tool
If the above method cannot recover the wallet data, the user can write a script to extract the extended storage data from the local database file and then decrypt it. Here, PhantomKeyRetriever is used as a template to write the underlying principles and implementations of different wallet recovery tools as follows:
Wallet plugins usually store sensitive data in a database or file on the local system. Browser extension wallets (such as Phantom, MetaMask, etc.) use the storage API provided by the browser to save encrypted data in the browser's local storage area, usually a database system such as LevelDB or IndexedDB. Regardless of the type of wallet, a key principle is that data is always stored in an encrypted form, ensuring that even if the data is copied, it cannot be accessed without the correct password.
Most crypto wallets use a multi-layer encryption architecture to enhance security. First, the user's master password is used to encrypt an intermediate key (often called an "encryption key" or "decryption key"). This intermediate key is then used to encrypt the actual private key or mnemonic. This design ensures that even if the wallet application's code is tampered with, the attacker only needs to know the user's password to obtain the private key. This multi-layer design also allows the wallet application to only decrypt the intermediate key after the user logs in, without having to re-enter the master password for each operation.
The process of writing a wallet recovery tool usually includes:
- Locate and extract encrypted data (read data from LevelDB/IndexedDB).
- Analyze data structures and identify encrypted private keys/mnemonics.
- The user is required to enter the wallet password and the decryption key is calculated through KDF (such as PBKDF2 or Scrypt).
- Decrypt the intermediate key and then decrypt the private key/mnemonic.
This process requires precise knowledge of the wallet’s encryption scheme and data storage format, which is usually obtained through reverse engineering or analyzing the wallet’s open source code.
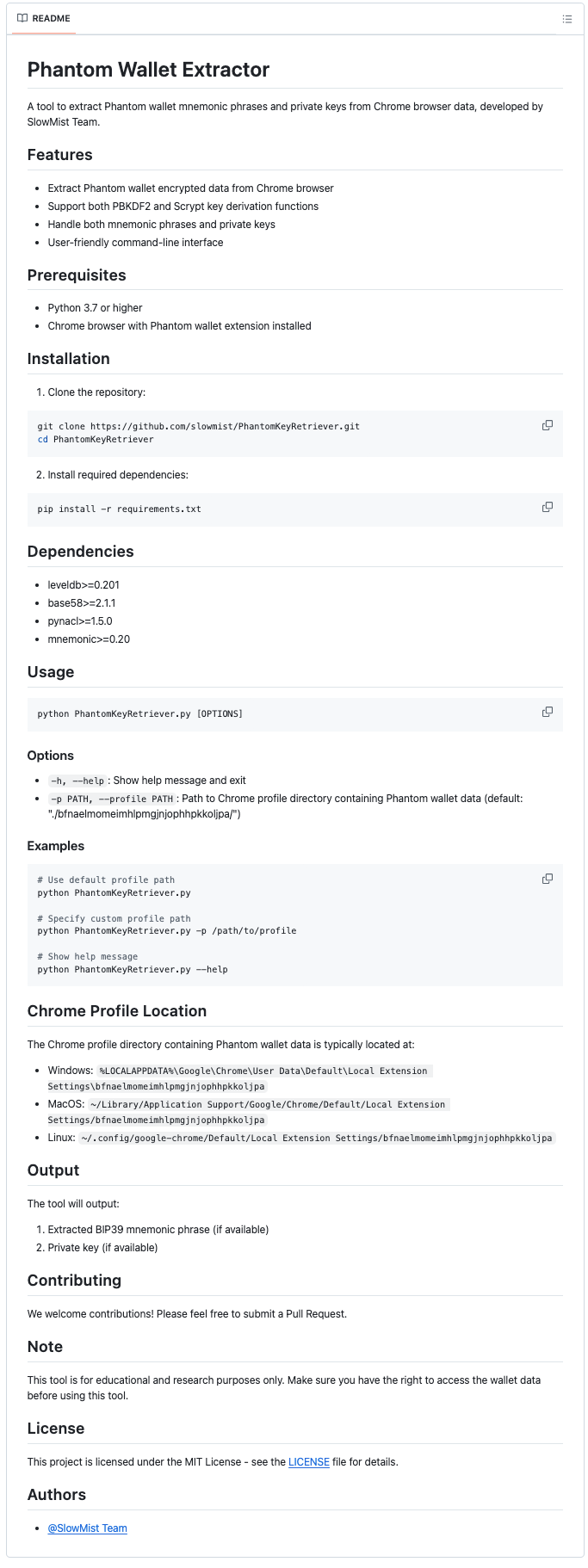
Take the PhantomKeyRetriever tool for example. This is a script specifically designed to extract the Phantom wallet mnemonics or private keys from Chrome browser data. SlowMist has now open-sourced this tool on GitHub (https://github.com/slowmist/PhantomKeyRetriever). Its core principles are as follows:
- Read the Chrome LevelDB database and copy the relevant data to a temporary directory.
- Traverse the database to find the encryption key and wallet seed information stored by the Phantom wallet.
- The user enters the Phantom password, and the script uses PBKDF2/Scrypt to calculate the decryption key.
- Decrypt wallet vault data and extract BIP39 mnemonic or Base58 private key.
In this two-layer decryption process, the script supports two key derivation functions, PBKDF2 and Scrypt, and uses the SecretBox of the NaCl library for secure decryption. Finally, depending on the type of decrypted data, the script will generate a BIP39 standard mnemonic or extract a Base58-encoded private key.
It should be noted that other browsers that support extended wallets (such as Edge and Firefox) follow a similar principle and will not be elaborated here.
How to prevent it?
To reduce the risk of false positives, users can take the following actions:
- Regularly back up important files and browser extension data so that you can quickly restore them if a false positive occurs.
- Manually add trust rules in the antivirus software. For important software or extensions (such as MetaMask), you can manually add them to the trust list to prevent false positives.
- Use official channels to download software and avoid installing unofficial or modified versions of applications to reduce the chances of being flagged as a potential risk by antivirus software.
Summarize
The confrontation is always dynamic, and security strategies also need to be constantly adjusted. Installing antivirus software is important, but in the end, users are the last line of defense for their assets. When encountering false positives, users should handle it calmly, avoid directly deleting key files, and use appropriate recovery methods. Only by mastering the correct security knowledge can you truly protect your data security.












