Author: Luke, Mars Finance
As night fell in Las Vegas, senior experts in cryptocurrency showed a rare solemnity at a private lunch at the Bitcoin 2025 conference. The air was not filled with the hustle and bustle of decadence, but a deeper worry: quantum computing, a disruptive technology once seen as a distant future, is approaching at an alarming speed, and its cold light has already been cast on Bitcoin's seemingly indestructible encryption barriers. Warnings claim that powerful quantum computers may crack Bitcoin's private keys within a few years, putting about $42 billion worth of Bitcoin at risk, and may even trigger a "liquidation event" that affects the entire market.
This is not an exaggeration. The latest research by Google's quantum artificial intelligence team has added fuel to the fire, pointing out that the quantum resources required to crack the currently widely used RSA encryption algorithm are 20 times lower than previously estimated. Although Bitcoin uses the Elliptic Curve Digital Signature Algorithm (ECDSA) instead of RSA, both face the potential threat of quantum algorithms based on mathematics. Casa co-founder Jameson Lopp's call is still fresh in our ears: "The Bitcoin community needs to reach a consensus and find a way to mitigate the quantum threat before it truly becomes an existential crisis."
How far are we from a future that could be "destroyed" by quantum computing? This is not just a technical issue, but also about trust, wealth and even the fate of an emerging industry.
How does quantum ghost knock on Bitcoin's encryption door?
To understand the threat of quantum computing to Bitcoin, we first need to examine the cornerstone of Bitcoin security - ECDSA. In simple terms, when you create a Bitcoin wallet, a pair of keys is generated: a private key (which you must keep absolutely confidential) and a public key (which can be made public). The public key generates a Bitcoin address through a series of hash operations. When trading, you use your private key to digitally sign the transaction, and other people in the network can use your public key to verify that the signature is indeed from you and that the transaction information has not been tampered with. For classical computers, it is considered mathematically impossible to reverse the private key from the public key, which is the foundation of Bitcoin security.
However, the emergence of quantum computers, especially the Shor algorithm proposed by Peter Shor in 1994, has completely changed this situation. The Shor algorithm can efficiently solve the prime factorization and discrete logarithm problems of large numbers, which is precisely the mathematical basis for the security of public key cryptographic systems such as RSA and ECDSA. Once a sufficiently powerful quantum computer is built and running stably, it can theoretically use the Shor algorithm to quickly calculate the corresponding private key from a known public key.
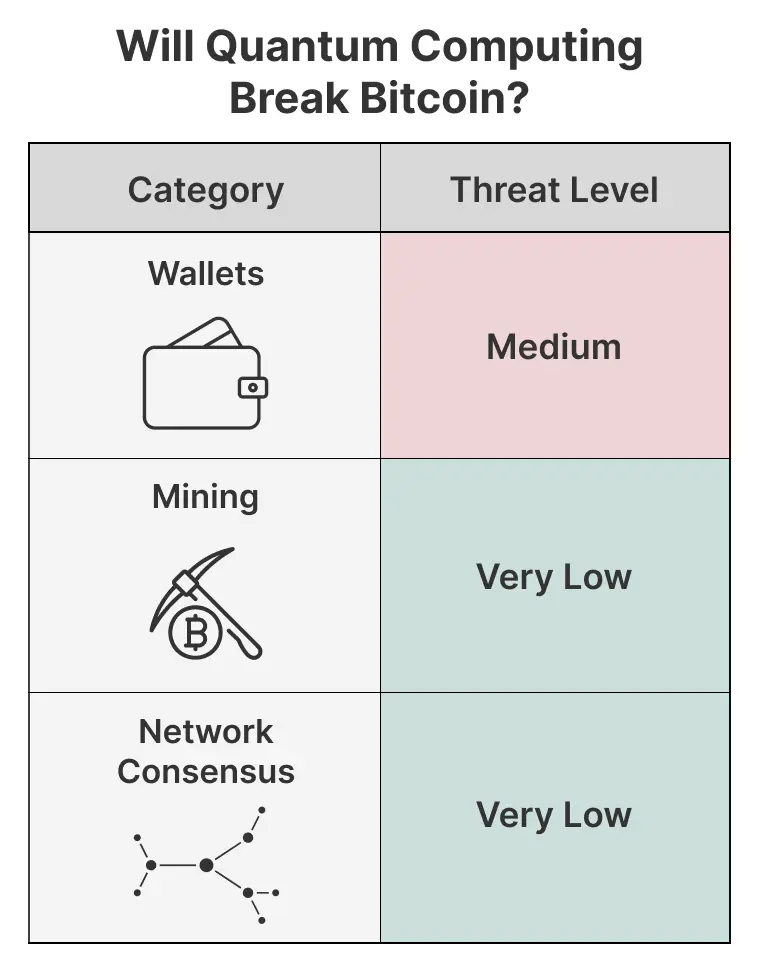
Which bitcoins are exposed to quantum artillery fire first? The first to be affected are those addresses that directly expose the public key. The most typical one is the P2PK (Pay-to-Public-Key) address used in the early days of Bitcoin, where the address itself or related transactions directly disclose the public key. It is estimated that there are still millions of bitcoins (one saying is about 1.9 million to 2 million) sleeping in such addresses, including the early "Genesis" bitcoins that are said to belong to Satoshi Nakamoto. In addition, the more common P2PKH (Pay-to-Public-Key-Hash) address, although the address itself is the hash value of the public key and is relatively safe, once the address has a spending transaction, its public key will be disclosed in the transaction data. If these addresses are reused (that is, transactions are sent from the same address multiple times), their public keys will continue to be exposed and are also at risk. According to earlier analysis by Deloitte and other institutions, the number of bitcoins whose public keys are exposed due to address reuse and other reasons may also be as high as millions. Including the newer Taproot (P2TR) addresses, despite the introduction of technical optimizations such as Schnorr signatures, in some cases the public key or its variants may still be inferred, making it not completely immune to quantum threats.
Taken together, the total amount of Bitcoin deposited in various vulnerable addresses may account for a certain proportion of the total supply of Bitcoin. Earlier estimates (such as 2022) suggest that approximately 4 million to 6 million Bitcoins are at high risk. If roughly calculated based on the current Bitcoin price (for example, assuming $70,000 per Bitcoin), the value of this part of the funds could reach $280 billion to $420 billion. This may be a more reasonable explanation for the "$42 billion" risk warning - it does not refer to an exact number, but a warning that huge wealth is exposed to potential risks.
Even more disturbing is the so-called "Short-Range Attack." When you initiate a Bitcoin transaction, your public key is broadcast to the network along with the transaction information, waiting for miners to package and confirm it. This process usually takes 10 to 60 minutes. If a quantum computer can crack the private key from the broadcast public key within this short time window, it can construct a new transaction and transfer your Bitcoin first with a higher fee. If this attack becomes a reality, almost all types of Bitcoin transactions will be under immediate threat.
The race for quantum hardware: the race from theory to reality
For a long time, building a quantum computer capable of running Shor's algorithm to crack actual cryptographic systems was considered out of reach. However, progress in recent years has been remarkable, especially in improving the quality, quantity, and error correction capabilities of quantum bits (qubits). The key to truly measuring the ability of a quantum computer to crack cryptographic codes is not just the number of physical qubits, but the number and quality of "logical qubits" that can reliably execute complex algorithms.
Craig Gidney, a researcher at Google's quantum artificial intelligence team, pointed out in an updated study in early 2025 that cracking 2048-bit RSA encryption (commonly used in traditional network security) may no longer require the tens of millions of physical qubits previously estimated, but "less than one million noisy qubits" and may be completed in "less than a week". This significant reduction in estimates is due to advances in algorithm optimization and error correction techniques, such as approximate remainder operations, more efficient logical qubit storage, and the application of "magic state" purification techniques. Although Gidney emphasized that such quantum computers still need to meet demanding conditions (such as stable operation for five consecutive days and extremely low gate error rates), far exceeding the current level of technology, it undoubtedly shortens the "quantum security distance" in our perception. As for ECDSA (secp256k1 curve) used by Bitcoin, although there is no equally accurate and widely accepted public data on the specific quantum resources required for cracking compared to the latest estimates of RSA-2048, the general view in the cryptography community is that due to its mathematical structure, it may be easier for quantum computers to break ECDSA than to break RSA.
At the hardware level, several giants are striving to catch up. IBM's quantum roadmap is ambitious. Its "Osprey" processor has reached 433 physical qubits, and "Condor" has reached an experimental 1121 physical qubits. More importantly, IBM focuses on improving the quality and error correction capabilities of qubits. Its "Heron" processor (133 qubits) has become the current development focus due to its lower error rate, and plans to launch a "Kookaburra" system with 1386 physical qubits in 2025, achieving a larger scale through multi-chip connections. Its longer-term goal is to achieve a "Starling" system with 200 high-quality logical qubits in 2029, when it is expected to perform up to 100 million quantum gate operations.
Google is also continuing to make efforts. Its "Willow" chip (allegedly with 105 physical qubits) was unveiled in early 2025. It was described by its team as a "convincing prototype of scalable logical qubits" and has made "below threshold" progress in quantum error correction, which is a key step in achieving fault-tolerant quantum computing.
Quantinuum dropped a bombshell in 2025, announcing that its "Helios" quantum computing system would be commercially available later that year and would be able to support "at least 50 high-fidelity logical qubits." This announcement, if fully realized, would be an important milestone in the transition of quantum computing from experimental research to practical computing capabilities, especially in specific application areas. The company also demonstrated record-breaking logical qubit teleportation fidelity in May 2025, further demonstrating its leading position in building high-quality logical qubits.
Despite this, experts’ predictions remain divided about the time it will take for a fault-tolerant quantum computer to threaten Bitcoin. Some optimistic (or pessimistic, depending on your perspective) estimates suggest it could happen in the next three to five years, while others say it will take at least a decade or more. Importantly, the quantum threat is not an “on/off” mutation, but a process of increasing probability. Every advancement in hardware and every optimization of the algorithm is quietly shortening the countdown.
Bitcoin’s “Quantum Counterattack”: Prepare for a Rainy Day or Make Up for Loss?
Faced with the increasingly clear quantum threat, the Bitcoin community is not helpless. The cryptography community has long begun to study "Post-Quantum Cryptography, PQC", which are new cryptographic algorithms that are believed to be able to resist attacks from known quantum algorithms. After years of screening, the National Institute of Standards and Technology (NIST) has announced the first batch of standardized PQC algorithms, mainly including CRYSTALS-Kyber for key encapsulation, and CRYSTALS-Dilithium, FALCON and SPHINCS+ for digital signatures.
For Bitcoin, hash-based signature schemes (HBS), such as SPHINCS+, are considered a strong competitor because their security does not rely on mathematical problems that have yet to be tested on a large scale (such as lattice cryptography), but is based on the collision resistance of well-studied hash functions. SPHINCS+ is stateless (compared to its predecessors such as XMSS), which is particularly important for the distributed nature of blockchain. However, hash-based signatures usually face challenges such as large signature size, long key generation and verification time, all of which may put pressure on Bitcoin's transaction efficiency and blockchain storage. How to integrate these PQC algorithms without sacrificing Bitcoin's core features is a huge technical challenge.
The greater challenge is how to migrate Bitcoin from the existing ECDSA to the new PQC standard. This is not just a code-level modification, but also involves a fundamental upgrade of the Bitcoin protocol and a smooth transition for millions of users and hundreds of billions of dollars in assets around the world.
The first is the choice of upgrade method: soft fork or hard fork? Soft forks are compatible with old nodes and are generally considered to be less risky, but the freedom to implement complex PQC functions may be limited. Hard forks are incompatible with old rules, and all participants must upgrade, otherwise it will lead to a blockchain split, which is often accompanied by huge controversy and community split risks in the history of Bitcoin.
The second is the migration mechanism. How can users safely transfer their bitcoins stored in the old address (ECDSA) to the new quantum resistant (QR) address? This process needs to be designed to be both safe and convenient, while preventing new attack vectors from appearing during the migration window.
Bitcoin thought leader Jameson Lopp offers a profound insight into this issue in his widely discussed article "Against Allowing Quantum Computers to Recover Bitcoin". He believes that if those with quantum computing power are allowed to "recover" (actually steal) bitcoins that are not protected by PQC, it would be tantamount to a redistribution of wealth for a small number of technological oligarchs, which would seriously undermine the fairness and credibility of Bitcoin. He even proposed a controversial idea: setting a "drop-dead date", after which bitcoins that have not been migrated to QR addresses may be considered "destroyed" or permanently unspendable by the protocol. Lopp admits that this is a difficult trade-off that may result in the loss of assets for some users (especially those addresses that have been dormant for a long time or have lost their private keys) and even trigger a hard fork, but he believes that this is a "bitter medicine" that must be considered to protect the long-term integrity and core value proposition of the Bitcoin network.
Another developer, Agustin Cruz, proposed a specific hard fork proposal called QRAMP (Quantum Resistant Address Migration Protocol). The proposal advocates setting a mandatory migration period, and Bitcoin that has not been migrated after the deadline will also be considered "burned" to "force" the entire ecosystem to quickly transition to a quantum-safe state. Such radical proposals highlight the potential differences in the community's path to responding to quantum threats and the difficulty of reaching consensus under a decentralized governance model.
In addition to upgrading to PQC addresses, continuing to advocate and strengthen the best practice of "not reusing addresses" can also reduce risks to a certain extent, but this is ultimately only a stopgap measure and cannot eradicate the threat of quantum algorithms to ECDSA itself.
Ecological Wandering: Between Inertia and Change
How prepared is the Bitcoin ecosystem to face such a significant systemic risk? Some emerging public chain projects, such as Quantum Resistant Ledger (QRL), have built-in PQC features from the beginning of their design, or projects such as Algorand are also actively exploring PQC integration solutions. They are like light boats, trying to take the lead in the wave of post-quantum cryptography.
However, Bitcoin, a "ton ship", has a huge market value, a broad user base, and deep-rooted decentralization and anti-censorship concepts, making any changes to its core protocol extremely difficult and slow. The developer community is deepening its understanding of quantum threats, and related discussions (such as Lopp's article, the QRAMP proposal, and sporadic discussions on the bitcoin-dev mailing list) are also ongoing, but there seems to be a long way to go before a clear and widely agreed upgrade roadmap is formed. At present, there is a lack of clear public information from mainstream Bitcoin exchanges, wallet service providers, or large mining pools about their PQC transition plans, which reflects from one side that Bitcoin's PQC transformation is still more in the theoretical research and early discussion stage, rather than imminent engineering implementation.
This state puts Bitcoin in a dilemma of being "too big to fail, but too slow to evolve." Its strong network effect and brand recognition are its moats, but in the face of rapid technological innovation, this stability can sometimes turn into a kind of inertia.
"Quantum settlement": much more than just losing the key
What would happen if Bitcoin fails to complete the PQC transition before quantum computers have the ability to actually attack? This is not just a matter of some users losing their Bitcoins.
A large-scale quantum attack could first trigger a "liquidation event" in the market. Once confidence is shaken, panic selling could lead to a catastrophic avalanche in Bitcoin prices. This shock wave would not be limited to Bitcoin itself, but would likely spread to the entire cryptocurrency market, and even have a ripple effect on traditional financial institutions that have large exposures in the crypto space.
The more far-reaching impact is the collapse of trust. The reason why Bitcoin is given the title of "digital gold" is largely due to its so-called "indestructible" encryption security. If this cornerstone is easily broken by quantum computing, then all value narratives and application scenarios built on it will face severe tests. The public's overall trust in digital assets may drop to a freezing point.
Compared with other known Bitcoin security risks (such as 51% attacks, major software vulnerabilities, and increasingly tightened global regulation), the uniqueness of the quantum threat lies in its subversive nature. Although a 51% attack can cause double spending or transaction review, it is difficult to directly steal private keys; software vulnerabilities can be fixed; and regulatory pressure affects compliance and application boundaries more. Once a quantum attack is realized, it will be a "dimensionality reduction attack" on the existing encryption system, directly threatening the ultimate ownership of assets.
Looking back at the history of cryptography, from the upgrade from DES to AES to the gradual abandonment of the SHA-1 hash algorithm, every major cryptographic system migration is a long process that takes years or even decades under the leadership of centralized institutions (such as governments and standard organizations). Although Bitcoin's decentralized governance model gives it strong resilience and anti-censorship capabilities, it may falter when rapid and unified action is needed to respond to global technological changes.
Conclusion: Exploring the way forward in the quantum fog
Quantum computing, the sword of Damocles hanging over Bitcoin, has an unclear time of falling, but the chill of the sword is already palpable. It poses the most profound long-term challenge to the entire cryptography world, especially the cryptocurrency field represented by Bitcoin.
The Bitcoin community is facing an unprecedented test: how to complete an upgrade of the underlying cryptographic system that is vital to its survival while adhering to its core beliefs of decentralization, anti-censorship, and code as law. This is not only a race against the development of quantum computers, but also a complex system engineering of PQC algorithm research, standardization, Bitcoin protocol innovation, community consensus cohesion, and coordinated migration of the global ecosystem.
The road ahead is full of uncertainty. Will it successfully evolve, turn quantum threats into a catalyst for technological innovation, and enter a safer post-quantum era? Or will it eventually fade in the dawn of quantum computing due to the difficulty of consensus and migration? As the wheel of history rolls forward, the answer may be hidden in every decision, every code submission, and every fierce debate in the Bitcoin community in the next few years. This is destined to be an unfinished story about innovation, risk, and tenacity, and each of us, whether participants or observers, is on the eve of this magnificent change.







