
In the Bitcoin Core software library, a proposal was recently made to remove the policy limit on the size of OP_Return outputs . We have already expressed our opinion on this issue. This move has caused some controversy and reignited the debate on what constitutes spam on the Bitcoin blockchain and how to deal with it. In this article, we look back at the incident ten years ago, in the summer of 2015, when the Bitcoin network was attacked by spam transactions. Our goal is to compare what happened then with what is happening now and explore what lessons have been learned at the time.
The spam attack in the summer of 2015 was an early confrontation in the block size debate . The attackers were "big blockers" who wanted to increase the block size limit. At the time, one of the main arguments of the big blockers was that the 1MB limit was too small and that blocks could easily be filled with spam transactions for relatively little money. This block filling situation was seen by the big blockers as an extremely bad outcome, representing a victory for spammers. In the eyes of the big blockers, block filling would make it unreliable to use Bitcoin for payments. The big blockers wanted to increase the block size limit to make it more expensive for spammers to fill all the space in the block. The logic was that, at a fixed fee rate, it would cost more to fill an 8MB block with spam transactions than to fill a 1MB block.
The “small blockers” counter to this argument is that the big blockers’ thinking is backwards, and if there is junk, getting it all on the chain quickly and cheaply does not stop the junk sender, but rather allows the junk sender to win. Furthermore, if the block size limit is increased, fees will go down, making junk transactions cheaper. However, for big blockers, a key metric is how much it costs to fill a block. They believe this number is too low for Bitcoin’s security, and that raising the block size limit will help increase this number, making Bitcoin more resilient.
Spam attack
First round
On June 20, 2015, a little-known Bitcoin wallet provider and exchange, CoinWallet.eu, which claims to be based in London, announced on BitcoinTalk and Reddit that it was conducting a "Bitcoin stress test." We were unable to find much information about this entity, such as who its management team or shareholders are. We were unable to find any meaningful WHOIS records or corporate registration documents, and its London address (78 York Street) appears to be a dummy address .

78 York Street in London (Google Street View)
However, the attackers, CoinWallet.EU , made their motive clear: to justify increasing the block size limit.
Bitcoin is on the brink of collapse, yet core developers are entangled in petty arguments and failing to make necessary changes for long-term sustainability. If nothing is done, Bitcoin will remain nothing more than an expensive science project. By stress-testing the system, we hope to make a clear case for increasing the block size by demonstrating how easy it is to attack the network with large-scale spam transactions.
The attackers explained that they would "generate 1MB of transaction data every 5 minutes". The attack was scheduled for June 22, 2015. The plan was that "the transaction backlog would reach approximately 241 blocks, or 1.67 days". This would be a transaction backlog of over 241MB.
At the time, Luke-Jr responded to the attackers on Reddit, stating:
Bitcoin has miner and block size limits precisely to combat this type of attack.
Source: https://www.reddit.com/r/Bitcoin/comments/3agk61/comment/cscgipz/
On June 24, 2015, the attackers announced that the attack was not as successful as they had expected, as their servers began to crash after about 2 hours, after the mempool size reached about 12MB. The attackers stated that "Bitcoind is not well suited to handle transactions of this size". The attackers also revealed that they spent about 2 Bitcoins or 434 Euros in fees on this failed attack.
Round 2
On the same day, June 24, 2015, CoinWallet.EU announced that the second spam attack would take place on June 29, 2015. Again, the goal was to push the mempool backlog to 241MB.
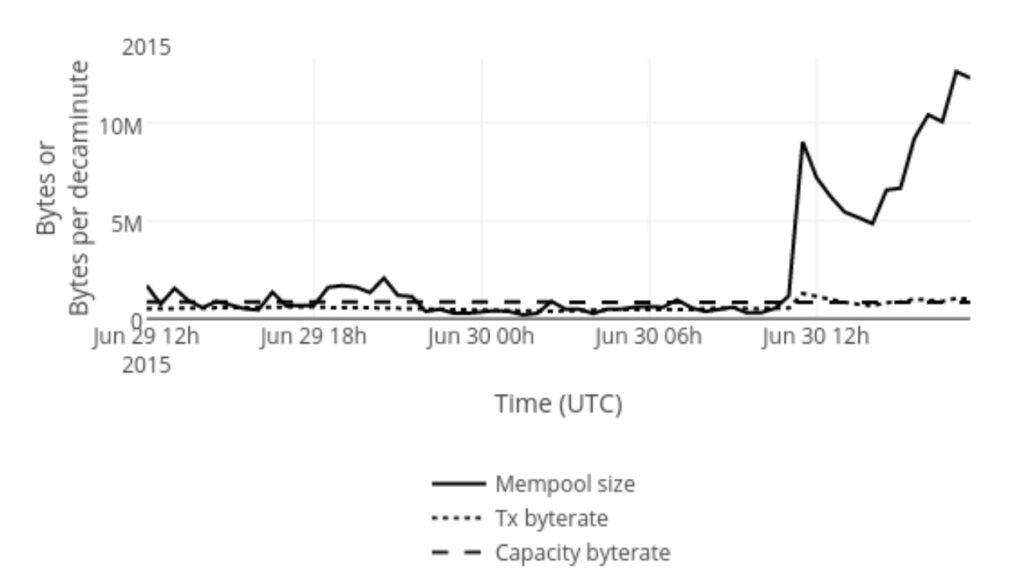
As shown in the chart above, the attack appears to be more effective this time, with some users apparently agreeing with big block proponents that it makes Bitcoin unusable.
Can someone explain to me what is going on? I bought 0.05 BTC through a local web exchange and they sent it to my wallet with a transaction fee of 0.0001. The transaction was 226 bytes. After waiting for confirmation for 7 hours, it was rejected by the blockchain.info node. The exchange sent it to me again with a transaction fee of 0.0002. The status shows that the estimated confirmation time is "very fast" (high priority). But it has been waiting for 6 hours now! What on earth did you do with BTC? ! Is this normal? BTC will not be able to be used for daily transactions in this way. Isn't a transaction of 226 bytes and a transaction fee of 0.0002 enough?
Source: https://bitcointalk.org/index.php?topic=1098263.msg11847265#msg11847265
Luke-Jr’s mining pool, Eligius, appears to have successfully filtered out the spam at the time. During the attack, the blocks produced by the Eligius mining pool were much smaller than other mining pools, which were usually 1MB or 750KB, regardless of what limits were set.
Luke’s earlier predictions were correct, and the block size limit and miners helped mitigate the impact of the attack. But this was not true for all miners, only his own pool. In our opinion, the block size limit played a more powerful role in preventing spam transactions from being put on the chain. Luke’s spam transaction filtering policy at the time caused controversy. Some people believed that Luke’s “blacklist” harmed Bitcoin’s fungibility and prolonged the attack by keeping the memory pool bloated for longer. For example, the operator of the Kano mining pool made the following argument about spam transactions on the BitcoinTalk forum:
The simple fact is that they are valid transactions with fees.
Another forum member, wizkid057, Luke’s colleague at Eligius, defended the filtering, just as Luke’s colleagues at Ocean Pool supported the filtering stance today:
The only thing that prolonged the attack was that the attacker and other pools/miners did not filter out the scammers' spam transactions. Other pools/miners would rather fill their blocks with the attacker's transactions to get an extra 0.1 BTC in fees than protect the entire Bitcoin... or maybe it's just laziness. In any case, any ill effects of this attack could easily be offset by 100% with the participation of just a few large mining pools. Source: https://bitcointalk.org/index.php?topic=1098263.msg11760038#msg11760038
We understand that wizkid057 is working with Luke at Ocean Mining Pool today. Another user on the BitcoinTalk forum, “spartacusrex”, agreed with Kano, saying:
A valid transaction is a valid transaction. Period. End of story. No politics. If anyone starts suggesting that it is possible to "edit" which transactions can go through the system, I think that would set a very bad precedent.
Round 3
On July 7, 2015, a third wave of attacks took place. However, as far as we know, this time CoinWallet.EU did not make an official announcement, although due to their previous behavior, they remain the prime suspect, and possibly others associated with them. In the following days, people reported between 27,000 and 80,000 transactions in their mempools. This was by far the most violent and multifaceted attack, causing a certain amount of chaos on the network.
Motherboard reported that the attack cost more than $8,000 (30 bitcoins) in fees, much higher than the 434 euros in the previous attack. This time the attackers used more diverse strategies to generate as many junk transactions as possible. For example, many dust transactions were sent to public wallets such as the WikiLeaks wallet and the wallet of the startup Reddit competitor Voat.
The spammers also sent small amounts of Bitcoin to addresses whose private keys were publicly known, such as brainwallets generated by the words "cat" or "dog." This facilitated the creation of more spam transactions because other users could create more spam transactions to try to redeem the funds without the attacker's server having to create these transactions themselves. For example, in July 2015, a Bitcoin address generated by the word "cat" using an uncompressed key had over 41,000 transactions associated with it. The address received thousands of outputs, each worth 0.00001 BTC. In July 2015, a Bitcoin address generated by the word "password" using an uncompressed key had over 45,000 transactions associated with it. An address generated by the word "dog" had over 43,000 transactions. Thus, the spammers clearly demonstrated ingenuity and expertise in carrying out this attack.
At the height of the attack, Bitcoin developer and large block advocate Mike Hearn argued that increasing the block size limit was the best defense against such attacks.
The best defense against this attack is to make it as costly as possible by increasing the block size limit. This is certainly what I am working on.
Source: https://www.reddit.com/r/Bitcoin/comments/3ck5z9/comment/cswda6x/
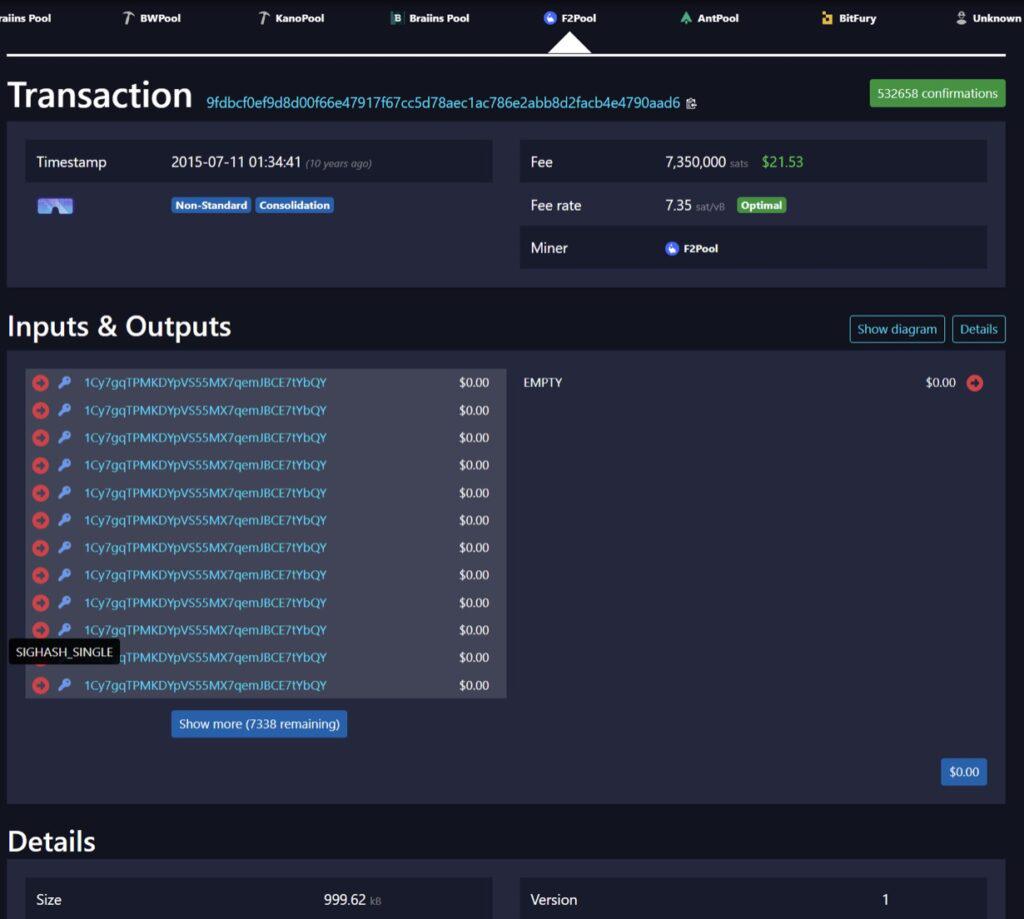
Mining pool F2Pool helped clean up the mess by creating a 1MB transaction to consolidate these junk transaction outputs, thereby reducing UTXO bloat. This 1MB transaction contained over 5,000 inputs and was computationally challenging to verify, taking nodes up to 20 seconds to check it due to quadratic scaling weaknesses in the sighash operation in Bitcoin at the time. A few days later, Bitcoin developer Gregory Maxwell reportedly helped F2Pool use the same signature for each input, making transactions easier to verify. For example, this is another 1MB transaction , containing over 7,000 inputs. More precisely, the first input has a unique signature that signs the hash of the transaction, while all other inputs have the same signature and do not sign the hash of the transaction. With Gregory's more efficient consolidation, each input is signed with SIGHASH_SINGLE instead of SIGHASH_ALL. SIGHASH_ALL means that the signature signs all inputs and outputs, which is the default behavior. This distinction is now nicely reflected on the mempool.space website, a great new feature added in May 2025, with SIGHASH_ALL denoted by a green key and SIGHASH_SINGLE by a blue key.
Round 4
CoinWallet then underwent a fourth and final round of stress testing, this time in September 2015 .
There are many opposing views on the stress test announced tomorrow. Some call it an attack on the network, however we see it as no different to someone buying all the tickets on a train to have exclusive access to the entire train. We have consulted with multiple lawyers and the general consensus is that such a test does not violate any law in the EU or elsewhere.
A person claiming to be “James Wilson”, the Chief Operating Officer (COO) or Chief Commercial Officer (CCO) of CoinWallet.EU , sent electronic transactions to the respective media outlets to talk about the attack. Wilson said:
The goal is for the community to fix Bitcoin. It's broken right now. A small wallet startup shouldn't be able to bring the network to its knees.
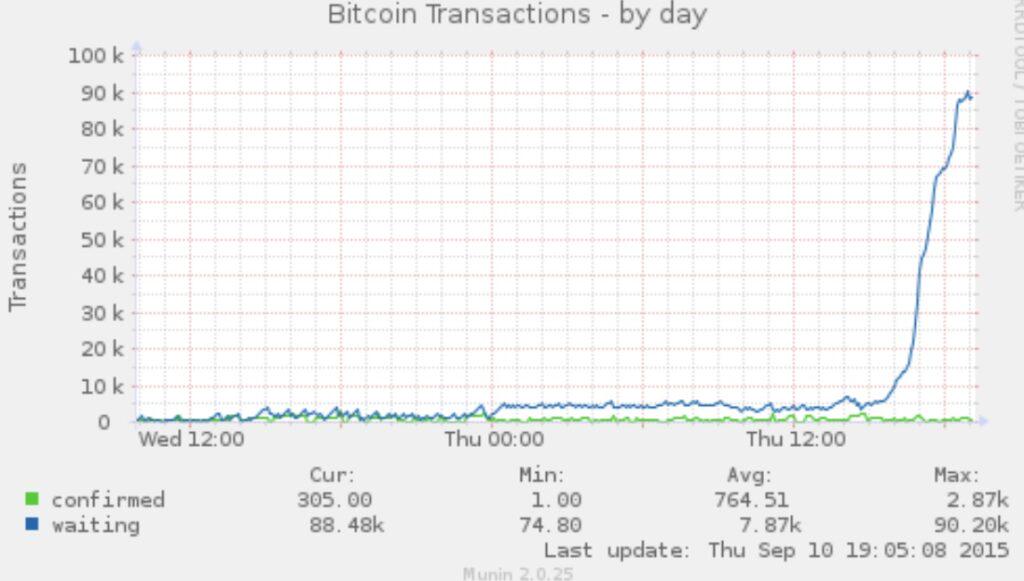
In this fourth attack, CoinWallet.EU took a different approach. The company announced that it would give away 200 Bitcoins by posting private keys directly to the BitcoinTalk forum. The original post contained 5 private keys, each with a balance of 0.53918 BTC. In the following days, the Coinwallet account posted thousands of private keys with balances in the post. This resulted in more than 90,000 transactions being generated, many of which were conflicting transactions and could therefore be discarded using the First Seen Safe (FSS) principle. This made the impact of the fourth round of attacks less severe than the third round.
With this latest attempt, the company announced that their “stress testing day is officially over,” with many Bitcoin holders declaring victory.
As for who is behind CoinWallet.EU, it remains a mystery. Speculations include the following:
- Former Quadriga CEO Gerald Cotton may be behind CoinWallet, as when customers send money to CoinWallet, they are told to set the recipient to 1009926 BC LTD , which is the same name as Quadriga. However, this may simply be CoinWallet using Quadriga as a payment processor.
- CoinWallet COO James Wilson may be the same person as former Craig Wright colleague Jamie Wilson, which means Wright may have been involved in the spam attack. Alternatively, he could be another fake Satoshi, Phil James Wilson (aka Scronty ) , who once said that his family often called him James Wilson. (James Wilson is a fairly common name)
For us, the above theories are too weak and there is not enough evidence to conclude at this stage that CoinWallet is behind this.
Academic Analysis
An academic paper was published covering the spam attack of 2015. The published data showed two major spikes in the size of the mempool, reaching around 175,000 transactions, which coincided with the third and fourth rounds of the spam attack.
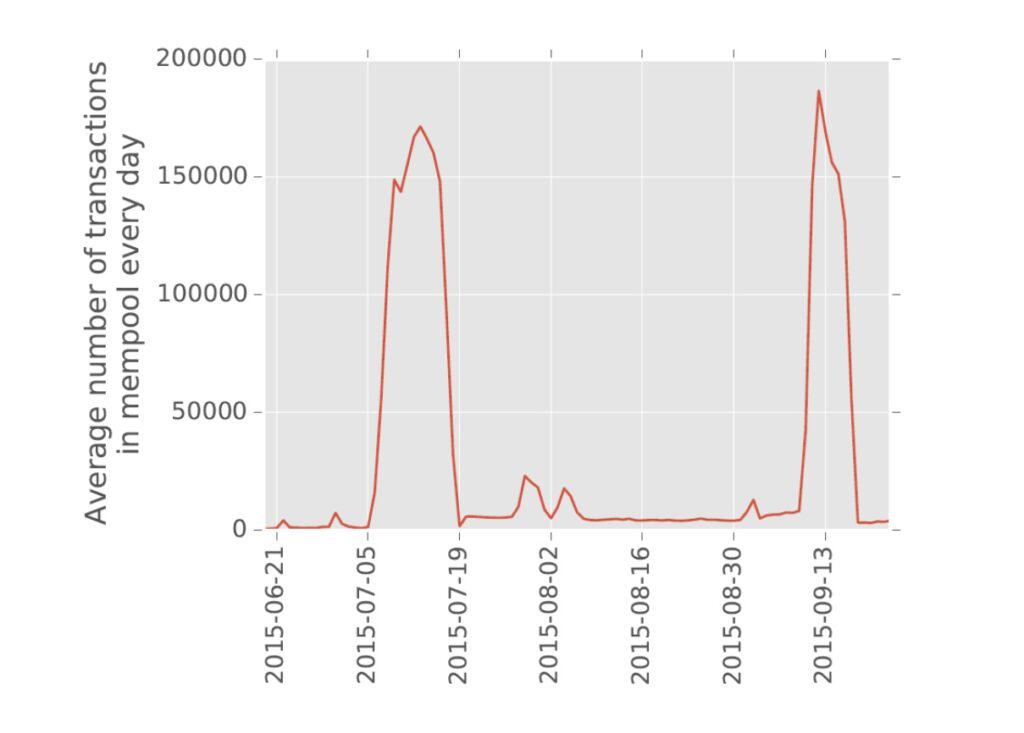
The paper finally draws the following conclusions:
We empirically investigate a spam-based "stress test" DoS attack on Bitcoin. Using our clustering-based approach, we find that 385,256 (23.41%) of a total of 1,645,667 Bitcoin transactions were spam during the 10-day peak of spam activity. We also show that the attack negatively impacted non-spam transactions, increasing average fees by 51% (from 45 to 68 satoshis/byte) and processing latency by 7x (from 0.33 to 2.67 hours). This suggests that an adversary willing to spend a small amount of Bitcoin (at least $49,000) to pay higher fees could perform a DoS attack on Bitcoin.
in conclusion
In our opinion, the 2015 spam attack had a considerable impact on Bitcoin. Not only did it have a technical impact on Bitcoin’s relay strategy , but it was also an influential series of events that helped shape people’s perception of spam on Bitcoin. Possibly as a result of these attacks, the network underwent the following changes:
- Miners increase their block size limit policy from 250KB or 750KB to 1MB. 1MB is the consensus limit and miners change their policy from the default to 1MB. This is an example of a miner changing their policy limit to comply with consensus rules. The idea here is that this will increase block capacity and make it harder for spam attackers to fill blocks and hurt the user experience.
- In October 2015, the minimum relay fee in Bitcoin Core was increased fivefold to 5,000 sathoshis . This decision was likely made to help combat spam.
- The spam attack also appears to have prompted the introduction of mempool limits and a default mempool size limit of 300MB in Bitcoin Core. Most of the discussion took place in October 2015 .
- The spam attack also appears to have heightened tension and polarization in the block size limit debate. Big blockers, some of whom participated in the attack, cited the degradation in user experience during the attack as evidence that the block size limit should be increased. Some big blockers seemed pleased that the attack pushed the block size limit to the top of the agenda and served as a catalyst for further debate. A skeptic could even say that this was a coordinated and deliberate attempt to gain more grassroots user support for increasing the block size limit. However, small blockers remained steadfast and held their ground.
Of course, the small block proponents won the war. Blocks became full, and this is now the norm. It is now a settled issue that increasing the block size limit to allow more junk transactions on-chain was not a good idea. However, the debate continues as to what constitutes junk transactions and how to deal with it from a relay and mining strategy perspective. For those who did not live through 2015, one of the main takeaways from this article may be that junk transaction attacks are not new. If anything, in our opinion, the malicious intent of the attackers in 2015 was probably more clear than the more ambiguous and perhaps more legitimate intent of those behind the generation of JPEG-related transactions in 2023 and beyond. Another interesting comparison is the amount of fees spent, which in 2015 was probably around $10,000 to cause damage. Since 2023, hundreds of millions of dollars have been spent on fees for “junk” transactions.







