Author: 23pds & Thinking
Editor: Sherry
background
Yesterday, when I was sorting out materials related to APT attacks, Brother Shan (@im23pds) suddenly came to my workstation excitedly and said, "Thinking, I found an interesting project. CZ is used frequently. We may be able to say hi to CZ at 0 cost." So we quickly drafted several possible vulnerability points:
- Hijack CZ's account on ReachMe;
- Change CZ's settings in ReachMe;
- Send CZ a message for free, bypassing the 1 BNB limit for sending him a message.
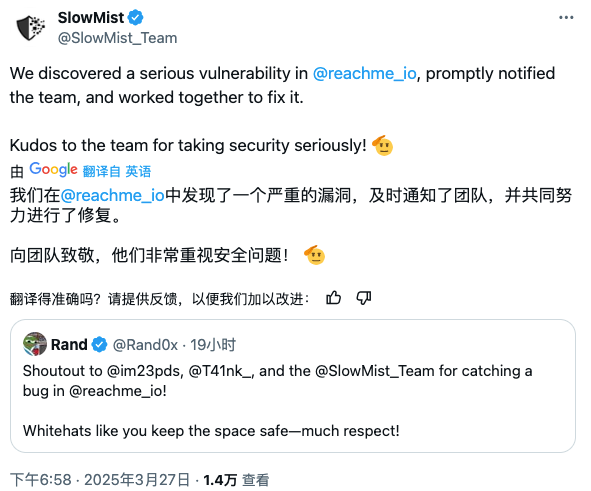
About 10 minutes later, we found a vulnerability that allowed us to say hi to any user at low cost on ReachMe.io, so we immediately contacted the project team and provided details of the vulnerability verification. The project team also quickly fixed the vulnerability and contacted us for retesting. I like the ReachMe team's serious and rigorous attitude towards security issues!
(https://x.com/SlowMist_Team/status/1905212712956665896)
In addition, the SlowMist Security Team is honored to receive thanks from CZ and the ReachMe project team.
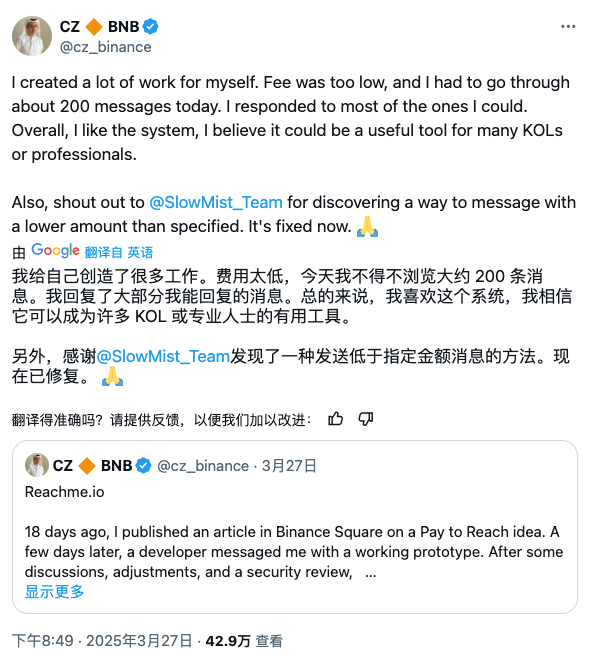
(https://x.com/cz_binance/status/1905240886986039437)
Discovery Process
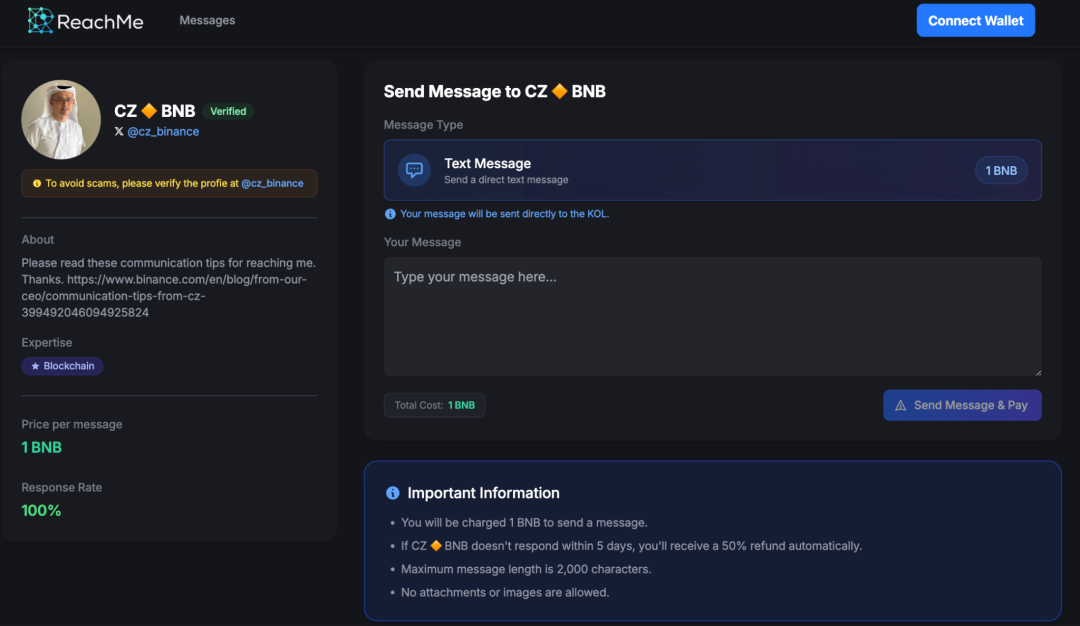
ReachMe.io is a paid chat platform based on BNB Chain, which aims to connect KOLs (key opinion leaders) and fans through cryptocurrency payment mechanisms. Users need to pay BNB to send private messages to KOLs, and KOLs can get 90% of the fees (the platform takes 10%); if the KOL does not reply within 5 days, the user can get a 50% refund.
On March 27, 2025, Binance founder CZ changed the profile of his X account to: "DM: https://reachme.io/@cz_binance (fees go to charity)", which means "DM me on ReachMe, the fees will go to charity."
We can see that the cost of Say Hi to CZ is 1 BNB, so we thought of some solutions and tried to see how to bypass the limit of 1 BNB to Say Hi to CZ.
After some research with Shan Ge, we found that when ReachMe sends a message to any KOL, it will generate a summary of the message through the "/api/kol/message" interface, which includes the "_id" field. This field is attached to the on-chain contract Function: deposit(string _identifier,address _kolAddress) when sending a message, and corresponds to the _identifier field.
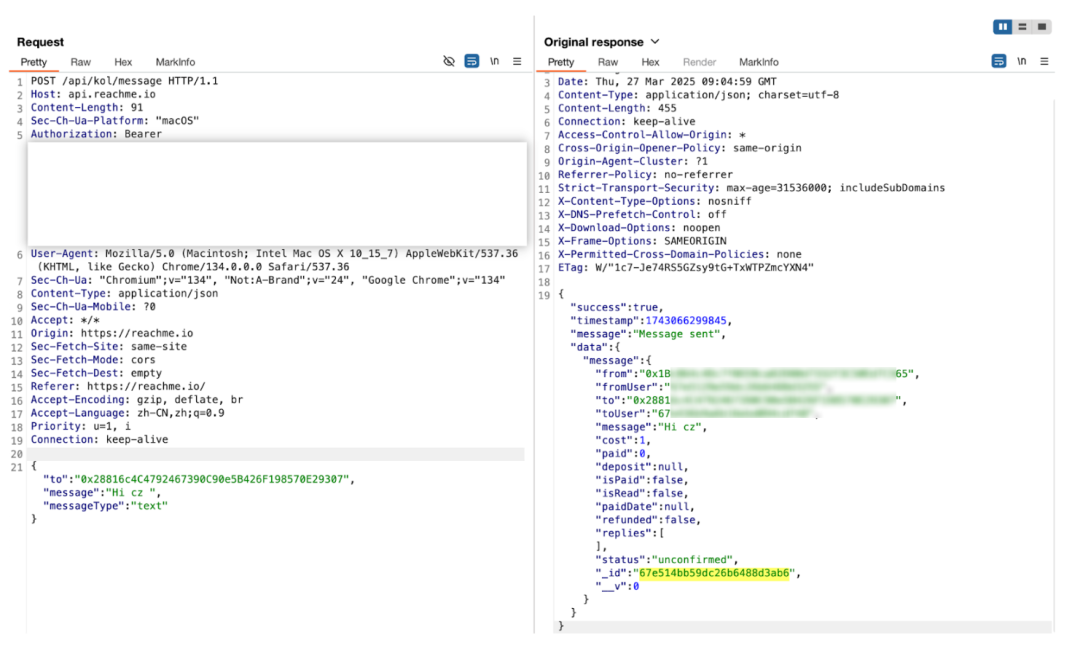
And the BNB attached to the message sent to the KOL is actually the amount of BNB attached to the call to the contract Function: deposit. So we constructed a transaction and sent the "_identifier" corresponding to the "Hi CZ" message and CZ's address, along with 0.01 BNB (only 0.001 BNB is required as a minimum) to the contract.
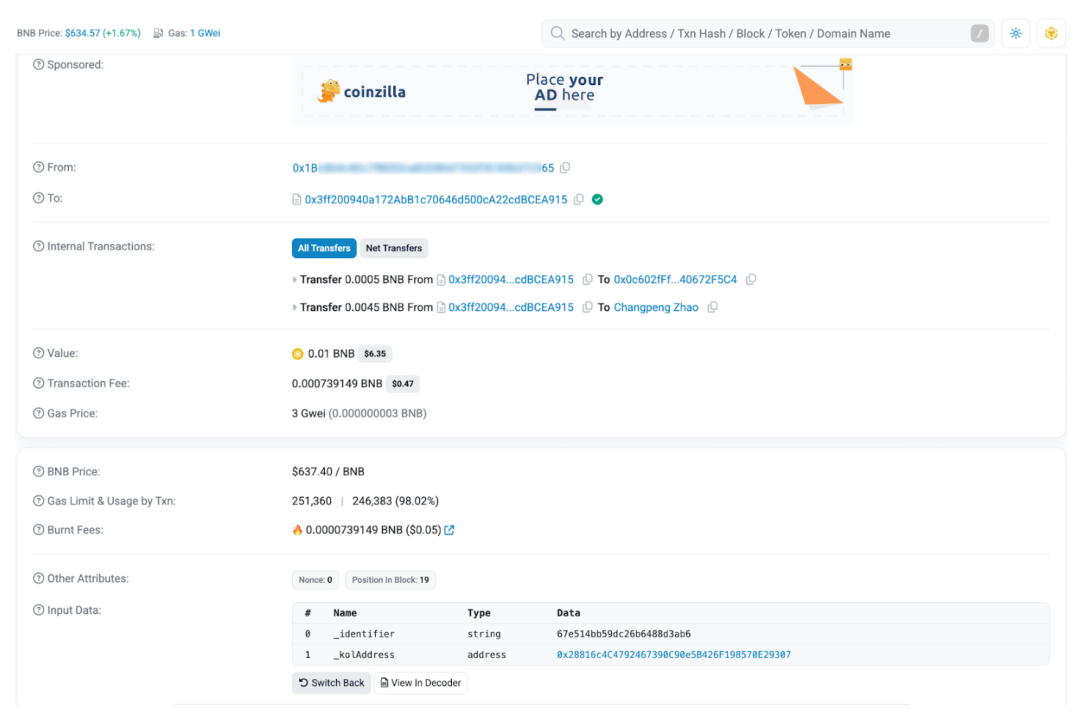
Since ReachMe did not put the KOL's preset message sending cost into the contract for testing at the beginning of its design (perhaps to facilitate KOL to adjust the message price at any time and save gas fees?), the 1 BNB limit can be bypassed by modifying the front-end code, modifying the network response package, or directly interacting with the contract. This is because the server also omits the check of the message price and the number of BNB in the on-chain transaction when retrieving the on-chain transaction.
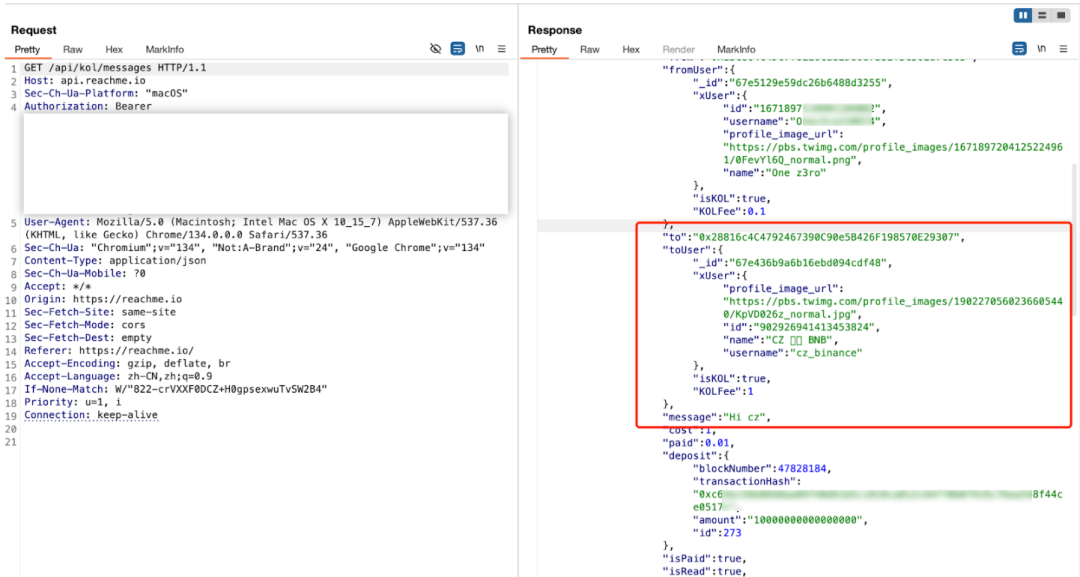
So it took us about 10 minutes to successfully bypass the rule that it costs 1 BNB to talk to CZ, and it only cost 0.01 BNB to say hi to CZ.
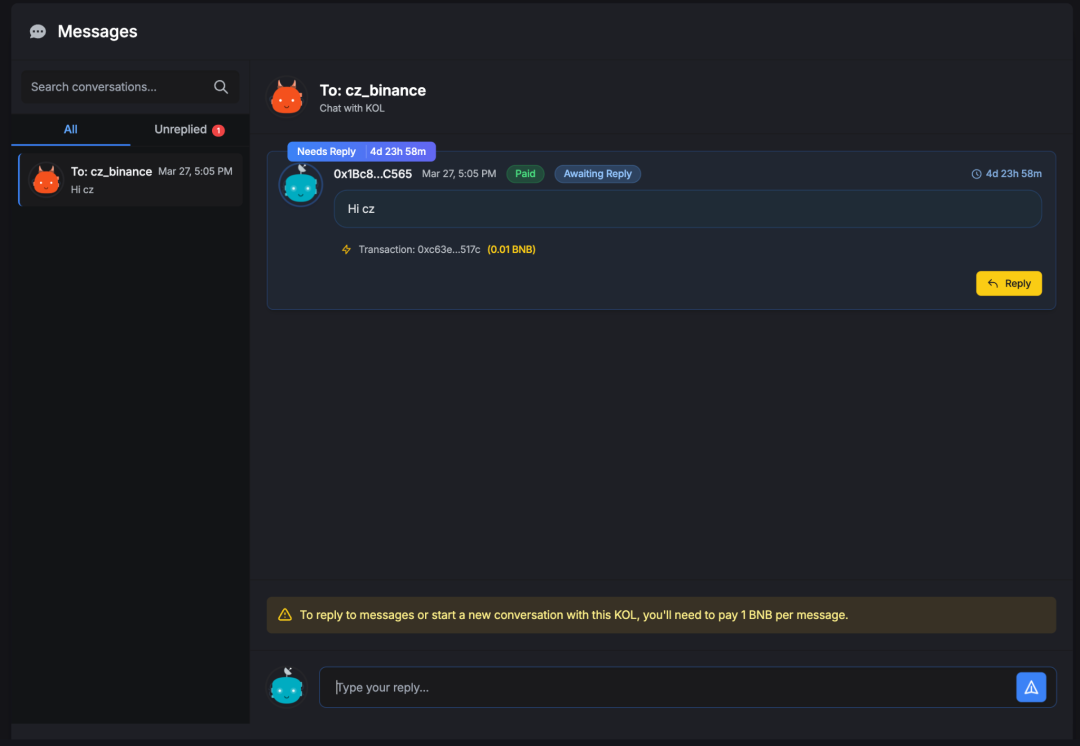
In addition, it is worth noting that there are actually further uses, such as: sending interesting messages to CZ, and conducting spear phishing? In view of the great influence of CZ himself, this part of the test was abandoned later. Everyone should pay more attention to safety and beware of phishing.
Summarize
This type of product design that combines centralization and decentralization often results in inconsistent security checks on and off the chain. Therefore, attackers can bypass certain inspection restrictions by analyzing the interaction process between the chain and the chain. The SlowMist security team recommends that project parties synchronize necessary security check items in the on-chain and off-chain codes as much as possible to avoid the possibility of being bypassed. At the same time, it is recommended to hire a professional security team to conduct security audits to discover potential security risks and prevent them.













