
The monthly security event highlights of Zero Hour Technology have begun! According to statistics from some blockchain security risk monitoring platforms, there were more than 60 cryptocurrency hacking incidents in the first quarter of 2025, with a total loss of US$ 1.629 billion , a year-on-year increase of 131% compared with US$ 706 million in the first quarter of 2024. There were 20 cryptocurrency hacking attacks in March, with more than US$ 38.71 million in stolen funds. However, the total loss has decreased due to the successful recovery of part of the stolen funds (about 90%) by the decentralized exchange aggregator 1inch.
Hacker attacks
7 typical safety incidents
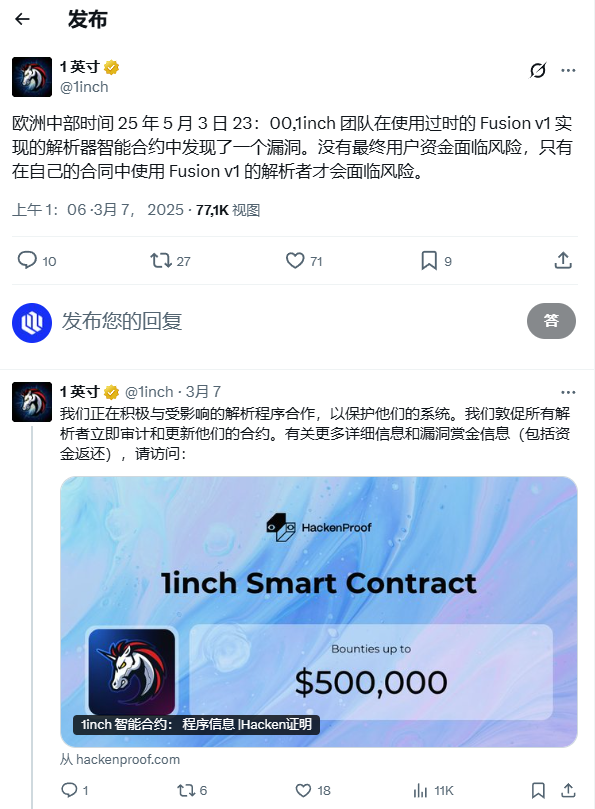
(1) On March 7, the 1inch team discovered a vulnerability in its old version of the Fusion v1 parser smart contract. According to the analysis of the SlowMist security team, the incident caused a loss of approximately 2.4 million USDC and 1,276 WETH, totaling more than 5 million US dollars.
Officials confirmed that this vulnerability does not affect end-user funds, and the only affected object is the parser contract using Fusion v1. 1inch has taken measures and is continuing to follow up on the security situation. Currently, 90% of the funds have been recovered.
(2) On March 13, Cointelegraph reported that in the past few days, at least three crypto project founders reported that they had successfully thwarted suspected North Korean hackers' attempts to steal sensitive data through fake Zoom calls. On March 11, Nick Bax, a member of the white hat hacker group "Security Alliance", posted a warning on the X platform that North Korean scammers have used this method to steal millions of dollars from victims. In addition, earlier today, blockchain security company CertiK said that after a series of high-profile hacker attacks, it was found that the Lazarus Group was using mixers to transfer crypto assets, and it had detected that 400 Ethereum, worth about $750,000, had been deposited into the Tornado Cash mixer service.
(3) On March 14, the Zero Hour Technology Security Team monitored an attack on the BNB Smart Chain project H2O. The main cause of this vulnerability was that when the H20 Token contract designed the economic model of buying from PancakeSwap Pair, it did not consider that skim could also achieve the same purpose when modifying the ERC20 transfer function, resulting in the attacker using skim to obtain a large amount of incentives out of thin air. This attack caused a total loss of 22,000 USD.
Zero Hour Technology || Analysis of the H2O attack
(4) On March 17, Wemix Foundation, a blockchain subsidiary of Wemade, disclosed that it had lost approximately 8.65 million WEMIX tokens (worth approximately $6.22 million) due to a hacker attack. Its CEO Kim Seok-hwan said that the hacker was unlikely to be the North Korean organization Lazarus Group, but a professional who infiltrated the system by stealing the service monitoring authentication key of the NFT platform Nile. It is reported that the hacker prepared for this attack for two months and then made 15 withdrawal attempts by creating abnormal transactions, 13 of which were successful. Kim Seok-hwan also revealed that it plans to reopen all services of Wemix on Friday and will upgrade security measures on the new blockchain infrastructure.
(5) On March 18, according to the monitoring of the Zero Hour Technology Security Team, the Four.meme platform was attacked by hackers. Four.meme is a memecoin launchpad incubated by Binance Academy that is similar to pump.fun. The loss from this attack was approximately USD 180,000.
Zero Hour Technology || Analysis of the Four.meme attack
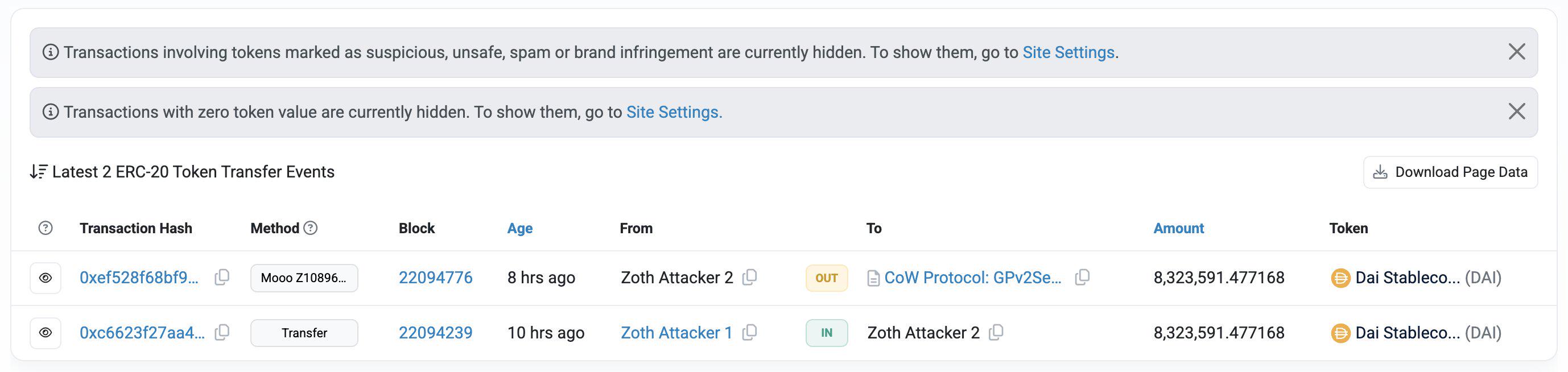
(6) On March 22, the RWA project Zoth released a theft update stating that the team is actively investigating the theft and working with professional experts to track the stolen funds and recover them. In addition, Zoth has partnered with Crystal Blockchain BV to fully investigate the incident. 73% of the Zoth platform's TVL (total locked value) has been immediately secured with the help of the asset issuer. A detailed report will be shared in a few weeks. Zoth announced that it has set up a public bounty of $500,000. Any actionable clues that help recover the funds will be rewarded from the bounty. Previously, Zoth confirmed that it had suffered a security vulnerability attack and the Zoth attacker had exchanged the stolen funds for 4,223 ETH.
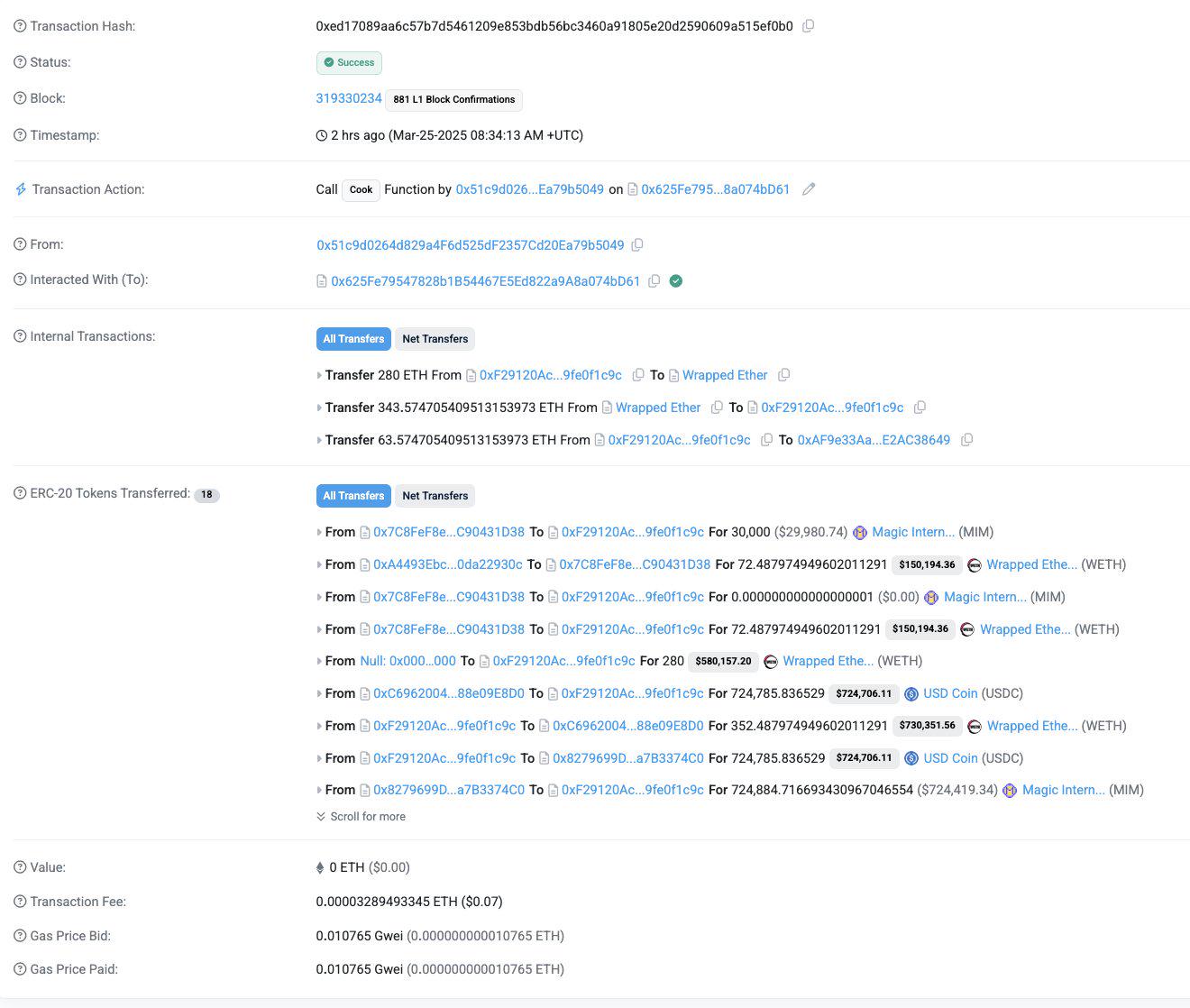
(7) On March 25, Abracadabra officially confirmed that its gmCauldrons product was hacked yesterday, resulting in a loss of approximately 13 million MIM (approximately 6,000 ETH). The DAO Treasury has urgently used part of its assets to repurchase 6.5 million MIM, accounting for 50% of the total loss. The remaining part will be gradually absorbed in the coming months and is expected to be fully repaid by mid-2025. The team is working with security agencies such as Chainalysis to track the whereabouts of the funds. The hacker's related addresses have been made public and it is willing to negotiate with the attacker to return the funds for the bug bounty. Previously, the GMX and MIM_Spell related contracts had been hacked, resulting in a loss of approximately US$13 million.
Rug Pull / Phishing Scam
3 typical safety incidents
(1) On March 12, the address 0xa4C1...683f suffered a phishing attack, resulting in a loss of approximately $1.82 million.
(2) On March 19, aixbt suffered a phishing attack and lost 55.5 ETH. The dashboard has been suspended for security upgrades.
(3) On March 24, a user lost $329,743 in assets due to a phishing authorization signed 408 days ago.
Summarize
In March, the largest losses were caused by code vulnerabilities, exceeding $14 million; wallet hacks resulted in the theft of more than $8 million. The most serious loss in March was the exploitation of a smart contract vulnerability in the decentralized lending protocol Abracadabra.money on March 25, resulting in a loss of approximately $13 million.
The Zero Hour Technology Security Team recommends that project parties prioritize multiple audits and real-time monitoring of smart contract vulnerabilities, strictly adopt multi-signature wallets and hardware isolation solutions to manage assets, and clean up unnecessary authorizations; at the same time, establish a rapid response mechanism, preset emergency pause functions and regularly conduct attack and defense drills, configure on-chain insurance and emergency funding pools; in addition, security health assessments should be conducted every quarter, and audit reports should be NFT-ed to ensure transparency and verifiability.













