On the evening of February 21, 2025, Beijing time, the crypto world ushered in a security crisis that shocked the world. The centralized trading platform Bybit suffered a carefully planned attack, resulting in the theft of assets worth $1.46 billion. This not only set a record for the largest single loss in the crypto field, but also surpassed the $1 billion theft of the Central Bank of Iraq in 2003, becoming the largest theft in global financial history.
In the face of this crisis, Bybit took a series of emergency measures: giving priority to retail investors to withdraw money, restricting institutional customers to withdraw money in a graded manner, and relying on the liquidity support of exchanges such as Bitget and OTC service providers. In just 12 hours, Bybit restored the full withdrawal function and avoided a possible run. On February 24, Bybit CEO Ben Zhou issued an announcement that the ETH deficit had been fully compensated, but what really shocked the industry was that the cold wallet defense line that was considered "unbreakable" was actually breached.
This security incident not only broke the myth that cold wallets are absolutely safe, but also sounded the alarm for the entire cryptocurrency industry: even the most advanced technical defenses cannot completely resist social engineering attacks carefully designed to target human weaknesses. When it was confirmed that the attack came from the notorious North Korean hacker group Lazarus Group, the situation became more complicated - the possibility of recovering the stolen funds was very slim.
So, how do exchanges store user assets? Why are cold wallets considered the "ultimate line of defense"? And how did the attackers break through this line of defense? Let's take a deeper look at the technical details and security risks behind this unprecedented digital asset theft.

Two lines of defense for digital vaults: asset storage on exchanges
Crypto asset storage basics:
Hot Wallets and Cold Wallets
The way cryptocurrency exchanges store funds can be compared to the deposit management of traditional banks. Banks have to deal with a large number of customers' deposit and withdrawal needs every day. They will prepare a certain amount of cash at the counter (equivalent to "liquidity"), but most of the money will be kept in the vault (equivalent to "reserve"). The operation of crypto trading platforms also follows a similar idea.
Exchanges store users' cryptocurrencies in two parts: one part in a "hot wallet" and the other in a "cold wallet". A hot wallet is like a bank counter, directly connected to the Internet, allowing users to quickly access and trade. Exchanges keep about 5-10% of their funds in hot wallets to meet users' daily trading needs. But because hot wallets are always online, they are like leaving money on the side of the road, making them a prime target for hackers. Attackers usually attack hot wallets through phishing attacks, malware, and other means. For example, in 2019, 7,000 BTC were stolen from Binance's hot wallet due to an API key leak.
Most of the funds (usually 90-95%) are stored in cold wallets. Cold wallets are like underground vaults in banks, completely isolated from the Internet, and the withdrawal of funds requires strict multiple verifications and approvals. To use the funds in the cold wallet, multiple administrators must verify them, just like the door of the vault requires multiple keys to open. It is this physical isolation and multiple authentication security measures that make cold wallets considered the safest storage method.
Are cold wallets 100% safe?
Although cold wallets are considered the safest way to store money, absolute security does not exist. Just like a safe, although it is strong, it can still be breached, cold wallets also have their weaknesses. These risks mainly come from three aspects:
Human factors: If the person responsible for managing the cold wallet is successfully phished or socially engineered, the attacker may be able to access the cold wallet by obtaining the administrator's credentials or information.
Technical vulnerabilities: If the device used to sign the transaction is implanted with a Trojan horse, or is hijacked by hackers when connecting to the network for transfer, the funds will also be at risk.
Failure of multi-signature mechanism: In theory, multi-signature (multi-sig) requires multiple key holders to approve a transaction, but if an attacker is able to deceive every signer, or control a sufficient number of keys required for the multi-signature threshold, the security mechanism will be bypassed.
Bybit hack: Analysis of social engineering attack methods
How was the Bybit cold wallet hacked?
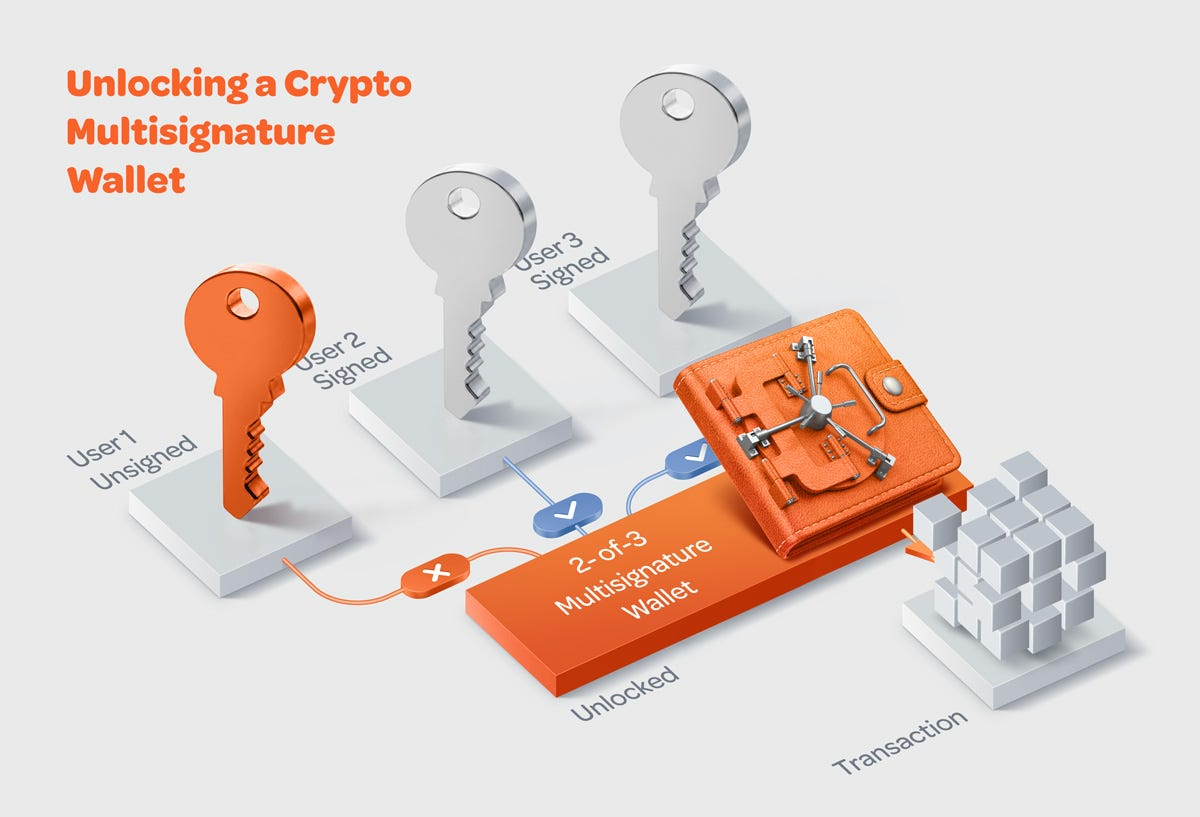
Bybit uses the most secure asset custody solution currently recognized by the cryptocurrency industry - Safe multi-signature wallet combined with hardware cold wallet. This solution sets a 3/3 signature threshold, which means that all three private key holders must authorize at the same time to perform any asset transfer operation. More importantly, these private keys are stored in completely offline hardware wallets, which theoretically has built an almost unbreakable security barrier.
However, the hackers did not attack these technical defenses directly, but chose a more covert method - social engineering attack. They first successfully hacked into the computer systems of the three signatories in some way, and patiently observed and recorded their operating habits, internal communication methods and transfer processes in the dark.
After observing for a while, the hacker targeted the process of transferring funds from cold wallets to hot wallets. According to CEO Ben Zhou, this transfer operation is usually carried out every two to three weeks, and the amount of funds involved each time is huge, mainly to meet the daily transaction needs of hot wallets. So the attacker deployed a malicious contract with a backdoor 3 days in advance. When the signer was performing daily operations, the attacker quietly replaced the normal transaction request with the malicious contract they had deployed in advance. The signer did not notice this when signing, because they saw an ordinary transfer transaction, but in fact, they signed a transaction that allowed the hacker to take over control of the wallet. Because the attacker had complete control over the employee's computer, the transaction information they saw was fake, but the signature was real.
Subsequent analysis showed that the attacker only used a forged signature attack to seize the owner's rights of the Safe wallet, which strongly suggests that more than one device was compromised, and the attacker may have been lurking in the Bybit intranet for a long time and had sufficient internal intelligence. Even the most advanced technical defenses cannot withstand carefully designed social engineering attacks targeting human nature.

Human Weakness: What is a Social Engineering Attack?
Social engineering attacks are a costly, complex but highly effective attack method. Unlike technical attacks, social engineering attacks mainly manipulate people's psychology and behavior to obtain confidential information or control permissions. Attackers do not directly target the system, but take advantage of people's trust, negligence and habits to induce the target to actively disclose information or perform certain operations.
Common attack methods include sending phishing emails, implanting malware, or exploiting loopholes in personal security habits (such as weak passwords, failure to enable two-factor authentication, etc.). Attackers may pretend to be project owners or internal colleagues in the company, contact employees by phone, email, or social media, and trick them into clicking on malicious links or leaking account information. For example, attackers may pretend to need help from developers to debug code and promise to pay them in advance to gain trust.
The biggest threat of social engineering attacks is that they can bypass traditional technical security protection. Attackers usually take advantage of human emotions, curiosity or fear to launch attacks, which are extremely covert. These attacks are not as immediate as viruses or malware. Attackers can lurk in the background for a long time, quietly collecting information and infiltrating, until the right time to suddenly launch an attack.
Lazarus’s terrible record: $6 billion stolen
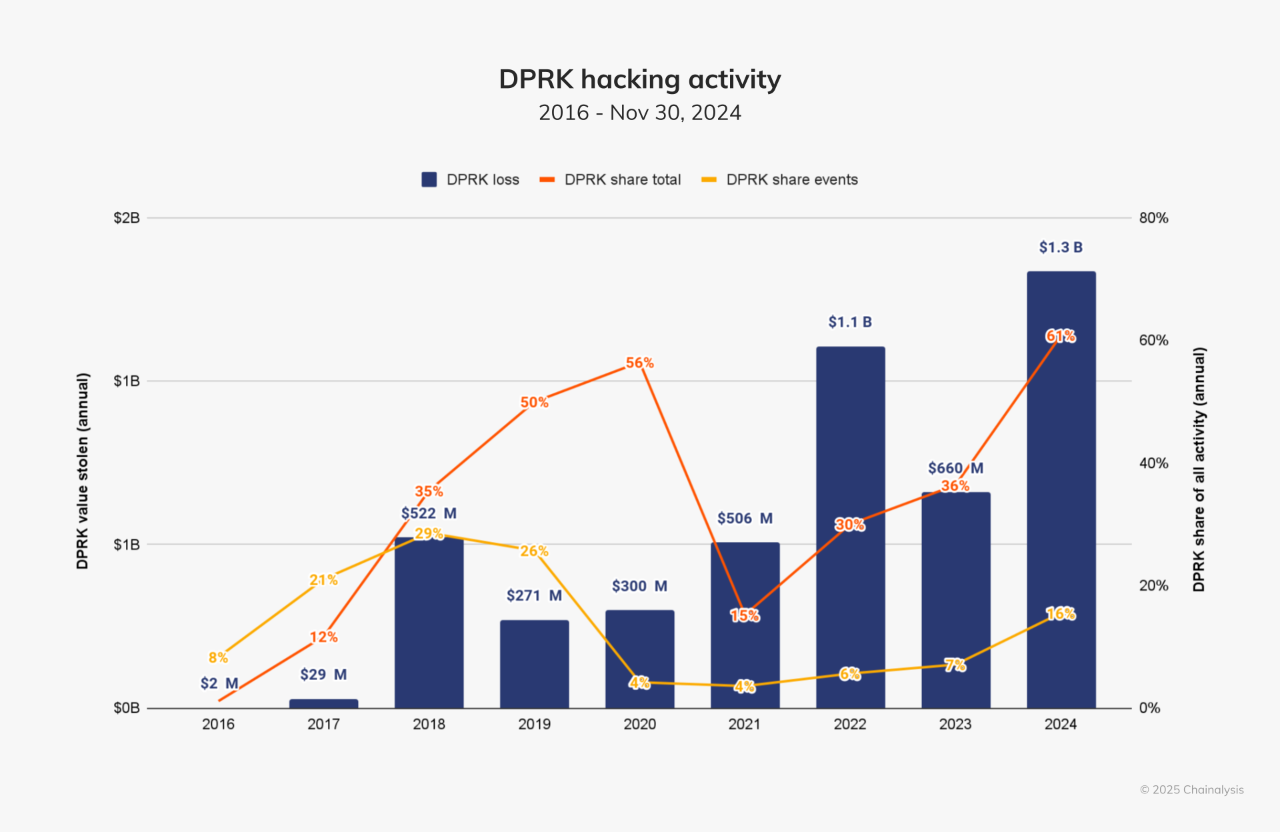
The North Korean hacker group Lazarus Group has been active since 2009 and has turned its attention to the crypto field since 2016. The Chainalysis report shows that from 2016 to 2024, the total amount of theft by the Lazarus Group exceeded $4.6 billion. Among them, $1.34 billion was stolen in 2024, $660 million was stolen in 2023, and $1.1 billion was stolen in 2022. Including the bybit incident in 2025, the total amount of theft by the Lazarus Group in the crypto field so far has directly exceeded $6 billion.
🔍 For more detailed information about the organization, check out this 615-page UN report:
https://documents.un.org/doc/undoc/gen/n24/032/68/pdf/n2403268.pdf
Ronin Incident: Fake Offers Stolen $620 Million
On March 23, 2022, crypto gaming giant Axie Infinity’s Ethereum sidechain Ronin suffered one of the largest hacker attacks in the history of cryptocurrency. The North Korean hacker group Lazarus successfully stole a staggering $620 million in digital assets through a carefully planned social engineering attack. Shockingly, the project did not discover that the treasury had been emptied until six days after the attack when a user reported that he could not withdraw 5,000 ETH.
The attack began with a seemingly ordinary recruitment bait. The Lazarus group forged the identity of a fictitious company and contacted a senior engineer at Sky Mavis (the parent company of Axie Infinity) through LinkedIn with an extremely attractive high-paying position. The engineer was attracted by the attractive salary conditions and actively participated in multiple rounds of "interviews". In one of the interviews, he received a seemingly formal PDF file with a "job offer".
The engineer downloaded and opened the document on his company computer, not knowing that this simple operation had opened the door to the Ronin blockchain network for the attacker. The malicious file quietly infiltrated through the infection chain, eventually allowing the attacker to control four validator nodes and one Axie DAO node in the Ronin network. Since Ronin is set up so that funds can be transferred out if five of the nine validator nodes approve, with control of these five nodes, the hacker easily bypassed the security mechanism and transferred a huge amount of funds.

CoinsPaid:
A sophisticated attack that lay dormant for 6 months
On July 22, 2023, the hot wallet of the crypto payment platform CoinsPaid was attacked by the Lazarus organization, resulting in the theft of approximately $37.3 million in funds. The hacker showed amazing patience, spending nearly 6 months carefully tracking and studying CoinsPaid, gradually accumulating intelligence on the company's internal operations.
Since March 2023, CoinsPaid has recorded multiple attempts to attack the company, including social engineering attacks, DDoS attacks, and brute force attacks. The attackers continue to upgrade their tactics, from technical consulting requests to bribery of employees to pretending to be recruiters of well-known crypto companies, offering salaries as high as $16,000-24,000 per month.
After 6 months of failed attempts, an employee finally responded to a job offer disguised as Crypto.com and installed an application containing malicious code during the "interview" for a "technical testing task." The attacker obtained configuration files and keys, established a connection to the company's infrastructure, and finally successfully stole funds from CoinsPaid's hot wallet.

Industry reflections and future challenges
Debunking the Myth of Cold Wallet Security
This record-breaking theft has sounded the alarm for the entire cryptocurrency industry. First, this incident has broken the myth that cold wallets are absolutely safe. Although cold wallets are regarded as the safest way to protect crypto assets, this attack proves that even cold wallets have their vulnerabilities.
According to CEO Ben Zhou's reflection afterwards, "our cold signatures can be completely dispersed to several wallets, so that all Ethereum is not placed in one wallet." This represents a change in thinking. Instead of thinking about how to never be stolen, it is assumed that if stolen, how to ensure that the loss will not leave the exchange with nothing, but within an affordable range. In the future, exchanges and wallet developers need to explore higher-level security measures, such as using advanced encryption technologies such as zero-knowledge proofs, optimizing multi-signature mechanisms, and even considering solutions that combine physical isolation with biometric technology. Security is no longer just a line of defense, but requires a multi-level, three-dimensional protection system.
Security risks of multi-signature wallets
The Bybit hack also triggered a deep reflection on the security of multi-signature wallets. In a multi-signature transaction, after the first transaction is submitted, subsequent signers may blindly trust the transaction data of the first person and sign directly, ignoring the importance of independent cross-checking. This practice actually violates the original design intention of the multi-signature mechanism.
This incident exposed a major flaw in the traditional multi-signature scheme: the lack of an independent transaction verification layer allows attackers to deceive signers through the control interface or contract logic. In order to avoid similar security incidents, the industry needs to strengthen the review and regulation of the multi-signature mechanism to ensure that each step is independently verified. The industry needs to promote in-depth cooperation with major hardware wallet manufacturers to build an independent third-party signature review channel while retaining their original security solutions. Currently, most of the assets with total locked value (TVL) on the chain are hosted in multi-signature managed contracts, including core infrastructure such as cross-chain bridges and DeFi protocols. If there is a lack of strict review and operating specifications in the contract management process, similar security incidents are likely to occur again.
Regulatory changes and industry transparency
After this attack, global regulators are likely to strengthen security reviews of exchanges and require exchanges to regularly publish audit reports to prove that their asset reserves and security measures meet standards. Bybit experienced the highest number of withdrawals ever in this incident, receiving a total of more than 350,000 withdrawal requests. However, there was no run, and the deposit and withdrawal levels returned to normal in about 12 hours.
Bybit's auditing company Hacken also said that it has confirmed that cash and token reserves can fully cover the $1.5 billion loss. If you encounter a platform with insufficient asset reserves, the consequences may be disastrous. Therefore, strengthening supervision can not only eliminate those platforms with weak security awareness, but also improve the transparency and trust of the entire industry, and promote the industry to develop in a healthier and safer direction.
Hacker technology evolution: AI
and the threat of automated attacks
What is even more worrying is that the technology of organizations such as the North Korean Lazarus Group is evolving rapidly. Their attack methods have become more covert and precise, and they may even begin to integrate artificial intelligence technology into the attack chain. In the future, we may face more complex and automated attack methods, including AI-based precision phishing attacks, more difficult to distinguish deep fake videos, and penetration of the Web3 development tool chain. The development of these technologies means that security protection measures will face higher challenges. The industry must always remain vigilant and strengthen technology updates and defense system construction.

Conclusion: Web3 security is an ongoing game
The security issue of Web3 is not just a single challenge, it is a marathon with no end. As technology continues to evolve, the game between the attacker and the defender will continue to escalate. Only by incorporating security awareness into every aspect of the industry, from code writing to user operations, can we truly establish a reliable cryptocurrency ecosystem and ensure the long-term development of the industry.
References:
- https://www.theblock.co/post/156038/how-a-fake-job-offer-took-down-the-worlds-most-popular-crypto-game
- https://coinspaid.com/company-updates/the-coinspaid-hack-explained/
- https://www.chainalysis.com/blog/crypto-hacking-stolen-funds-2025/
- https://documents.un.org/doc/undoc/gen/n24/032/68/pdf/n2403268.pdf
- https://mp.weixin.qq.com/s/imC09I6Ty5aMkkENZTMOVg











