Ten years have passed since Tether launched USDT, the world's first mainstream stablecoin pegged to the US dollar, in 2014. After more than a decade of development, the total market capitalization of stablecoins exceeded $250 billion in 2025, with an estimated annual transaction volume of $36.3 trillion, surpassing the combined value of Visa and Mastercard. Stablecoins, pegged to specific assets (such as fiat currencies, gold, or other stable assets), enjoy relatively stable value and are widely used in diverse scenarios, including cross-border trade settlement, corporate treasury management, and daily consumer payments. Annualized payments in the B2B sector reach $36 billion, while P2P transfers cover small, high-frequency transactions. Brick-and-mortar merchants such as Metro Singapore and global retail giant SPAR have already accepted stablecoin payments.
However, due to its inherent anonymity, USDT has also been viewed by illicit and underhanded groups as a preferred tool for capital transfer. The "Xinkangjia" scam, which caused a stir in 2025, relied on USDT to collect and transfer funds, ultimately resulting in the loss of assets for thousands of investors. Below, we will delve into new criminal tactics used by illicit and underhanded groups to exploit USDT and, drawing on practical experience in blockchain security, explore countermeasures for businesses and users.
1. USDT issuance on mainstream blockchains
USDT's deployment across multiple public chains facilitates cross-chain fund transfers and evasion of tracking for illicit and gray market actors. The current USDT issuance status across several major blockchains is as follows:
- Tron: TRC20-USDT, issued based on the TRC-20 protocol, has a circulation of over 75.8 billion. With its high throughput and low fees, it has become a popular choice for small, high-frequency transfers by illicit and gray market actors.
- Ethereum: ERC20-USDT has a circulation of over 79 billion. Leveraging the vast DeFi ecosystem, it is often used as a funding vehicle disguised as “normal financial transactions”.
- BNB Chain: BEP20-USDT issuance has exceeded 7.4 billion, and its close integration with the exchange ecosystem has made it a key channel for cross-border fund laundering.
- Solana: SPL-USDT has a circulation of 2.3 billion, and its fast transaction confirmation speed can help black and gray industries shorten the fund transfer cycle;
- Polygon: The amount of USDT issued based on the ERC-20 protocol has reached 1.4 billion. As an Ethereum expansion solution, it is often used to divert large amounts of illegal funds.
This multi-chain distribution allows funds from illegal and gray markets to rapidly switch between different public chains, increasing the difficulty of regulation and tracking. BlockSec's Phalcon and MetaSleuth products have achieved comprehensive monitoring of mainstream chains like Ethereum, BNB Chain, and Polygon, as well as tracking and monitoring over 20 cross-chain bridges, providing technical support for fund tracking and compliance reviews.
2. Six new criminal methods used by black and gray industries to exploit USDT
Method 1: Fake U forgery
Fake USDT is a counterfeit USDT that is often created by tampering with on-chain data and falsifying transaction records to make it look very similar to real USDT, but without any real value. Common tactics used by black and gray industries include:
- On niche exchanges or peer-to-peer trading platforms, users are lured into private transactions by offering a discount of 5%-10% below the market price.
- Forged USDT transfer record screenshots to deceive victims into paying fiat currency or other assets first;
- Develop a fake wallet app with a built-in "fake U generation function" to make victims mistakenly believe that they hold real USDT, and then defraud the wallet private key.
While this type of scam is difficult for ordinary users to identify, it can be easily verified with specialized tools. Common blockchain explorers (such as Etherscan) and BlockSec's MetaSuites plug-in can quickly identify the "abnormal transaction characteristics" of fake Us through on-chain data verification, helping users and businesses mitigate this risk. This capability, built on BlockSec's years of full-chain risk monitoring capabilities, allows for real-time identification and storage, resulting in hundreds of millions of risky contract address tags.
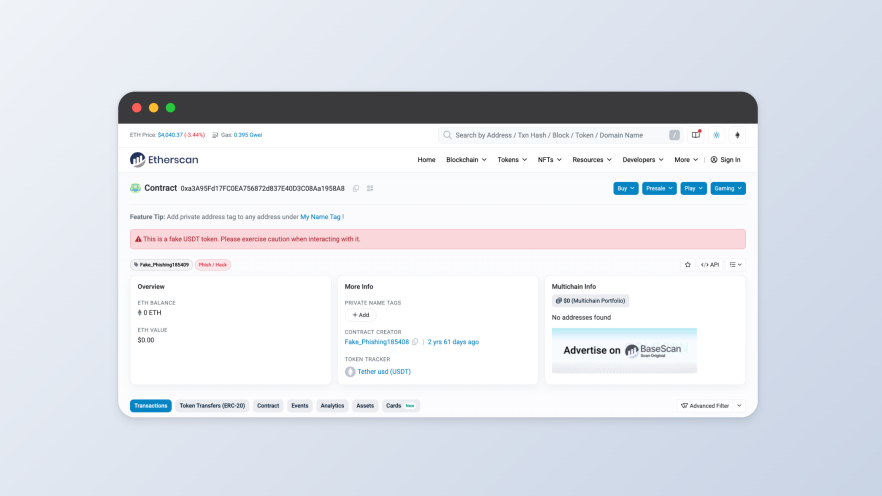
Method 2: Black U circulation
Black money refers to USDT obtained through illegal activities such as telecom fraud, online gambling, theft, human trafficking, and terrorist financing. The core risk lies in the "compliance of the source of funds." Black money often flows into the legitimate market through the following methods:
- "Running Points" platform distribution: Setting up a fake "digital currency trading agent" platform to attract ordinary users to become "running points customers" and use their personal bank cards to receive legal tender exchanged by Black U, which is then transferred to designated accounts to complete the "fund splitting";
- DeFi protocol coin mixing: Using the "anonymous lending" and "liquidity mining" functions of the DeFi platform to mix black U with other compliant assets, increasing the difficulty of fund tracing and obscuring the flow of funds;
- Cross-border OTC transactions: Black U is exchanged for other virtual currencies through anonymous overseas OTC merchants, and then transferred to domestic exchanges for cash.
For businesses (especially exchanges and payment institutions), the influx of illegal U funds can lead to wallet freezes at best, license revocation, hefty fines, or even criminal imprisonment at worst. BlockSec's Phalcon Compliance product uses address risk scoring, fund traceability, and AI-powered risk behavior analysis to identify high-risk addresses and unusual transaction patterns associated with illegal U funds in real time. This helps businesses intercept illicit funds during user deposits and transactions, meeting anti-money laundering (AML) and compliance requirements.
Method 3: Stealing U and upgrading
The means of stealing USBs have evolved from simple "phishing links" and "address poisoning" in the early days to more covert technical attacks, mainly including:
- Malicious plug-in hijacking: Implanting plug-ins in browsers to monitor user wallet operations and steal private keys or transfer authorizations;
- Smart contract vulnerability exploitation: Targeting DeFi platform contract vulnerabilities, launching attacks to transfer user-staked USDT (e.g., a lending agreement in 2024 was stolen 120 million USDT due to a “reentrancy vulnerability”);
- Supply chain attacks: Invading third-party tools (such as wallet SDKs and transaction APIs), implanting "backdoors" in the code, and stealing user assets in batches.
Bybit's $1.5 billion theft was a coordinated, targeted on-chain attack launched by a sovereign nation. The attacker deceived multiple Safe Wallet operators into signing Safe Wallet upgrade transactions, ultimately taking control of the wallets. A detailed analysis of the attack is available in: Analysis of the Bybit Theft. An in-depth analysis of the Bybit theft.
- Malicious upgrades: Using new blockchain features like 7702 to trick project owners into signing transactions, take over their privileged accounts, and steal assets. For example, the recent thefts of SeedifyFund and Griffin_AI projects were carried out using this method.
The BlockSec team has repeatedly detected such attacks and, through the Phalcon Security threat monitoring and attack blocking platform, helps project owners stay ahead of hackers and automatically block attacks the moment they occur. Furthermore, Phalcon Compliance's "Vulnerability Association Address Library" helps companies proactively flag malicious addresses involved in attacks, preventing them from laundering funds through the platform. To date, BlockSec has completed over 20 white hat rescues, recovering over $20 million in losses and safeguarding over $50 billion in on-chain digital assets in real time.
Method 4: USDT money laundering
Currently, money laundering in the black and gray industries has formed a "multi-chain jump + DeFi tool nesting" model. The typical process is:
1. Black and gray industries convert illegal funds into USDT and transfer them to 10-20 "intermediary wallets";
2. Transfer USDT to different public chains (such as from Ethereum to Polygon) through a cross-chain bridge, and conduct a "borrow-collateralize-exchange" cycle on the DeFi platform;
3. Transfer the laundered USDT to an offshore exchange and convert it into legal tender or other assets to complete the capital outflow.
Under this model, the capital chain is fragmented into dozens of segments, making it difficult to penetrate with traditional tracking methods. However, BlockSec, through its "full-chain capital map" technology, can restore cross-chain capital flows, identify "abnormal circulation characteristics" in DeFi operations, and provide companies with compliance reports that meet FATF (Financial Action Task Force on Money Laundering) standards, helping them meet cross-border capital regulatory requirements.
Method 5: USDT scoring platform
The USDT running point platform is a typical model for black and gray industries to "launder" funds by exploiting ordinary user accounts. Its operating logic is hidden and highly deceptive:
The illicit industry gangs first set up a fake "digital currency trading assistance platform," using the gimmick of "part-time work from home, earning hundreds of yuan a day" to attract unemployed individuals, students, and other groups to register as "runners." The platform requires runners to link their personal bank cards or virtual currency wallets. The platform then splits USDT (USDT) garnered from overseas fraud and online gambling scams and assigns it to runners as "platform tasks." After receiving the USDT, runners must follow the platform's instructions to transfer the equivalent amount in fiat currency to a designated account, completing the "running" process. The platform then pays a commission of 1%-3% of the transaction amount.
This model breaks large amounts of illegal funds into hundreds of small transactions, using ordinary users' "legitimate accounts" to obscure the source of the funds, making it extremely difficult for regulators to track them. Phalcon Compliance can quickly identify the core funding pool addresses of scoring platforms by analyzing abnormal patterns such as "multiple accounts funneling funds to the same address" and "small, high-frequency transfers."
Method 6: Virtual currency pyramid scheme
Virtual currency pyramid schemes often use the guise of "blockchain innovation" and "stable returns" to package USDT as an "investment target" or "entry threshold" to attract users and recruit downline members. Their routine is mainly divided into three steps:
- Personality packaging: Using social media platforms to create fake personas such as "cryptocurrency tycoons" and "foreign financial experts," they share fake cases of "USDT investment with a 20% monthly return" to create the illusion of "low risk, high return";
- Tiered new member acquisition: Setting an "investment threshold" - users need to deposit 1,000-10,000 USDT to become a member, and can be upgraded to an "agent" by developing 3 downlines, and receive a "referral reward" of 5% of the downline's investment amount. The higher the tier, the higher the commission ratio;
- The funding pool collapsed: In the early stages, the USDT of new users was used to pay "profits" to old users to keep the scam running; when the growth of new users slowed down and the inflow of funds was insufficient, the gang directly closed the platform and took away all the users' USDT and ran away.
Investors should fully understand the high risks of the virtual currency market, especially the widespread use of USDT in the black and gray sectors. Avoid blindly believing promises of guaranteed profits and remain highly wary of investment projects with inflated returns and minimal risk.
III. Conclusion
As a key asset in the blockchain ecosystem, USDT's inherent "tool attributes" are neither good nor evil. However, its abuse by illicit and gray market actors poses a serious threat to financial security and user assets. From counterfeit USDT to multi-chain money laundering, the increasing sophistication and covertness of criminal methods necessitate the use of professional compliance tools (such as Phalcon Compliance) to build risk mitigation strategies and heighten user awareness.