Author: BUBBLE
In October 2025, the United States District Court for the Eastern District of New York disclosed an unprecedented cryptocurrency asset seizure case, in which the US government confiscated 127,271 bitcoins, worth approximately US$15 billion at market price.
Cobo co-founder Shenyu stated that law enforcement agencies did not obtain private keys through brute force or hacking, but rather exploited randomness vulnerabilities. Some forums also claim that law enforcement agencies directly seized wallet mnemonics or private key files from servers and hardware wallets controlled by Prince Group executive Chen Zhi and his family, but the specific facts have not been publicly reported.
These hardware wallets were subsequently transferred to multi-signature cold storage maintained by the US Marshals Service (USMS), a subsidiary of the US Treasury Department. The 9,757 BTC transfer signed by the USMS to the official escrow address on October 15, 2025, originated from this storage facility. The US Department of Justice's indictment described Lubian as part of a money laundering network run by the Cambodian Prince Group, emphasizing that the criminal group attempted to launder fraudulent funds using "new coins" mined by mining pools.
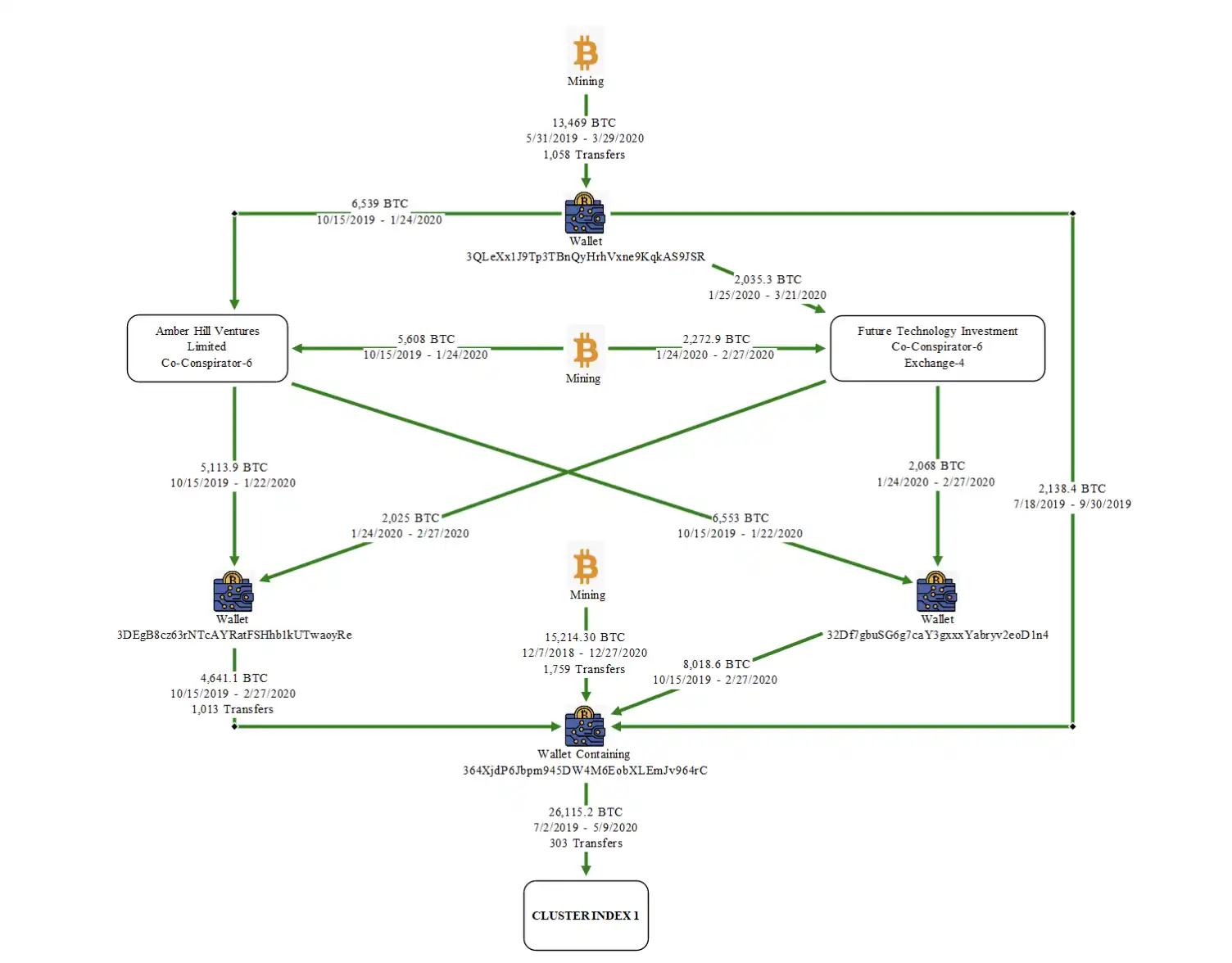
Some community members tracked on-chain data and determined that this was the batch of Bitcoins that was stolen from the Lubin mining pool due to a vulnerability in late 2020. The Lubin mining pool suddenly appeared in 2020. There was no team background information and no published operating model, but its computing power ranked among the top 10 mining pools in the world in just a few months, and at one time occupied nearly 6% of the world's computing power.
The report mentioned that Chen Zhi boasted to other people in the Prince Group that "the profits were considerable because there were no costs", but it is not clear whether this group was founded by Chen Zhi or controlled later. However, this case has pulled the dormant giant whale out of the water again, forcing people to re-examine the wallet private key security disaster that was lurking around 2020.
When researchers later reinvestigated the incident, they found that the first two words of the first mnemonic phrase used in the corrupted key generation process were "Milk Sad," and the incident became known as the Milk Sad incident.
Hidden dangers of weak random numbers
And all of this stems from the Mersenne Twister MT19937-32, a pseudo-random number generator.
Bitcoin private keys are supposed to consist of 256-bit random numbers. Theoretically, there are 2^256 possible combinations. To generate a completely consistent sequence, the heads and tails of 256 coin tosses need to match perfectly. The probability of this happening cannot be zero, but it’s pretty close. Wallet security doesn’t come from luck, but from this huge potential space.
However, the Mersenne Twister MT19937-32 random number generator used by tools like the Lubian mining pool is not a truly fair "coin-flipping machine," but rather a stuck device that always selects numbers within a limited and regular range.
After hackers master this rule, they can quickly list all possible weak private keys through brute force enumeration and then unlock the corresponding Bitcoin wallet.
Due to the misunderstanding of security by some wallet or mining pool users, between 2019 and 2020, many Bitcoin wallets generated using this "weak random algorithm" accumulated astonishing wealth, and a large amount of funds poured into this vulnerable range.
According to statistics from the Milk Sad team, between 2019 and 2020, the cumulative number of bitcoins held by these weak-key wallets exceeded 53,500.
Funding came from both whale-level centralized transfers, with four weak wallets receiving approximately 24,999 bitcoins in a short period of time in April 2019. It also came from daily mining revenue, with some addresses receiving over 14,000 bitcoins in a single year from miners marked "lubian.com." There are now 220,000 such wallets, and their holders are apparently unaware of the hidden dangers in the private key generation process, continuing to invest their assets to this day.
Mass evacuations at the end of 2020
The long-buried security risk erupted at the end of 2020. On December 28, 2020, abnormal transactions occurred on the chain. A large number of wallets belonging to the Lubian weak key range were emptied within a few hours. Approximately 136,951 bitcoins were transferred out at once. Based on the unit price of approximately US$26,000 at the time, the value was approximately US$3.7 billion.
The transfer fee was fixed at 75,000 sats, regardless of the amount, demonstrating the operator's thorough understanding of the Bitcoin network. Some funds subsequently flowed back to the Lubian mining pool for subsequent mining rewards, indicating that not all transferred funds fell into the hands of the hackers. However, for the victims, the loss was already realized.
Even more bizarrely, some on-chain transactions carry messages such as "To the white hats who want to save our assets, please contact 1228btc@gmail.com." Because the weak private key addresses have been exposed, anyone can send transactions with messages to these addresses, and these messages don't necessarily come from the actual victims.
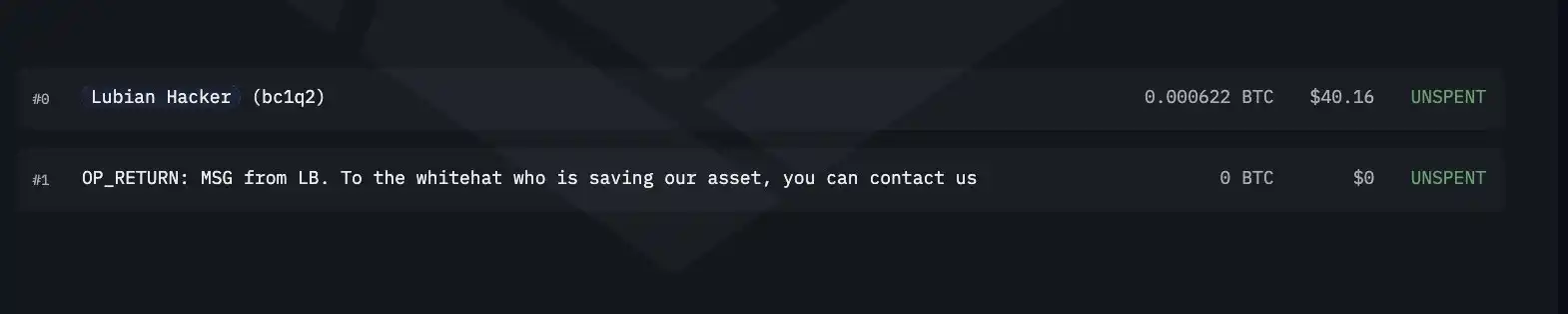
Whether it was a joke by the hackers or a request for help from the victims remains unknown. Crucially, the huge transfer was not immediately considered a theft.
In a subsequent analysis, Milk Sad researchers admitted that, given the surge in Bitcoin prices and the cessation of mining pool revenue at the time, they were unsure whether the theft was the work of hackers or whether Lubian management sold off their wallets at a high point and reorganized their wallets. They noted, "If the theft occurred in 2020, it would be earlier than the confirmed timeline for the Mersenne Twister weak key attack, but we cannot rule it out."
Precisely because of this uncertainty, the capital withdrawal at the end of 2020 failed to trigger industry alarms, and huge amounts of Bitcoin subsequently remained silent on the chain for many years, becoming an unsolved mystery.
Therefore, it wasn't just Lubian that was affected, but also older versions of Trust Wallet. On November 17, 2022, security research team Ledger Donjon first disclosed the random number vulnerability in Trust Wallet to Binance. The team responded quickly, pushing a fix to GitHub the next day and notifying affected users.
However, it was not until April 22, 2023, that Trust Wallet officially disclosed the details of the vulnerability and compensation measures. During this period, hackers exploited the vulnerability to launch several attacks, including stealing approximately 50 bitcoins on January 11, 2023.
Late Alarm
Meanwhile, a vulnerability was brewing in another project.
The bx seed command of Libbitcoin Explorer 3.x uses the MT19937 pseudo-random number algorithm plus the 32-bit system time as the seed, and the generated key space has only 2^32 combinations.
Hackers quickly began exploratory attacks, and starting in May 2023, numerous small thefts occurred on-chain. On July 12, the attack reached its climax, with a large number of wallets generated by bx being emptied. On July 21, MilkSad researchers, while helping users troubleshoot losses, discovered the root cause of the issue: the weak random number in the bx seed allowed private keys to be brute-forced. They immediately notified the Libbitcoin team.
However, since the command was officially regarded as a testing tool, initial communication was not smooth. The team eventually bypassed the project party, publicly disclosed the vulnerability on August 8, and applied for a CVE number.
It was this discovery in 2023 that prompted the Milk Sad team to reverse engineer historical data. They were surprised to find that the weak key range that accumulated huge amounts of funds between 2019 and 2020 was associated with Lubian, and that the huge transfer mentioned above occurred on December 28, 2020.
At the time, there were approximately 136,951 bitcoins residing in these weak wallets, with the massive outflow on that day worth approximately $3.7 billion, and the last known movement was the wallet consolidation in July 2024.
In other words, the suspicious nature of the Lubian incident only surfaced after the weak randomness vulnerability was exposed. The missed warning window had already vanished, and the whereabouts of the bitcoins at that time were also completely lost. Five years later, with the joint indictment of Prince Group and Chen Zhi by the US Department of Justice (DOJ) and UK authorities, the case finally became clear.
For us, the phrase “Not your Wallet, Not Your Money” can only be effective under the premise of randomness.







