Author: Yiping, Jiawei, Danny, IOSG
What is TEE?
The TEE isolates sensitive data in a protected CPU enclave during processing. The contents of the enclave, including the data being processed and the processing methods, are visible only to authorized program code and cannot be accessed or understood by anyone or anything else, including cloud service providers.
▲ Source: Twitter
The configuration of a TEE determines which entities are authorized to input data, the types of data sets and programs that can be processed, and the output results that are allowed. One of the core functions of a TEE is to verify its correct configuration through a separate certification process. The certification process provides cryptographic verification of the hardware and configuration elements of the TEE, thereby ensuring the security of its isolated processing.
The Development and Evolution of TEE
The evolution of TEE revolves around three concepts:
- Developer Experience
- performance
- Security
Developer Experience
Intel SGX revolutionizes security hardware and provides strong isolation capabilities close to local performance, but its developer experience is challenging. Developers need to rewrite a lot of applications to adapt to the SGX programming model. This complexity limits its application outside of a few areas such as key management.
With the introduction of frameworks like Gramine, the developer experience has been significantly improved. Gramine provides software abstraction for CPU isolation zones, allowing developers to compile applications directly into binaries and run them in SGX. Gramine acts like a "glue" that connects the SGX environment to the regular Linux environment.
Performance Improvements
As TEEs evolve into Confidential VMs and GPUs such as Intel TDX and H200, developers can directly deploy unmodified applications. Developers can package and run the entire production environment directly in an encrypted virtual machine. H200 is the first product to provide GPU-level TEE, capable of running more AI and image processing related applications.
For example, the dStack platform further simplifies developers' deployment and expansion in confidential computing environments. Based on a microservices architecture, dStack supports multiple microservices to be deployed and communicate securely in a single TEE instance. This modular design enables more complex workflows to run securely in TEE.
Security
The security of TEE relies on the root of trust provided by the hardware manufacturer, but this also brings reliance on proprietary hardware and closed-source implementations, which may raise concerns about transparency and potential backdoors. To address these issues, open source TEE solutions such as Keystone and OpenTEE are gradually becoming viable alternatives. Although their performance is currently inferior to proprietary solutions, their transparent design and verifiable manufacturing process enhance trust in the integrity of the hardware.
Developers can also combine multiple TEEs from different vendors, run the same workload and compare the output results. This cross-validation reduces the risk of potential vulnerabilities in a single TEE.
Another key security challenge is side-channel attacks. These attacks extract sensitive data from TEEs through physical characteristics such as timing, power consumption, or electromagnetic leakage. A novel solution is to deploy TEEs in a completely isolated environment. For example, the SpaceCoin project plans to launch TEEs into orbiting satellites to eliminate the threat of proximity-based attacks through the physical isolation of satellites. By running calculations in space, these TEEs achieve protection against side-channel attacks and other physical threats.
The Future of TEEs
As TEEs evolve further, the tradeoffs become more complex:
- Improving the developer experience may increase the trusted computing base (TCB).
- Open source instruction sets may reduce performance but improve verifiability.
- Improvements to the TCB through the Yocto Project may make deployment more complex.
From creating fun social experiences, to building a fair global financial system, to training large models with sensitive data, to enabling privacy-focused identity management at a global scale, we need to reach the fifth level of TEE - the holy grail of encrypted computing, and the future prospects are exciting.
Early TEEs, such as SGX, required developers to write custom C code or use abstraction layers like Gramine that provided a Linux-like interface.
Advanced solutions such as TDX and Nitro now support containerized workflows like Docker, but debugging can still be difficult.
Paradigm envisions enabling multi-isolated zone collaboration through multi-party computation (MPC) or fully homomorphic encryption (FHE) to mitigate the risk of single-isolated zone failure.
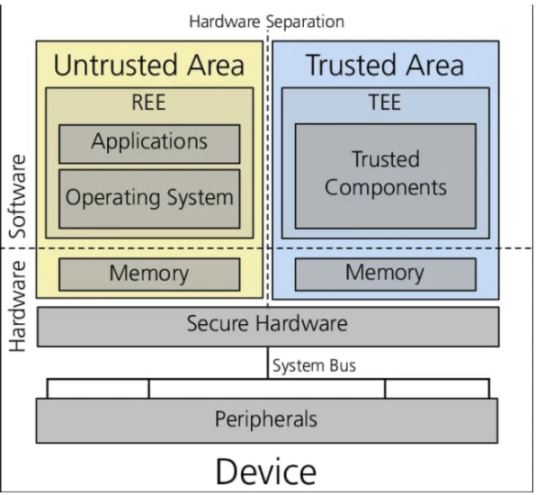
For Crypto x TEE, Phala, Automata and Flashbot are promoting the establishment of standards. By providing standards and improving Tee-related basic services, Crypto TEE can be quickly adopted by more protocols.
▲ Source: IOSG
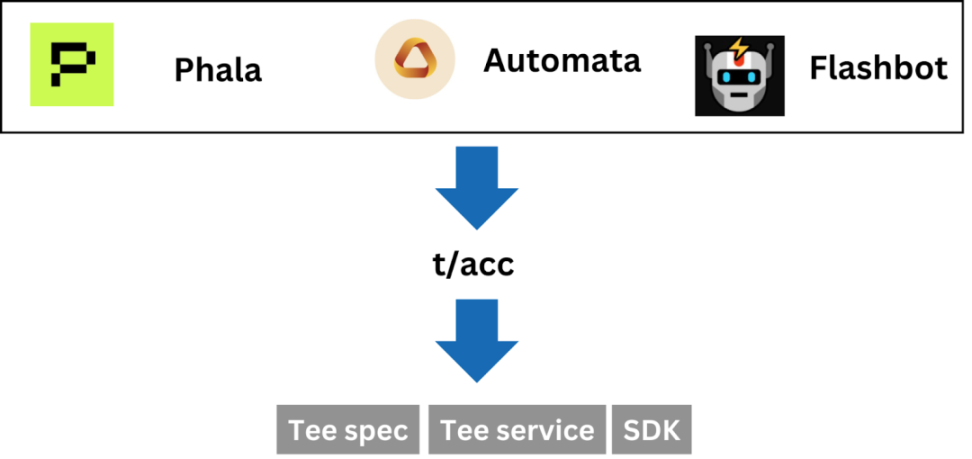
Use Cases for TEEs
TEE hardware in a decentralized network creates a trusted computing environment, known as Decentralized Confidential Computing, which has spawned many interesting and market-focused use cases in the crypto space, including Agent, DePIN, and social media account management. Among many emerging infrastructures, Unichain, Flashbots, and Taiko are also using TEE to optimize their services.
▲ Source: IOSG
MEV related use cases
As a pioneer in the MEV field, Flashbots began exploring the role of privacy technologies like TEE in the transaction lifecycle as early as December 2022. Its main goal is to achieve trust-free collaboration in the transaction supply chain, including decentralized block building and order flow sharing. Flashbots has conducted a series of TEE-related research and experiments, such as running the Ethereum client Geth in Intel SGX and performing block builder operations in SGX.
For a long time, 90% of Ethereum blocks were built by only two block builders, which posed a continuous risk to Ethereum's decentralization, resilience, and censorship resistance. To enhance the decentralization of block building, Flashbots launched BuilderNet, a decentralized block building network for Ethereum powered by TEE. The network also supports refunds to upstream order flows from dApps, wallets, and users, while ensuring security and performance.
Subsequently, Flashbots ceased operations of its centralized block builder on the mainnet and migrated to BuilderNet. Beaverbuild, currently Ethereum’s number one block builder, also integrated its software, infrastructure, and order flow into this decentralized network.
A few months ago, Flashbots, together with Uniswap Labs and OP Labs, launched Rollup-Boost on Unichain, a verifiable Rollup block building platform based on TEE support.
Based on similar TEEcoprocessor technology, Flashbots also released Teleport - an application that uses the TEE coprocessor to implement smart contract control of Twitter accounts.
AI-related use cases
The combination of Crypto and AI has given rise to many links, which have been described in previous articles by IOSG. With the increase in support for TEE running on GPUs, the demand for TEE in various aspects of AI has been realized, including
- Data collection & annotation
- Model Training
- Model Inference
- Autonomous Agent
Data collection & annotation
Under the influence of Scailing Law, data has become the most important part of AI development. Crypto can provide the greatest help to AI at the data layer by encouraging users to contribute private data and data annotation through a decentralized mechanism, making up for data sets that cannot be obtained on the public network, especially labeled data. TEE can improve the privacy and security of data collection and annotation.
Take Vana as an example. Vana is a decentralized data network in which Satya-type validators specialize in providing TEE environments. Through TEE verification nodes, the data liquidity pool (DLP) in Vana, which serves as a data market, can ensure the traceability and accuracy of data and provide data securely without exposing the original data. Users submit encrypted data to smart contracts, and smart contracts create asset identifiers for users. User data is transmitted to TEE nodes through end-to-end encryption protocols (such as TLS), and the data is decrypted in the TEE nodes to generate quality certificates.
From the user's perspective, TEE transforms data into a verifiable asset, and data becomes a kind of "right to use". Users retain ownership of the data, receive corresponding types of token rewards, and participate in decision-making through the governance mechanism.
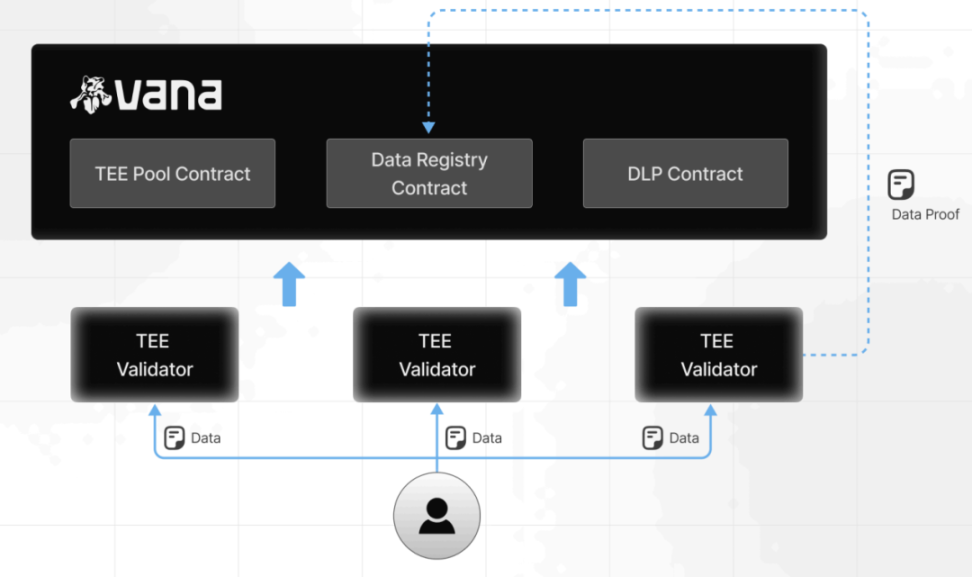
▲ Source: Phala 2025 Report
Especially for sensitive data such as medical or financial data, TEE makes the provision and labeling of data private. This is crucial to maintaining users' confidence in providing data and complying with data protection regulations such as GDPR and CCPA at the compliance level.
Model Training
The independence of TEE means that it is the best place for model training. With the popularity of GPU-based TEE and the improvement of hardware performance, TEE can support more training scenarios. Currently, through the Nvidia H200 GPU, open source models such as Llama-3.1-8B can be fine-tuned, which not only ensures the isolation and encryption of training data and calculations, but also generates cryptographic proofs and model fingerprints for public verification. With appropriate parameters, the model training performance of TEE is sufficient to support most models. Training Llama-3.1-8B in the TEE of the H200 GPU completed 30 rounds of training in just 1 hour, achieving 98% accuracy with almost no performance loss.
The hardware-dependent nature of Tee requires a decentralized GPU network to support the stability of its training. For example, Hyperbolic uses TEE to support AI training between distributed nodes, which is lower in cost than centralized GPU providers such as OpenAI, while also providing verifiable proof of execution.
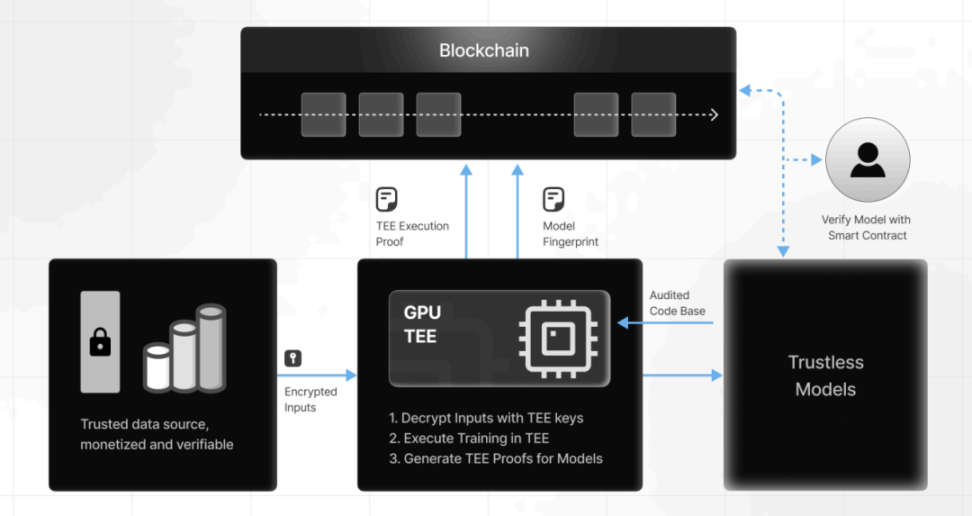
▲ Source: Phala 2025 Report
Platforms with strong demand for AI training can easily access TEE technology. For example, Near and Phala jointly built TEE model training capabilities.
▲ Source: Twitter
Model Inference
From the user's perspective, the most important thing is whether the model used has actually been calculated by the corresponding model. From the Chatgpt interface to the open source model in the TEE environment. The reasoning process supported by TEE can verify the reasoning results of the model. Nvidia GPU TEE allows the reasoning process to protect user privacy without sacrificing speed and accuracy. Services such as Phala's confidential AI reasoning will generate verification proofs for each output. Users can verify whether the reasoning actually occurs in the TEE, which enhances trust in the AI output results. Platforms such as 0G integrate TEE into AI reasoning services to ensure end-to-end data protection and verifiability from request to response.
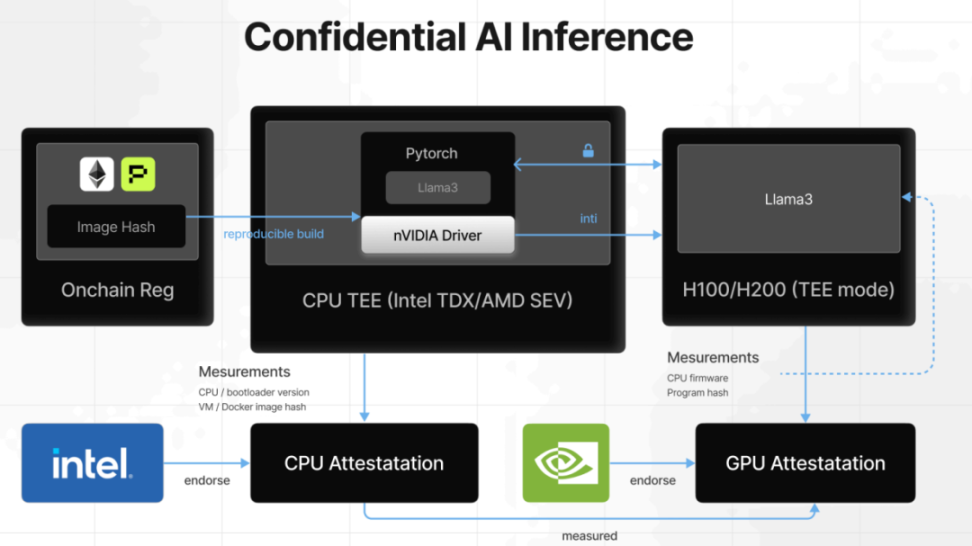
▲ Source: Phala 2025 Report
Platforms with strong demand for AI training can easily access TEE technology. For example, Near and Phala jointly built TEE model training capabilities.

▲ Source: Twitter
Autonomous Agent
Crypto Agents are gradually becoming important participants in on-chain activities. In order to truly allow agents to participate more effectively in the on-chain financial system, agents need to be given autonomy and sovereignty.
Autonomy means that the operation, decision-making, input and output of the Agent are not subject to human intervention. For example, autonomy means that the input and output content pushed by Truth Terminal cannot be controlled by Andy. Although it is not a direct intervention at present, there is still suspicion of guidance from the background prompt. Sovereignty emphasizes ownership. Including Crypto assets and computing resources. The Agent has 100% control over the assets and independent control over its own operating environment.
Autonomous and sovereign agents are the prerequisite for opening up more use cases. Only when agents have autonomy can they play a role in more economic activities. At the same time, this is an unprecedented social experiment, and it can only happen in Crypto. Any progress is a super meme, which will generate a huge attention economy in the crypto market.
At present, the most widely used Eliza framework of ai16z has integrated TEE technology. Developers can quickly deploy agents with TEE features through Eliza. Agents can autonomously obtain control over Twitter accounts, wallets, and computing resources through TEE.
The earliest TEE agent experiment came from Pet rock, an agent that runs in a TEE environment and has Twitter permissions. Later, AI pool provided a launchpad with fair launch and rich randomness through the fact that the Agent's operations in TEE are not interfered with by the outside world. You only need to send money to a specific address, and the agent will be initialized with security parameters. After initialization, when the money transfer process is completed, the agent will automatically select a random time, a random ticker, and deploy liquidity and launch tokens. All these operations are run in an environment protected by TEE, and humans cannot interfere. Spore.fun even demonstrated the process of Agent managing wallets through TEE.
Any TEE agent has a corresponding verification process, which allows users to verify at any time whether the agent is running in the TEE and whether the permissions are really not controlled by humans. In addition to TEE, this can also be done through ZK.
Many TEE projects are trying to collaborate with Agent projects to create some more innovative gameplay.
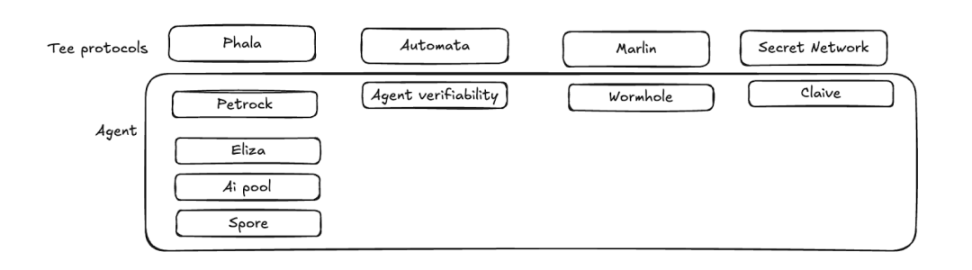
▲ Source: IOSG
As Agents become smarter, they play a more important role in the on-chain ecosystem, and it is more important to reduce their impact on humans. Embedding TEE into the life cycle of the agent is the most visible way to achieve this.
Conclusion
For Crypto, TEE is a trusted computing tool with strong usability and rapid application development. Its development revolves around three directions: developer experience, performance, and security, and is also subject to hardware constraints. With the development of GPUs led by NVIDIA, TEE has gradually transitioned from SGX to TDX.
At the application level, AI, social networking, and depin are the strong application directions of Toc, while block building is an application direction that is biased towards infra. With the development of AI narrative, TEE can contribute to the computational privacy and model/data traceability of different AI links in decentralized computing, and can give Agent the ability to operate independently and autonomously. Social networking and depin are new retail directions that are constantly being explored. For the operation of the blockchain itself, TEE will serve as an important node capability in the future, bringing privacy and fairness to the blockchain.
As the underlying services/SDKs become more mature, the threshold for various projects to use TEE technology is getting lower and lower. Service providers focusing on TEE for crypto applications are accumulating in the direction of standardized unified standards, mature open source technology support, etc., and have already created many new use cases. With such vertical integration, we expect to see more explosions of TEE-based applications.














