Background
Recently, we detected a series of attacks on Ionic Money on Mode Chain:
https://explorer.mode.network/tx/0x37e53b15cb7f298bd8c45fcbbd914ba90feb3946f5511fc55bc986b7472956df
Ionic Money is a compound fork DeFi project that provides services on Base, Optimism, Bob, Fraxtal, Lisk, and Mode. This time, it was attacked by an attacker on Mode Chain, and a total loss of about 8.5 MUSD was caused by this attack.
Attack and incident analysis
First, the attacker used 60 LBTC to redeem undelying assets, 300 ionLBTC, through mint.
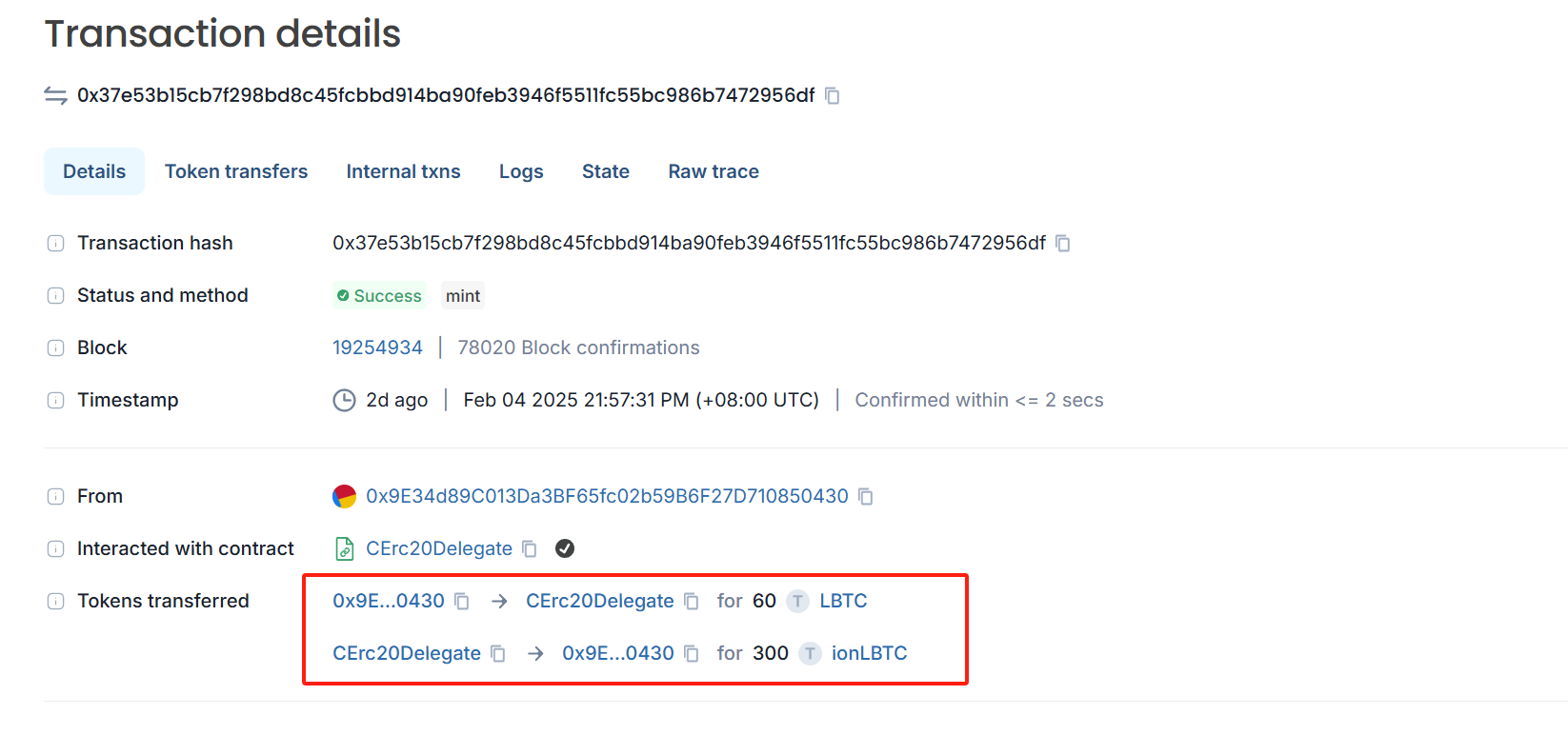
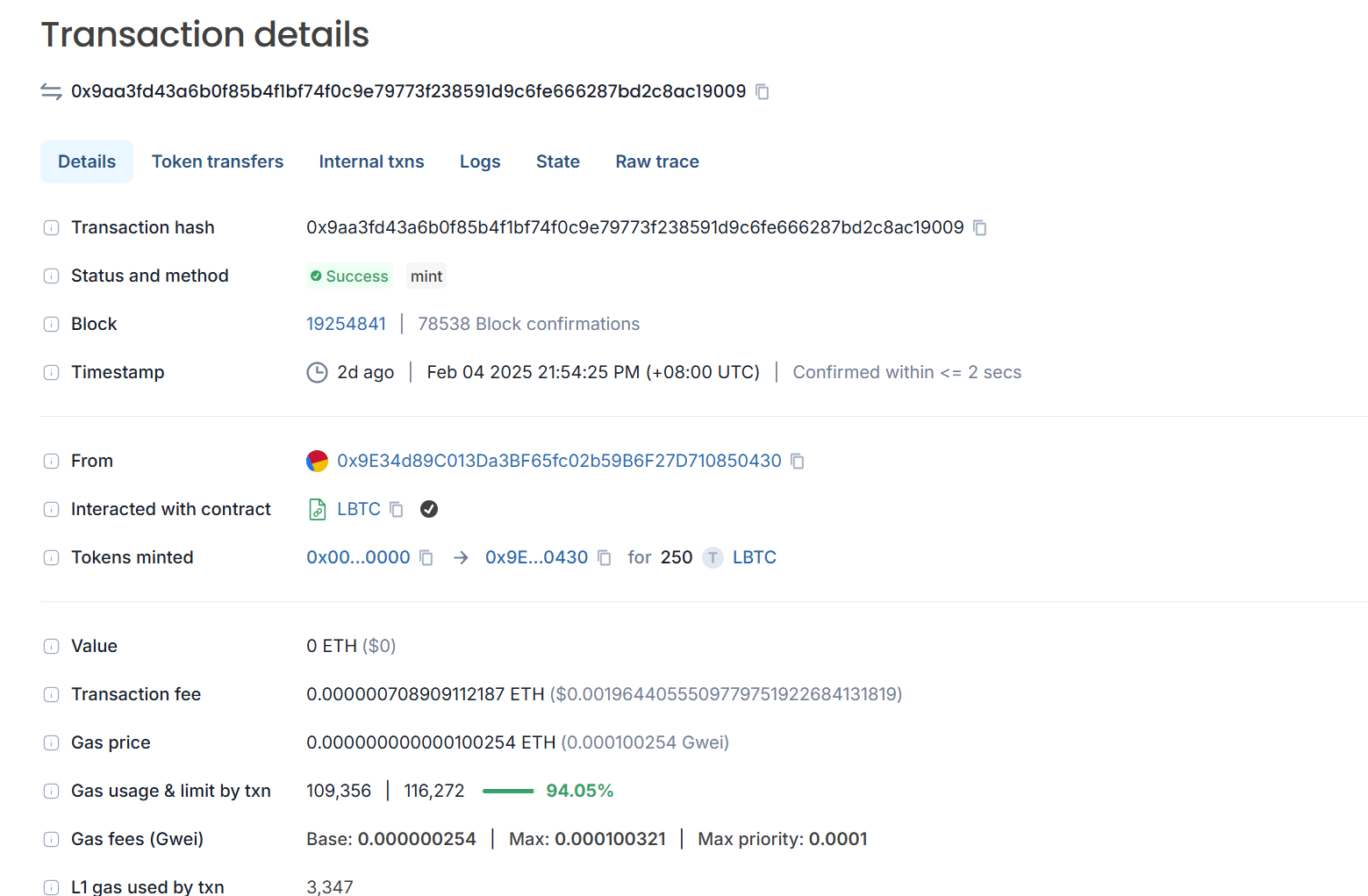
However, when we looked at the source of the attacker’s 60 LBTC, we found that these 60 LBTC were minted by the attacker himself. The attacker obtained 250 LBTC through minting before launching the attack.
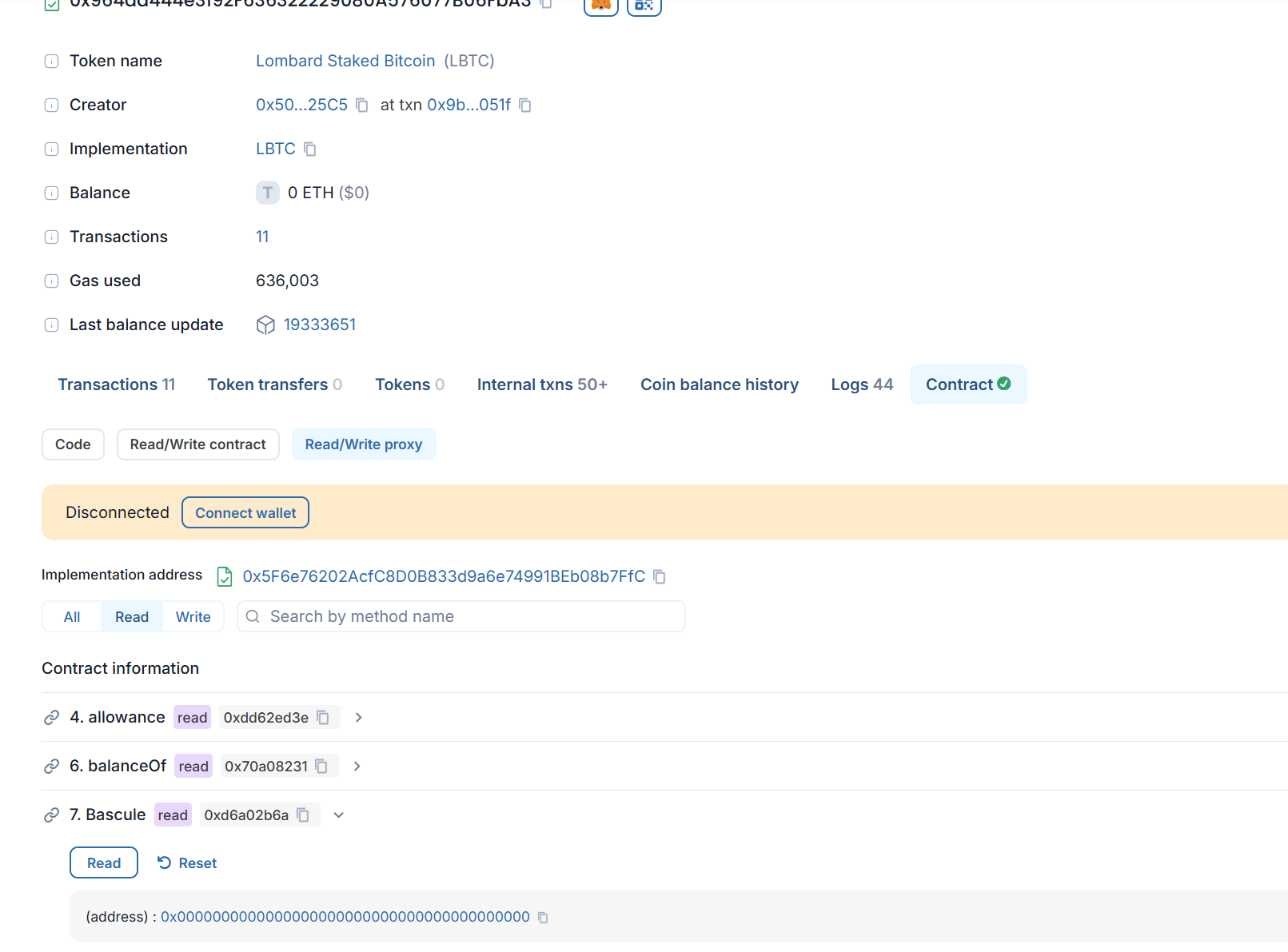
Then, we checked the LBTC contract and found that the Bascule in the contract was:
0x0000000000000000000000000000000000000000.
In the implementation of LBTC, mint needs to be verified by Bascule.
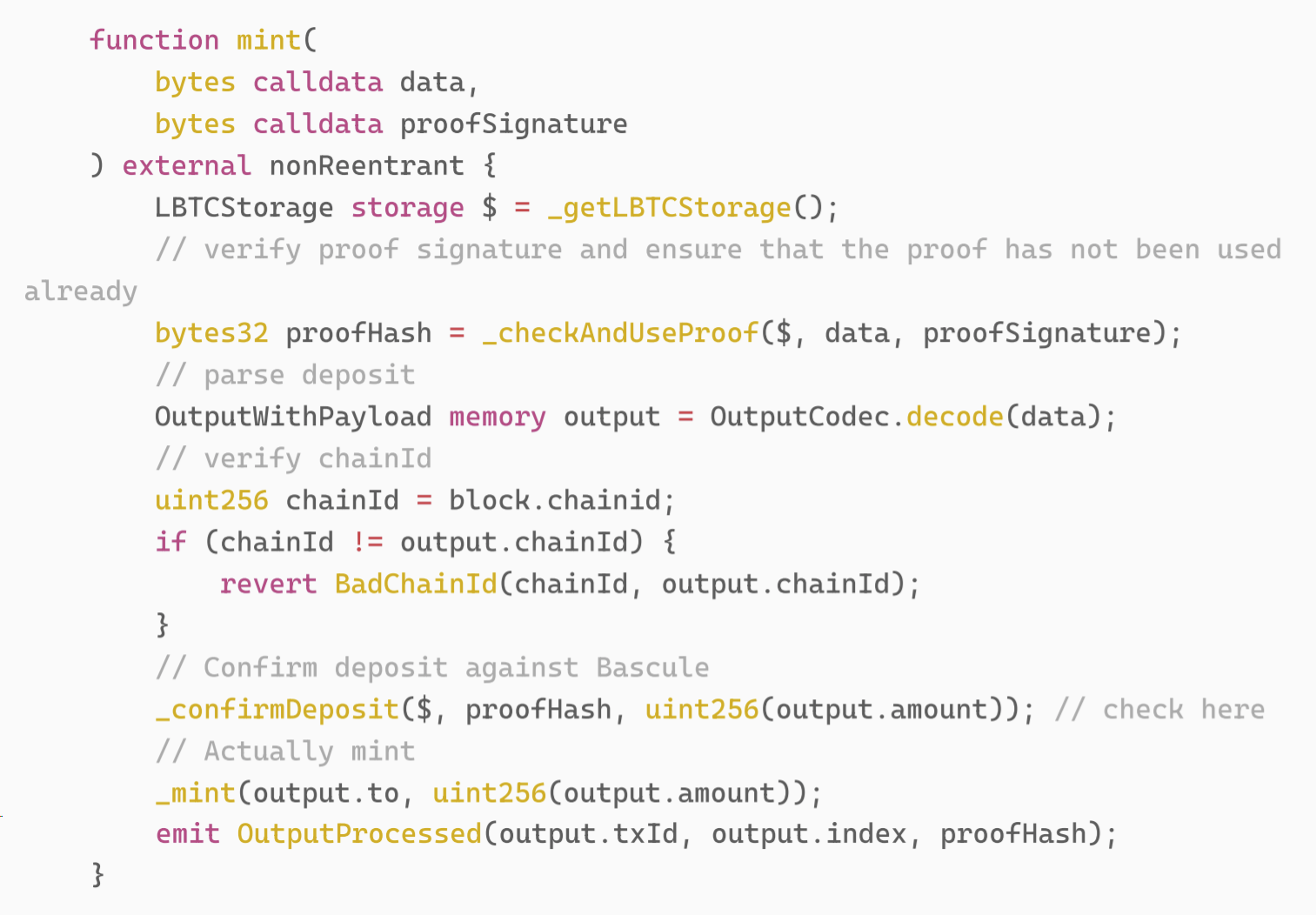
Among them, the implementation of _confirmDeposit is as follows:
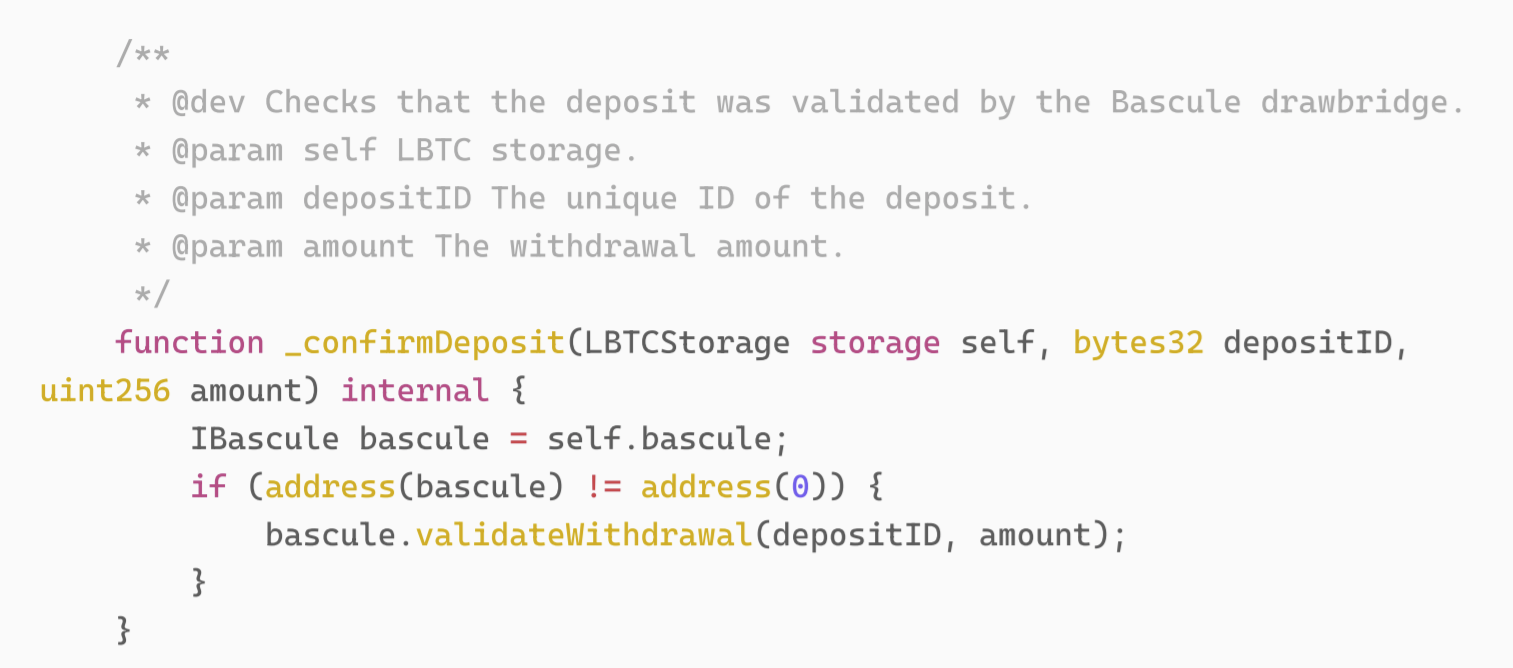
The LBTC official document introduces Bascule as follows: its main functions are an on-chain contract and an off-chain system to prevent attackers from attacking.

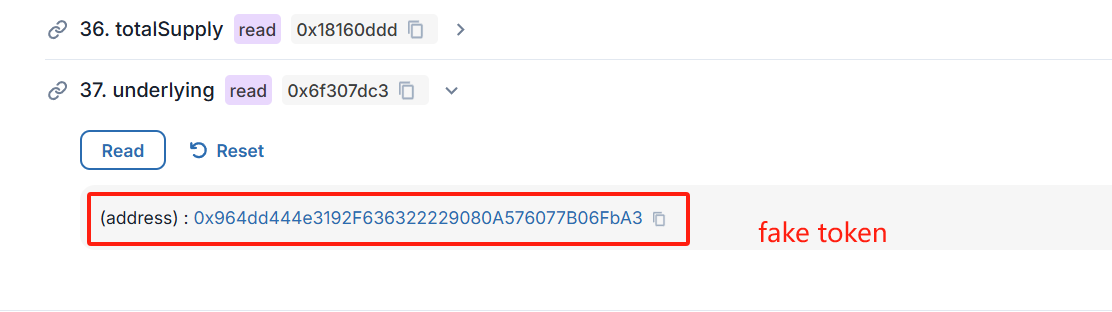
Because the Bascule of this LBTC has no corresponding contract, the attacker can mint it at will. Afterwards, the attacker mortgaged the minted LBTC to IonicMoney and withdrew the funds of all pools to complete the attack. Therefore, the root cause of this attack is that IonicMoney did not verify whether LBTC was an officially created contract when creating the lending pool, resulting in the unlying assets of the lending pool being fake tokens. The attacker minted it at will and emptied all funds through borrow.
Summarize
The main cause of this vulnerability is that the IonicMoney project did not verify whether the contract corresponding to the asset was officially deployed when creating the lending pool, resulting in the undeleting asset of the lending pool being a fake token. It is recommended that the project party conduct multiple verifications when designing the economic model, price calculation mechanism and code operation logic, try to select multiple audit companies for cross-audits when auditing the contract before going online, and finally check whether the corresponding token is officially deployed when deploying before going online.












