作者:九九 & Lisa
编辑:Sherry
背景
2025年 3 月30 日,根据慢雾 MistEye 安全监控系统监测,Ethereum 链上的杠杆交易项目 SIR.trading (@leveragesir) 遭攻击,损失价值超 30 万美元的资产。慢雾安全团队对该事件展开分析,并将结果分享如下:
(https://x.com/SlowMist_Team/status/1906245980770746449)
相关信息
攻击者地址:
https://etherscan.io/address/0x27defcfa6498f957918f407ed8a58eba2884768c
存在漏洞的合约地址:
https://etherscan.io/address/0xb91ae2c8365fd45030aba84a4666c4db074e53e7#code
攻击交易:
https://etherscan.io/tx/0xa05f047ddfdad9126624c4496b5d4a59f961ee7c091e7b4e38cee86f1335736f
前置知识
Solidity 0.8.24 版本(2024 年 1 月发布)引入了基于 EIP-1153 的瞬态存储(transient storage) 特性。这是一种新的数据存储位置,旨在为开发者提供一种低成本、交易期间有效的临时存储方式。
瞬态存储是一种与存储(storage)、内存(memory) 和调用数据(calldata) 并列的新数据位置。其核心特点是数据仅在当前交易执行期间有效,交易结束后会被自动清除。访问和修改瞬态存储通过两个新的 EVM 指令实现:
- TSTORE(key, value):将256 位的值value存储到瞬态存储的指定键key对应的内存中。
- TLOAD(key):从瞬态存储的指定键key对应的内存中读取256 位的值。
该特性主要有以下特点:
- 低 gas 成本:TSTORE 和 TLOAD 的 gas 成本固定为 100,相当于热存储访问(warm storage access)。相比之下,常规存储操作(SSTORE) 在首次写入(从 0 到非 0)时可能高达 20,000 gas,更新时也至少需要 5,000 gas。
- 交易内持久性:瞬态存储的数据在整个交易期间保持有效,包括所有函数调用和子调用,适合需要跨调用共享临时状态的场景。
- 自动清除:交易结束后,瞬态存储自动重置为零,无需手动清理,减少了开发者维护成本。
根本原因
本次被黑事件的根本原因是,在函数中调用tstore 进行瞬态存储的值在函数调用结束后并没有被清空,导致攻击者可以利用这个特性构造特定的恶意地址来绕过权限检查转出代币。
攻击步骤
1. 攻击者首先创建两个恶意代币 A 和 B,之后在 UniswapV3 上为这两个代币创建池子并注入流动性,其中 A 代币为攻击合约。
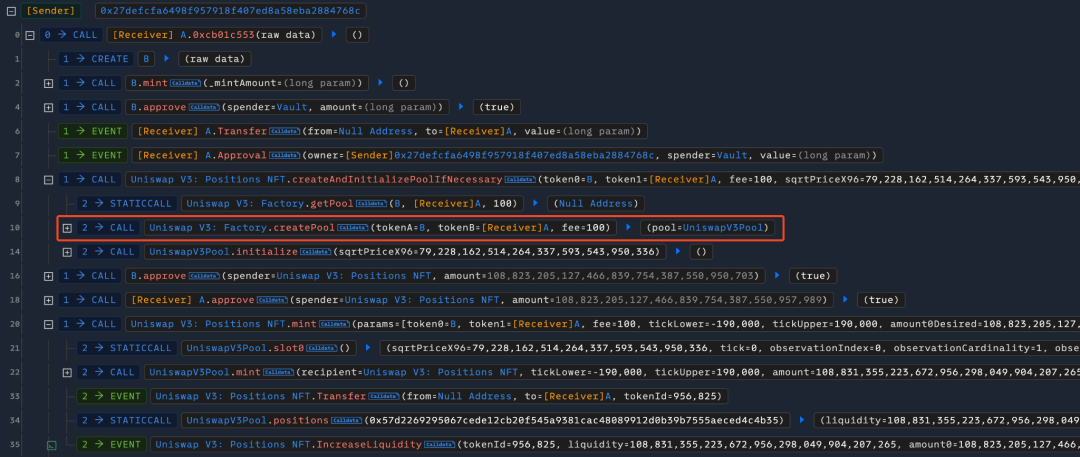
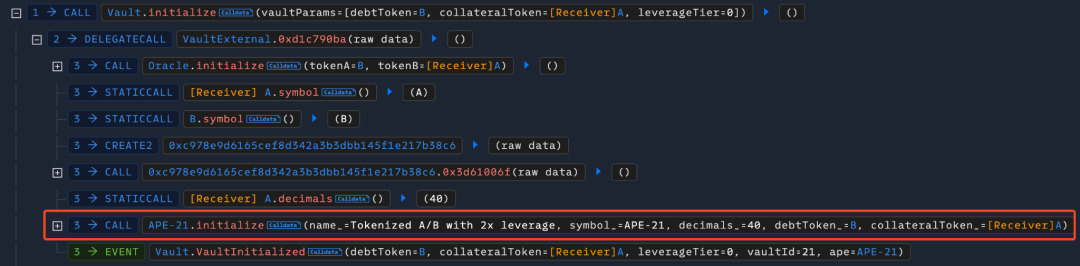
2. 接着攻击者调用 Vault 合约的 initialize 函数,以 A 代币为抵押品代币,B 代币为债务代币创建一个杠杆交易市场 APE-21。
3. 紧跟着攻击者调用 Vault 合约的 mint 函数,存入债务代币 B 铸造杠杆代币 APE。
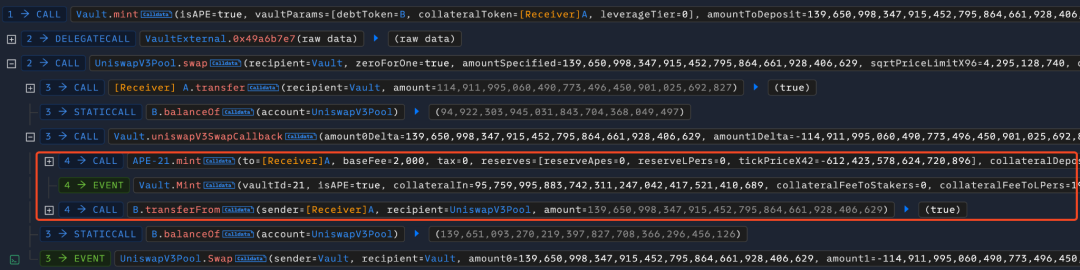
跟进到mint 函数中,我们发现当需要存入债务代币 B 去铸造杠杆代币时,需要传入的 collateralToDepositMin 参数的值不能等于 0,之后会通过 UniswapV3 先将 B 代币兑换成抵押品代币 A 并转入 Vault 中,其中会将攻击者先前创建的 UniswapV3 池子的地址进行第一次瞬态存储。
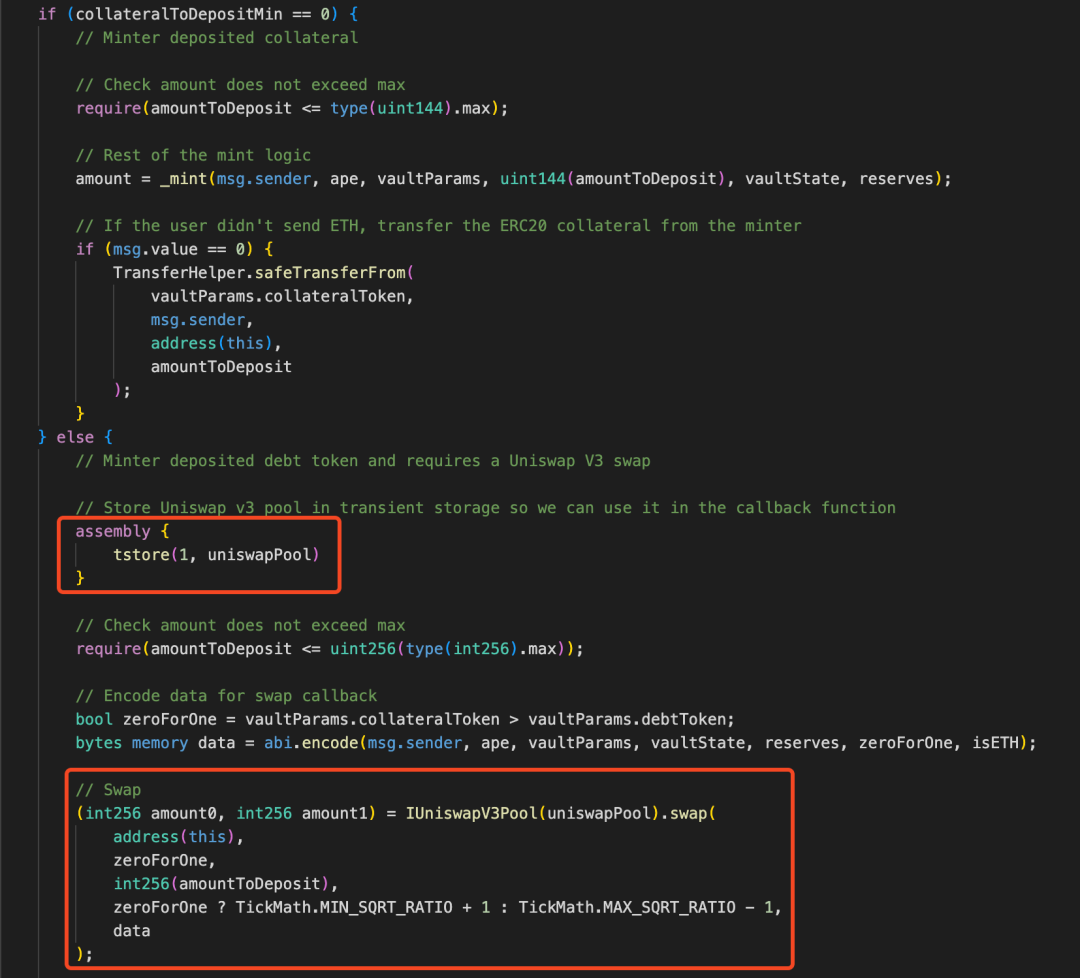
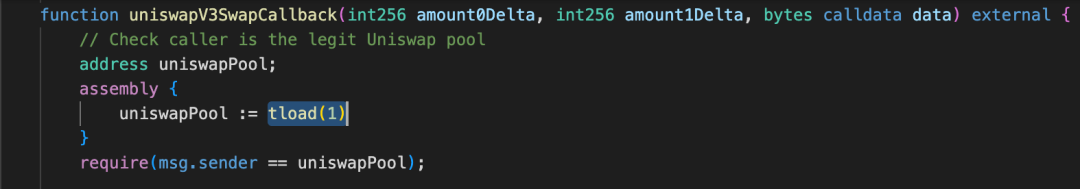
当UniswapV3 池子进行兑换操作时,会回调 Vault 合约的uniswapV3SwapCallback函数。可以看到:该函数首先会用tload 从先前瞬态存储的指定键 1 对应的内存中取出值,来验证调用者是否是 UniswapV3 池子,接着从铸造者地址转出债务代币 B 并铸造杠杆代币 APE,最后将铸造的数量 amount 进行第二次瞬态存储,保存在指定键 1 对应的内存中,用作 mint 函数的返回值。这里需要铸造的数量是攻击者提前计算控制好的,其值为 95759995883742311247042417521410689。
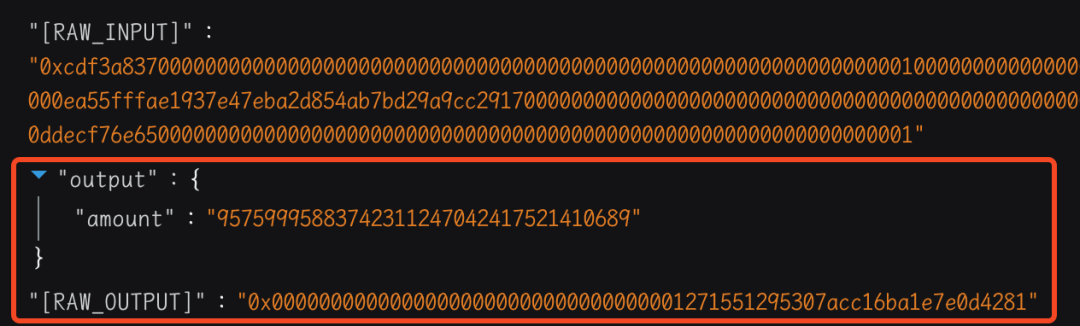
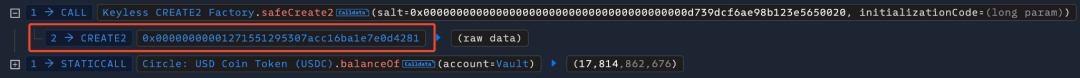
4. 攻击者之后调用 Keyless CREATE2 Factory 合约的 safeCreate2 函数来创建一个恶意的合约,其合约地址 0x00000000001271551295307acc16ba1e7e0d4281,与第二次瞬态存储的值相同。
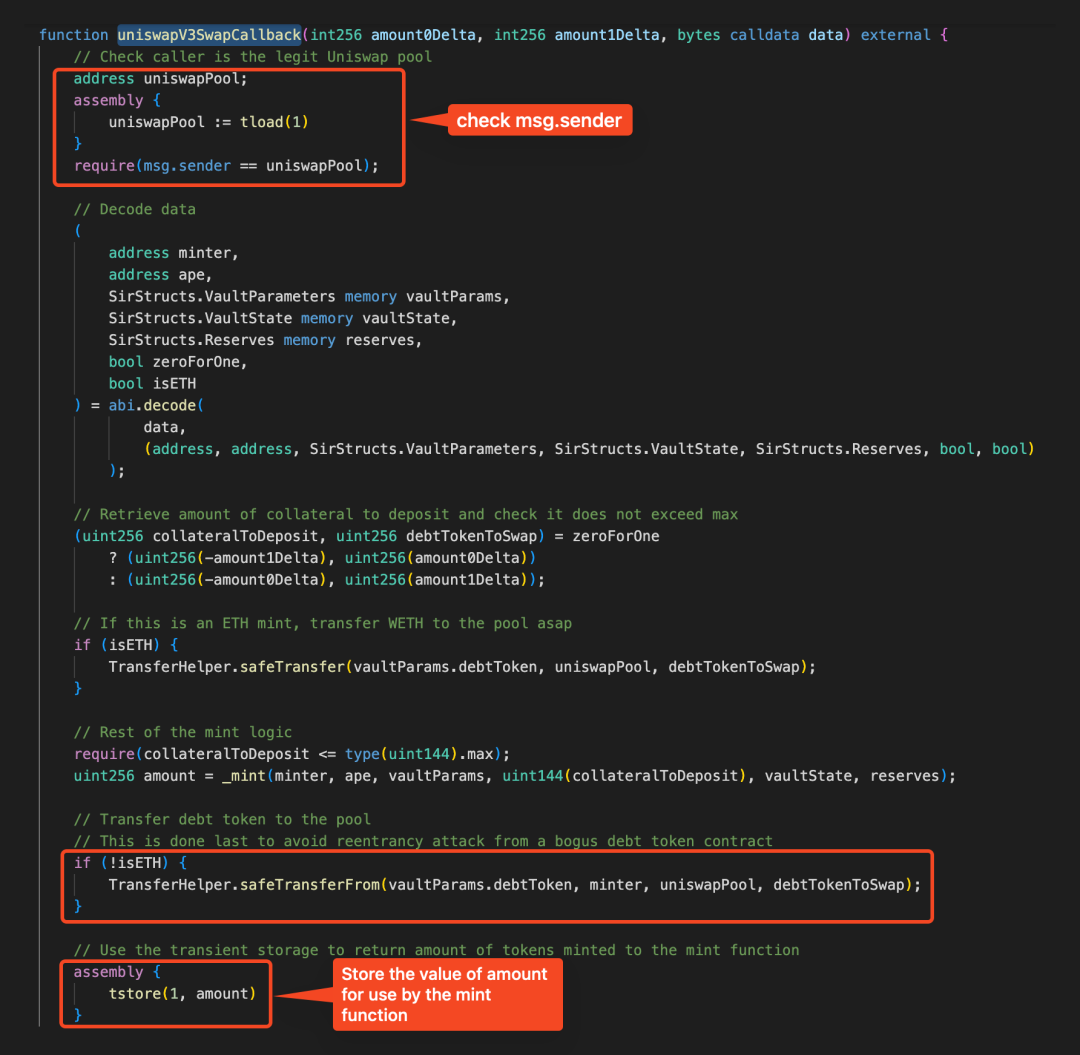
5. 接着攻击者通过该恶意合约去直接调用 Vault 合约的uniswapV3SwapCallback函数转出代币。
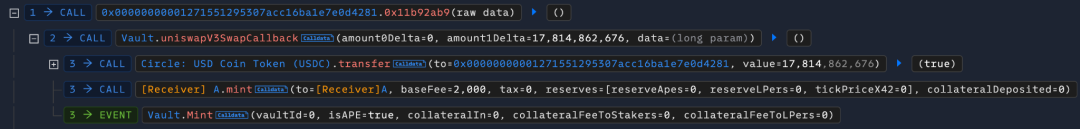
因为uniswapV3SwapCallback函数是通过tload(1) 来获取验证调用者是否是 UniswapV3 池子,然而在先前的铸造操作中,指定键 1 对应内存中的值被保存为铸造的数量 95759995883742311247042417521410689,并且该内存中的值在mint 函数调用后并没有进行清空,所以使得此刻 uniswapPool 的地址被获取为 0x00000000001271551295307acc16ba1e7e0d4281,导致对调用者的身份检查被错误地通过。
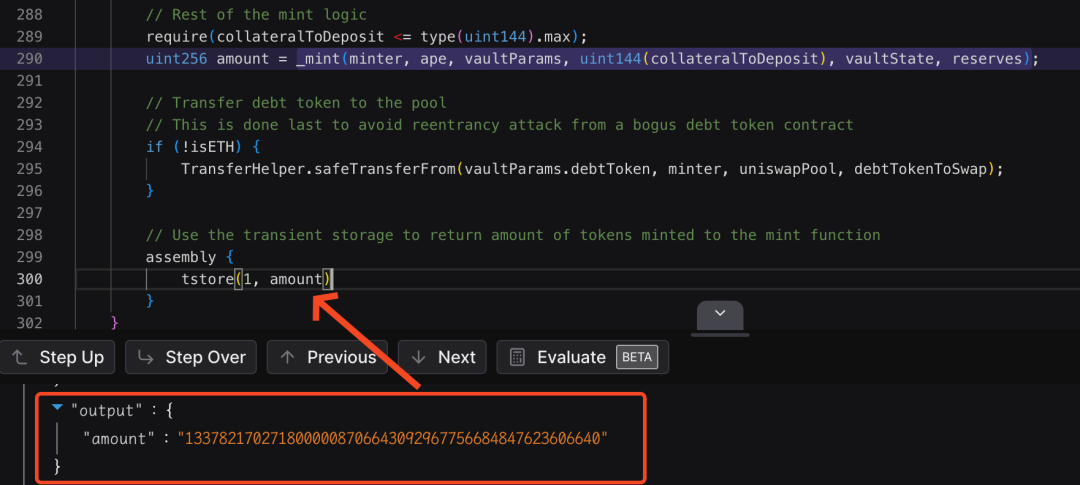
并且攻击者提前计算好了需要转出的代币数量,将最终铸造的数量amount 构造为指定的值:1337821702718000008706643092967756684847623606640。同样的,在这一次调用uniswapV3SwapCallback函数的最后,会进行第三次的瞬态存储,将该值保存到指定键1 对应内存中。这是需要让该值与攻击合约(A 代币)的地址的值 0xea55fffae1937e47eba2d854ab7bd29a9cc29170 相同,才能让之后对调用者的检查通过。
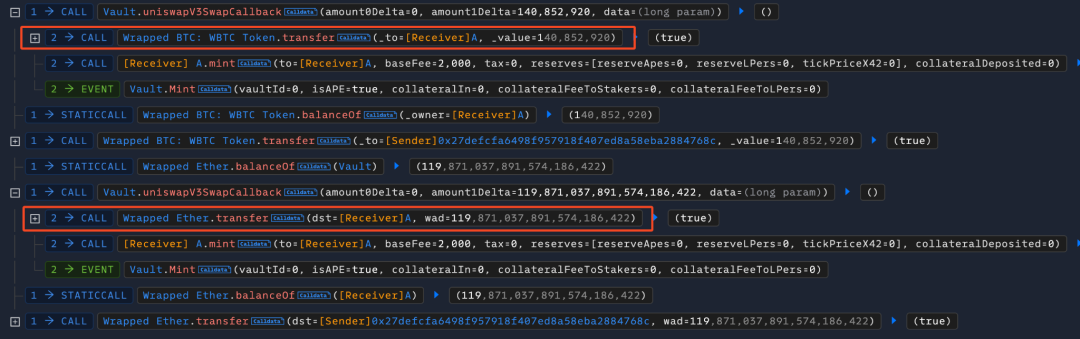
6. 最后,攻击者就可以直接通过攻击合约(A代币)去调用 Vault 合约的uniswapV3SwapCallback函数,将Vault 合约中的其他代币(WBTC、WETH) 转出获利。
MistTrack 分析
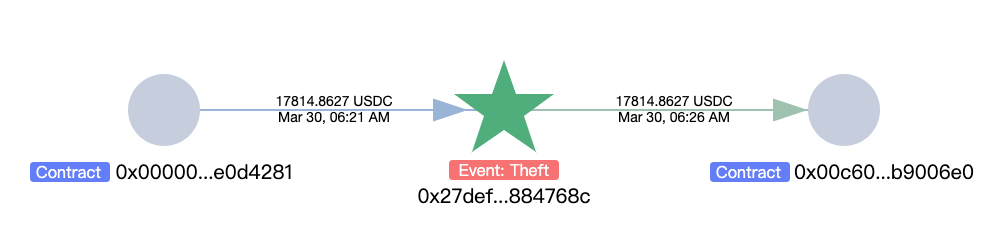
据链上反洗钱与追踪工具MistTrack 的分析,攻击者 (0x27defcfa6498f957918f407ed8a58eba2884768c) 盗取了约 30 万美元的资产,包括 17,814.8626 USDC, 1.4085 WBTC 和 119.871 WETH。
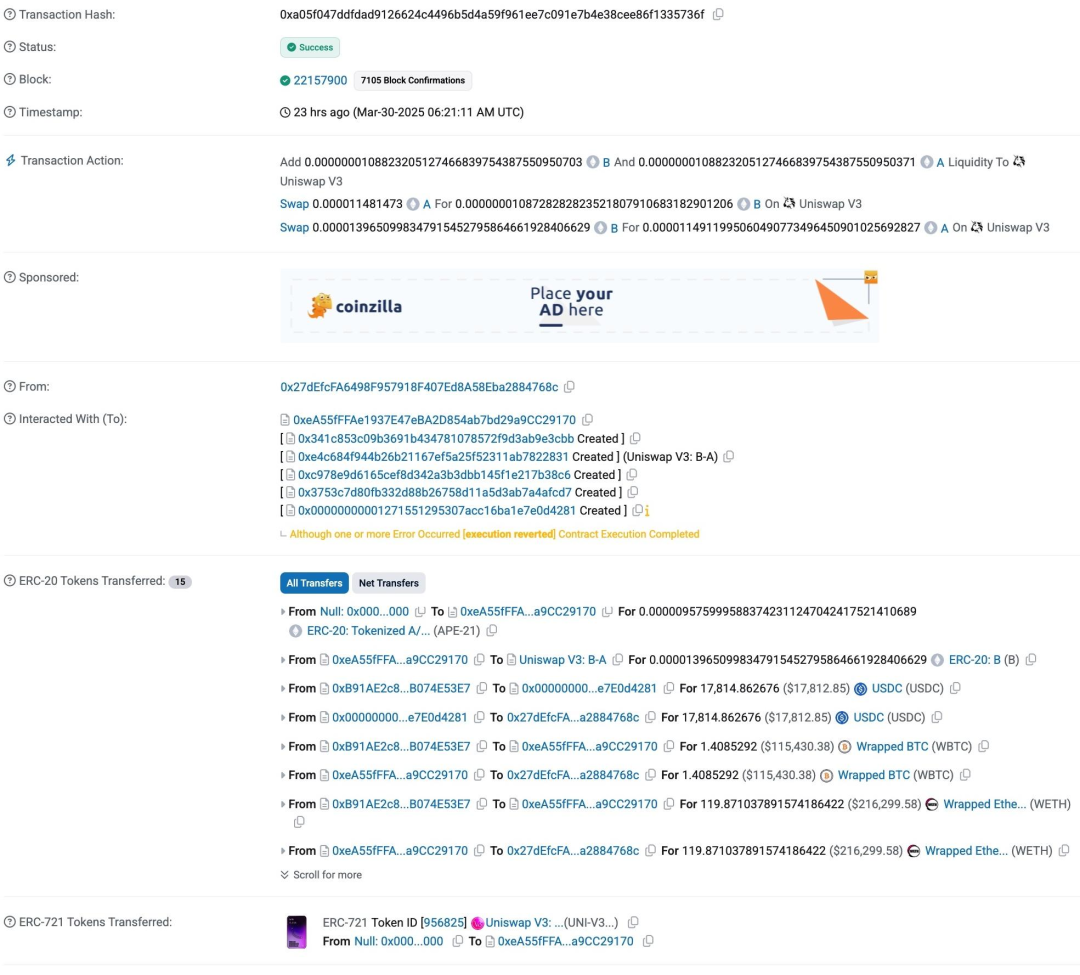
其中WBTC 被兑换为 63.5596 WETH,USDC 被兑换为 9.7122 WETH:
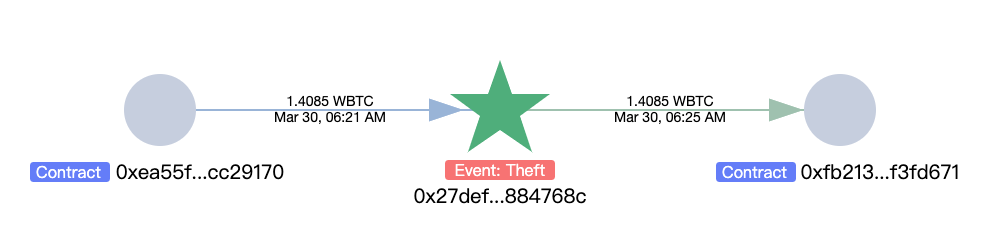
接着,共193.1428 WETH 被转入 Railgun:
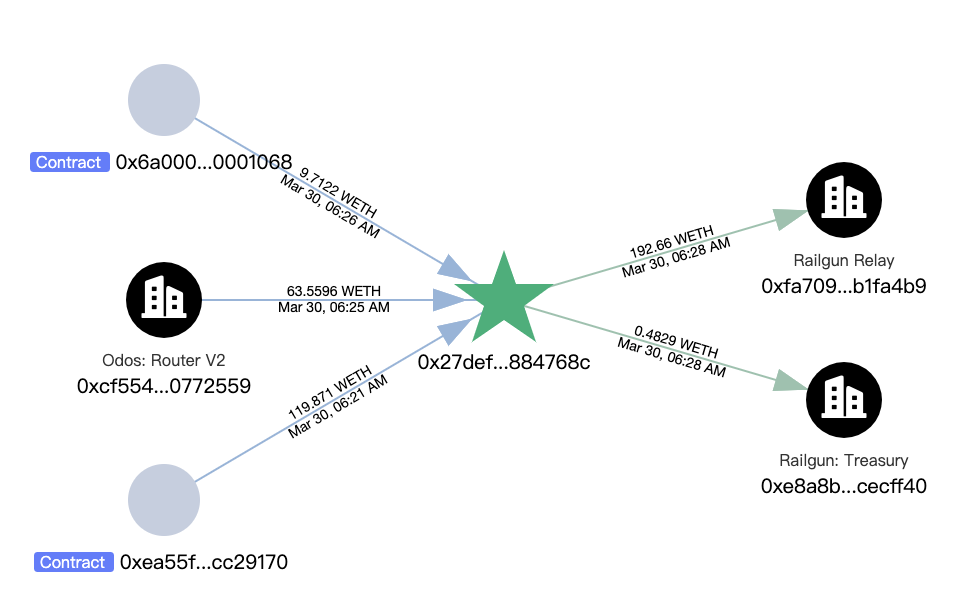
此外,攻击者的初始资金来源于Railgun 转入的 0.3 ETH:
总结
本次攻击的核心在于攻击者利用项目中瞬态存储不会在函数调用后将保存的值立即清空,而是会在整个交易期间中一直保存的特性,从而绕过了回调函数的权限验证来获利。慢雾安全团队建议项目方应该根据相应的业务逻辑在函数调用结束后立即使用tstore(key, 0) 将瞬态存储中的值进行清除。此外,应当对项目的合约代码加强审计与安全测试,从而避免类似情况的发生。






