Author: Liz & Lisa
Editor: Sherry
background
In the field of crypto assets, social engineering attacks are becoming a major threat to the security of user funds. Since 2025, a large number of social engineering scams targeting Coinbase users have surfaced, attracting widespread attention from the community. It is not difficult to see from the community's discussions that such incidents are not isolated cases, but a type of scam with persistent and organized characteristics.
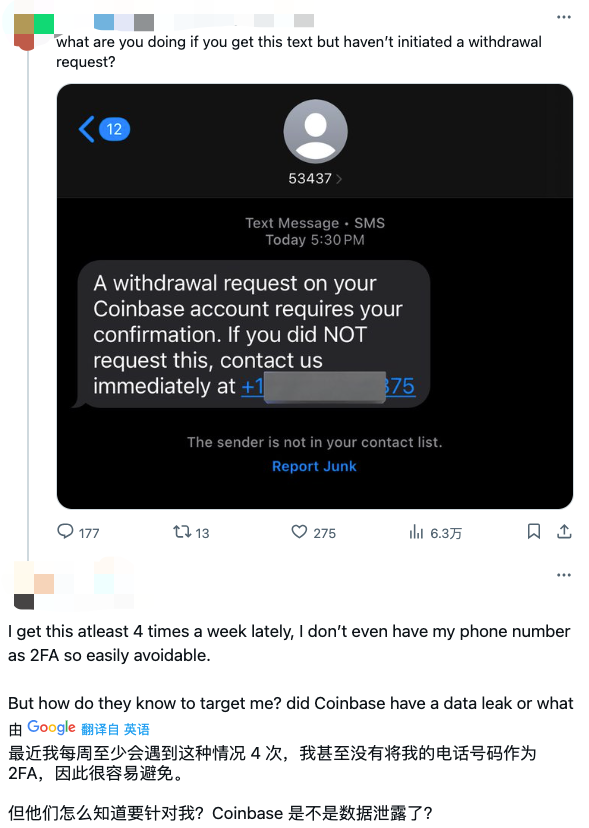
On May 15, Coinbase released an announcement confirming previous speculations that there was an "insider" in Coinbase. It is reported that the U.S. Department of Justice (DOJ) has launched an investigation into the data leak.
This article will reveal the main methods used by scammers by collating information provided by multiple security researchers and victims, and explore how to effectively deal with such scams from the perspectives of both platforms and users.
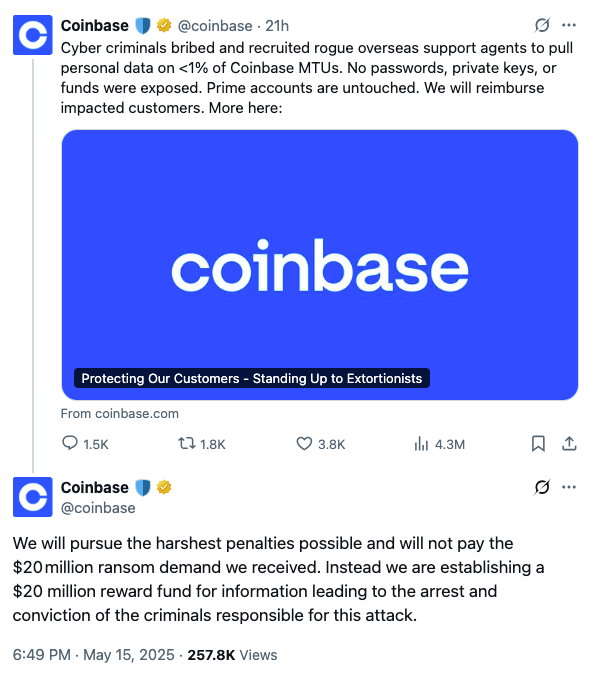
(https://x.com/coinbase/status/1922967576209998133)
Historical analysis
“Over $45 million stolen from Coinbase users in social engineering scams in the past week alone,” Chainalysis Detective Zach wrote in a Telegram update on May 7.
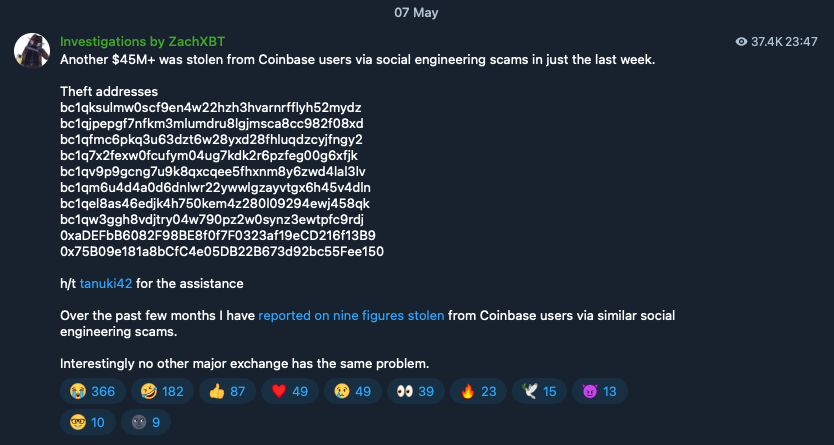
In the past year, Zach has repeatedly disclosed Coinbase user theft incidents on his Telegram channel and X platform, with individual victims losing tens of millions of dollars. In February 2025, Zach published a detailed investigation, saying that the total amount of funds stolen from similar scams between December 2024 and January 2025 alone exceeded $65 million, and revealed that Coinbase is facing a serious "social engineering fraud" crisis, and such attacks are continuing to infringe on user asset security at an average annual scale of $300 million. He also pointed out:
- The gangs that lead this type of fraud can be divided into two main categories: one is low-level attackers (skids) from the COM circle, and the other is cybercrime organizations based in India;
- The fraud gangs mainly target American users, with standardized methods and mature rhetoric processes;
- The actual amount of loss may be much higher than the statistics visible on the chain, because it does not include undisclosed information such as Coinbase customer service tickets and police report records that are inaccessible.
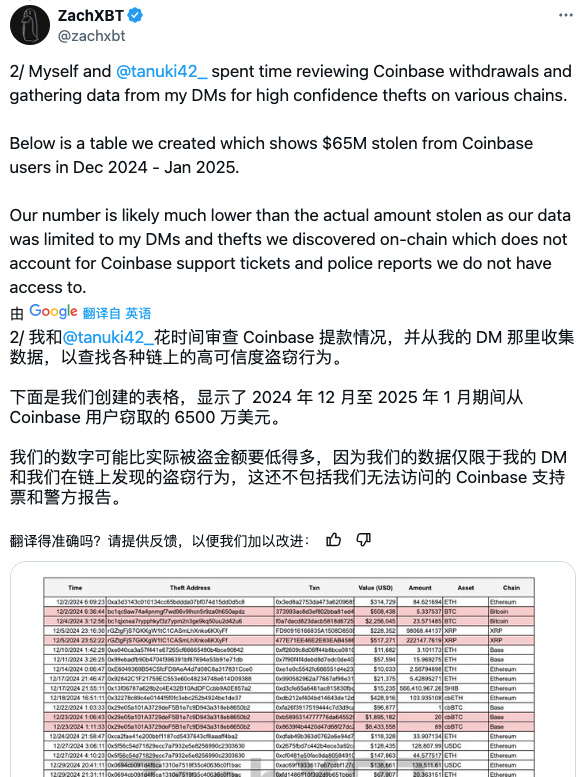
(https://x.com/zachxbt/status/1886411891213230114)
Scam Methods
In this incident, Coinbase's technical system was not breached. The scammers used the privileges of internal employees to obtain sensitive information of some users. This information includes: name, address, contact information, account data, ID card photos, etc. The ultimate goal of the scammers is to use social engineering methods to guide users to transfer money.

(https://www.coinbase.com/blog/protecting-our-customers-standing-up-to-extortionists)
This type of attack method has changed the traditional "cast a net" phishing method and turned to "precision attack", which can be called "tailor-made" social engineering fraud. The typical path of the crime is as follows:
1. Contact the user as "official customer service"
Scammers use fake telephone systems (PBX) to impersonate Coinbase customer service and call users to say that their "accounts have been illegally logged in" or "withdrawal anomalies have been detected" to create an atmosphere of urgency. They then send simulated phishing emails or text messages containing fake work order numbers or "recovery process" links to guide users. These links may point to cloned Coinbase interfaces and even send emails that appear to be from official domains. Some emails use redirection technology to bypass security protection.
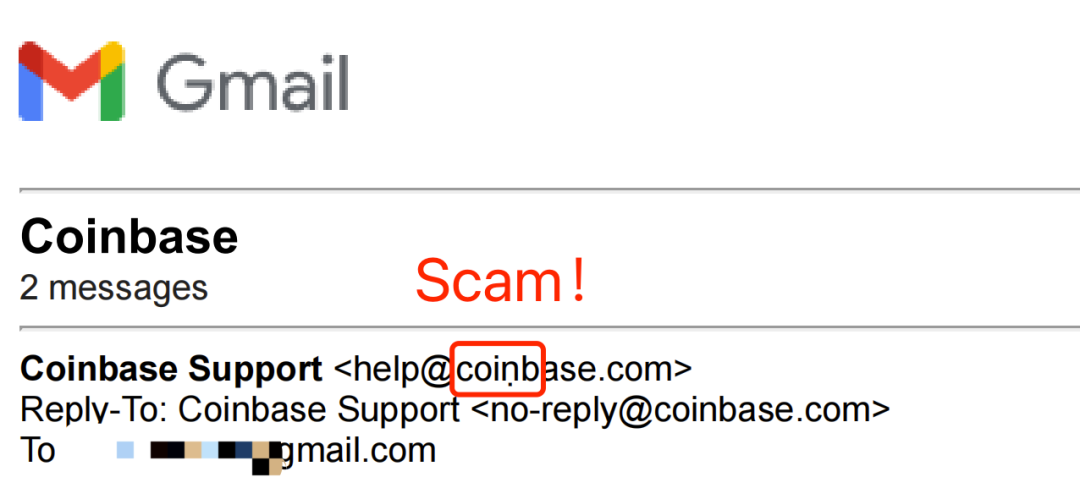
2. Guide users to download Coinbase Wallet
Scammers will guide users to transfer funds to a "safe wallet" on the grounds of "protecting assets". They will also assist users in installing Coinbase Wallet and instruct them to transfer assets originally hosted on Coinbase to a newly created wallet.
3. Induce users to use the mnemonic phrases provided by scammers
Unlike the traditional "fraudulent mnemonic phrases", scammers directly provide a set of mnemonic phrases generated by themselves, inducing users to use them as the "official new wallet".
4. Fraudsters steal funds
Victims are easily trapped when they are nervous, anxious and trust the "customer service" - in their view, the "official" new wallet is naturally safer than the "suspected hacked" old wallet. As a result, once the funds are transferred to this new wallet, the scammers can immediately transfer them away. Not your keys, not your coins. - This concept has been bloodily verified again in social engineering attacks.
In addition, some phishing emails claim that "Coinbase will fully migrate to self-hosted wallets due to a class action ruling" and require users to complete asset migration before April 1. Under the tight time pressure and the psychological suggestion of "official instructions", users are more likely to cooperate with the operation.
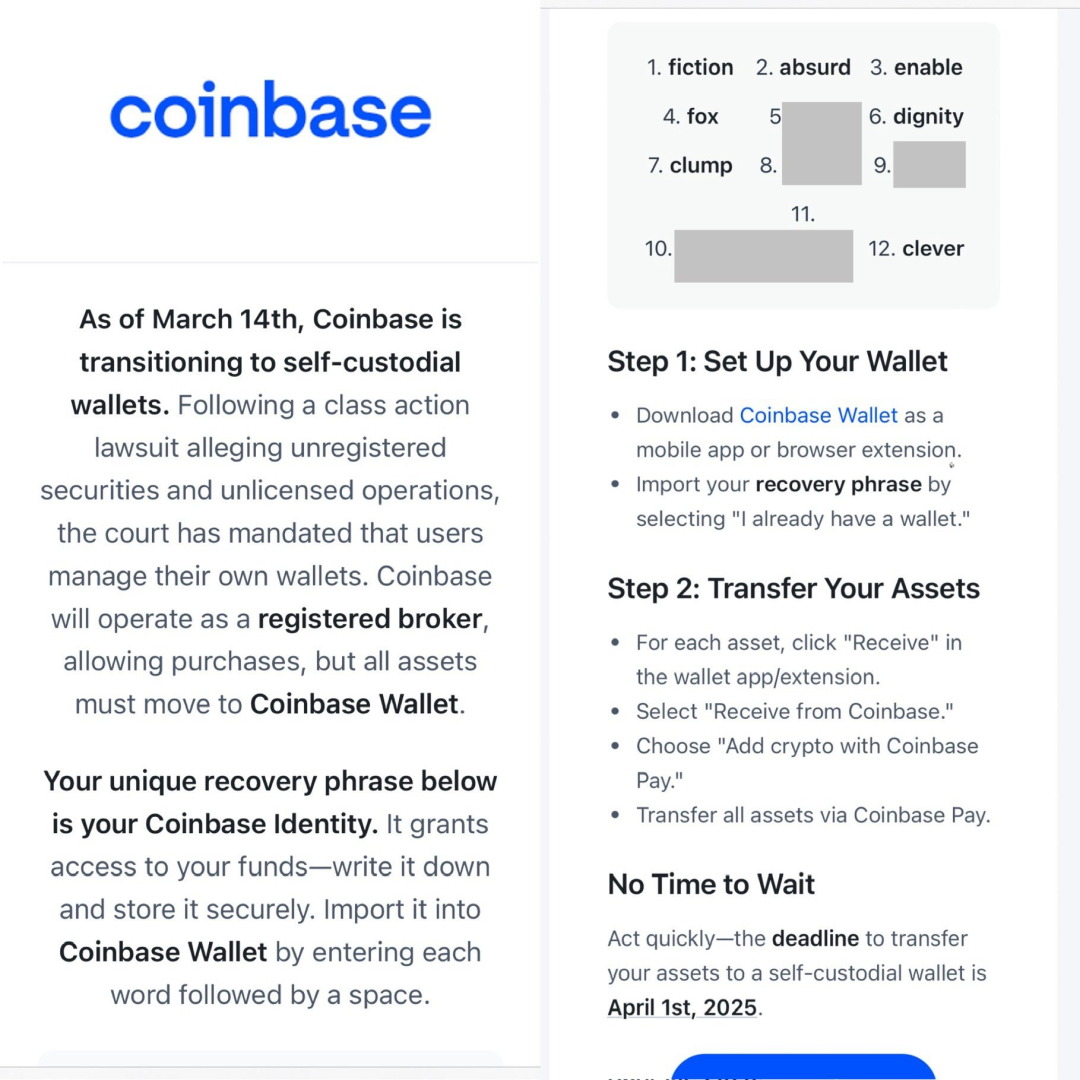
(https://x.com/SteveKBark/status/1900605757025882440)
According to @NanoBaiter, these attacks are often planned and implemented in an organized manner:
- The fraud tool chain is complete: the scammers use PBX systems (such as FreePBX and Bitrix24) to forge incoming call numbers and simulate official customer service calls. When sending phishing emails, they use @spoofmailer_bot in Telegram to imitate the official Coinbase email address, and attach an "account recovery guide" to guide transfers.
- Precise targeting: Scammers rely on stolen user data purchased from Telegram channels and the dark web (such as "5k COINBASE US2", "100K_USA-gemini_sample"), targeting US Coinbase users as their main target. They even use ChatGPT to process the stolen data, split and reorganize phone numbers, generate TXT files in batches, and then send SMS fraud through blasting software.
- The fraud process is coherent: From phone calls, text messages to emails, the fraud path is usually seamless and coherent. Common phishing phrases include "the account has received a withdrawal request", "the password has been reset", "the account has abnormal login", etc., which continuously induce victims to perform "security verification" until the wallet transfer is completed.
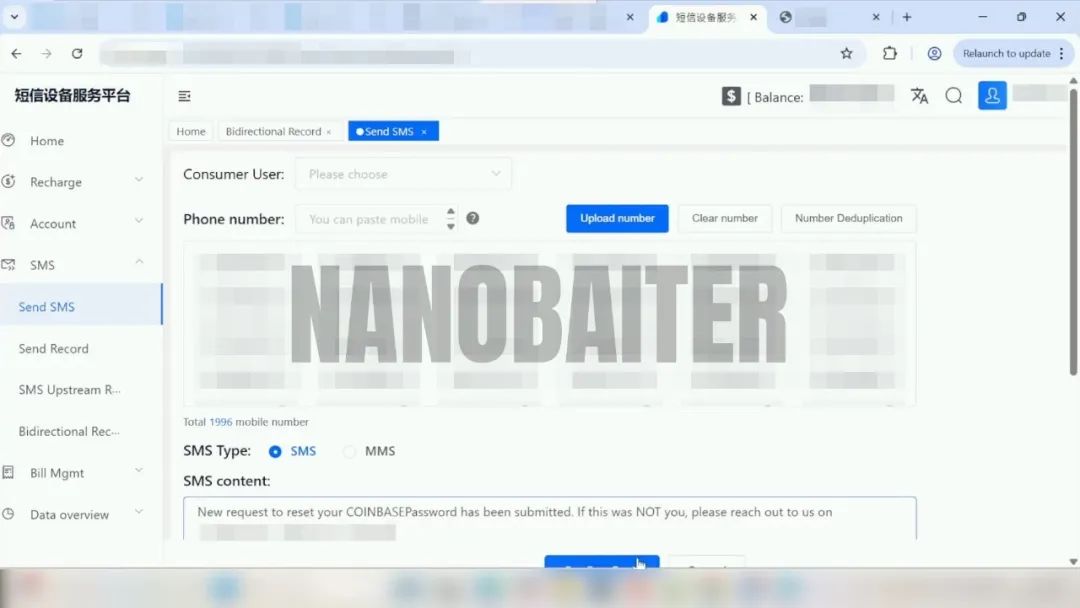
(https://x.com/NanoBaiter/status/1923099215112057010)
MistTrack Analysis
We used the on-chain anti-money laundering and tracking system MistTrack (https://misttrack.io/) to analyze some of the scammers’ addresses that Zach had disclosed and that we received through our form, and found that these scammers have strong on-chain operation capabilities. Here are some key information:
The scammers' targets cover a variety of assets held by Coinbase users. The active time of these addresses is concentrated between December 2024 and May 2025, and the target assets are mainly BTC and ETH. BTC is currently the main target of fraud, and multiple addresses have made a one-time profit of up to hundreds of BTC, with a single transaction worth millions of dollars.
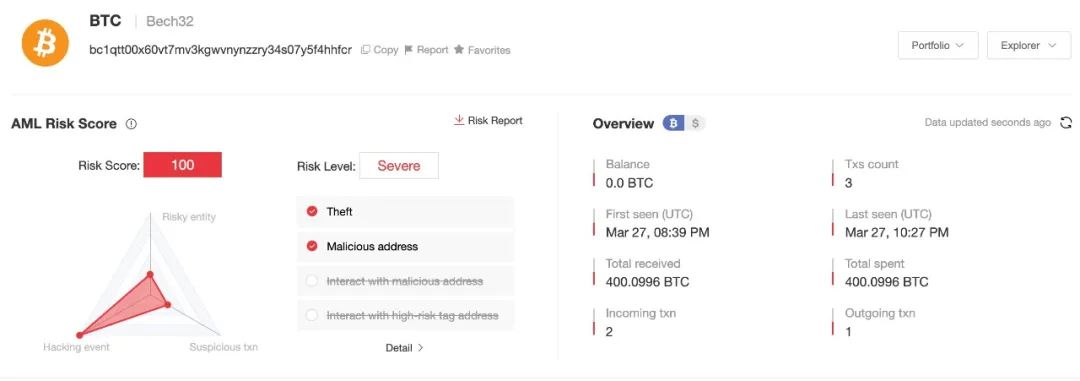
After obtaining the funds, the scammers quickly use a set of laundering processes to exchange and transfer the assets. The main modes are as follows:
- ETH assets are often quickly converted to DAI or USDT through Uniswap, and then dispersed and transferred to multiple new addresses, with some assets entering centralized trading platforms;
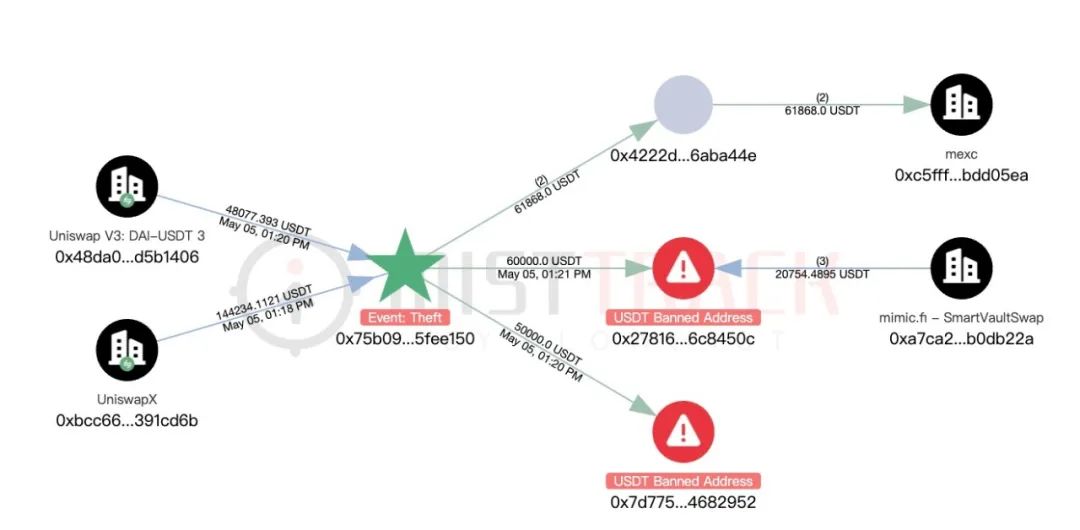
- BTC is mainly transferred to Ethereum through THORChain, Chainflip or Defiway Bridge, and then converted into DAI or USDT to avoid tracking risks.
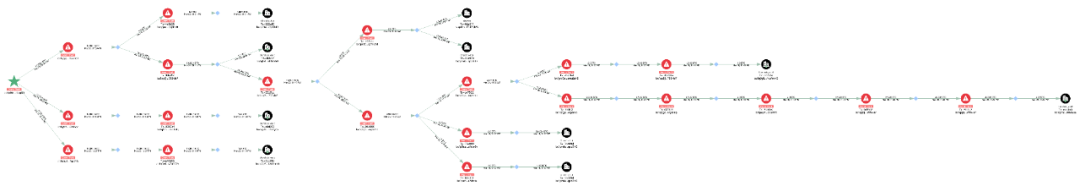
Multiple scam addresses are still in a "dormant" state after receiving DAI or USDT and have not yet been transferred out.
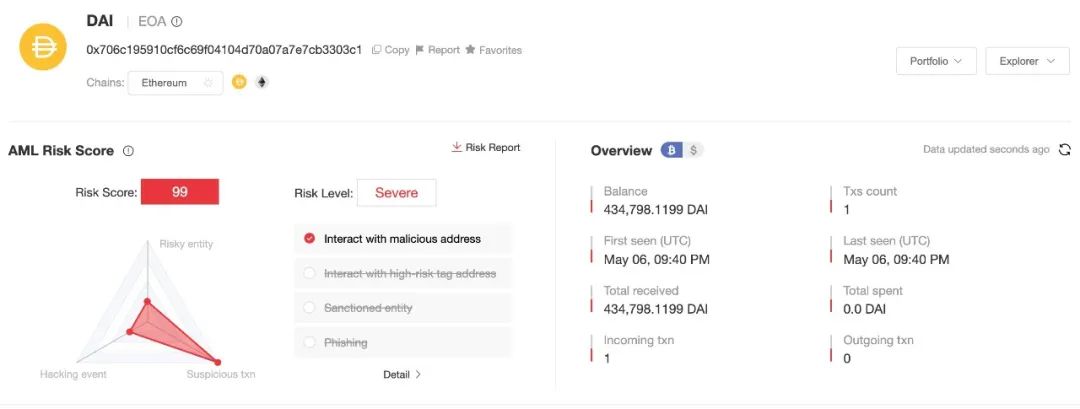
In order to avoid the risk of your address interacting with suspicious addresses and thus facing the risk of your assets being frozen, users are advised to use the on-chain anti-money laundering and tracking system MistTrack (https://misttrack.io/) to perform risk detection on the target address before trading to effectively avoid potential threats.
Countermeasures
platform
The current mainstream security measures are more of a "technical layer" of protection, but social engineering fraud often bypasses these mechanisms and directly attacks users' psychological and behavioral loopholes. Therefore, it is recommended that the platform integrate user education, security training, and usability design to establish a "people-oriented" security line of defense.
- Regularly push anti-fraud education content: Improve users' anti-phishing capabilities through App pop-ups, transaction confirmation interfaces, emails, etc.
- Optimize the risk control model and introduce "interactive abnormal behavior identification": Most social engineering scams will induce users to complete a series of operations (such as transfers, whitelist changes, device binding, etc.) in a short period of time. The platform should identify suspicious interaction combinations (such as "frequent interactions + new addresses + large withdrawals") based on the behavior chain model and trigger a cooling-off period or manual review mechanism.
- Standardize customer service channels and verification mechanisms: Scammers often impersonate customer service to confuse users. The platform should unify telephone, SMS, and email templates, and provide a "customer service verification entrance" to clarify the only official communication channel to avoid confusion.
user
- Implement identity isolation strategy: Avoid sharing the same email address or mobile phone number on multiple platforms to reduce joint risks. You can use leakage query tools to regularly check whether the email address has been leaked.
(https://haveibeenpwned.com/)
- Enable transfer whitelist and withdrawal cooling mechanism: preset trusted addresses to reduce the risk of fund loss in emergency situations.
- Keep an eye on security news: Learn about the latest developments in attack methods through security companies, media, trading platforms and other channels, and stay alert. Currently, the Web3 phishing drill platform created by SlowMist, @DeFiHackLabs and @realScamSniffer is about to be launched. The platform will simulate a variety of typical phishing methods, including social engineering poisoning, signature phishing, malicious contract interaction, etc., and combine the real cases collected in our historical discussions to continuously update the scenario content. Allow users to improve their identification and response capabilities in a risk-free environment.
- Pay attention to offline risks and privacy protection: leakage of personal information may also cause personal safety issues.
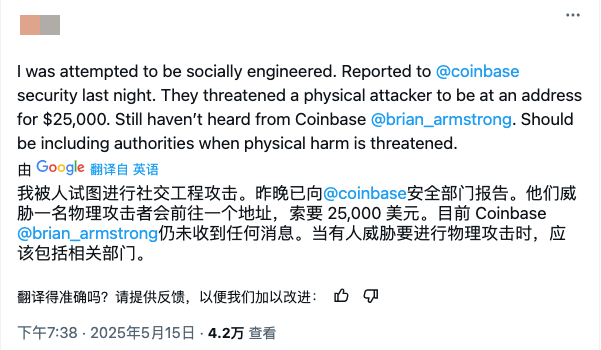
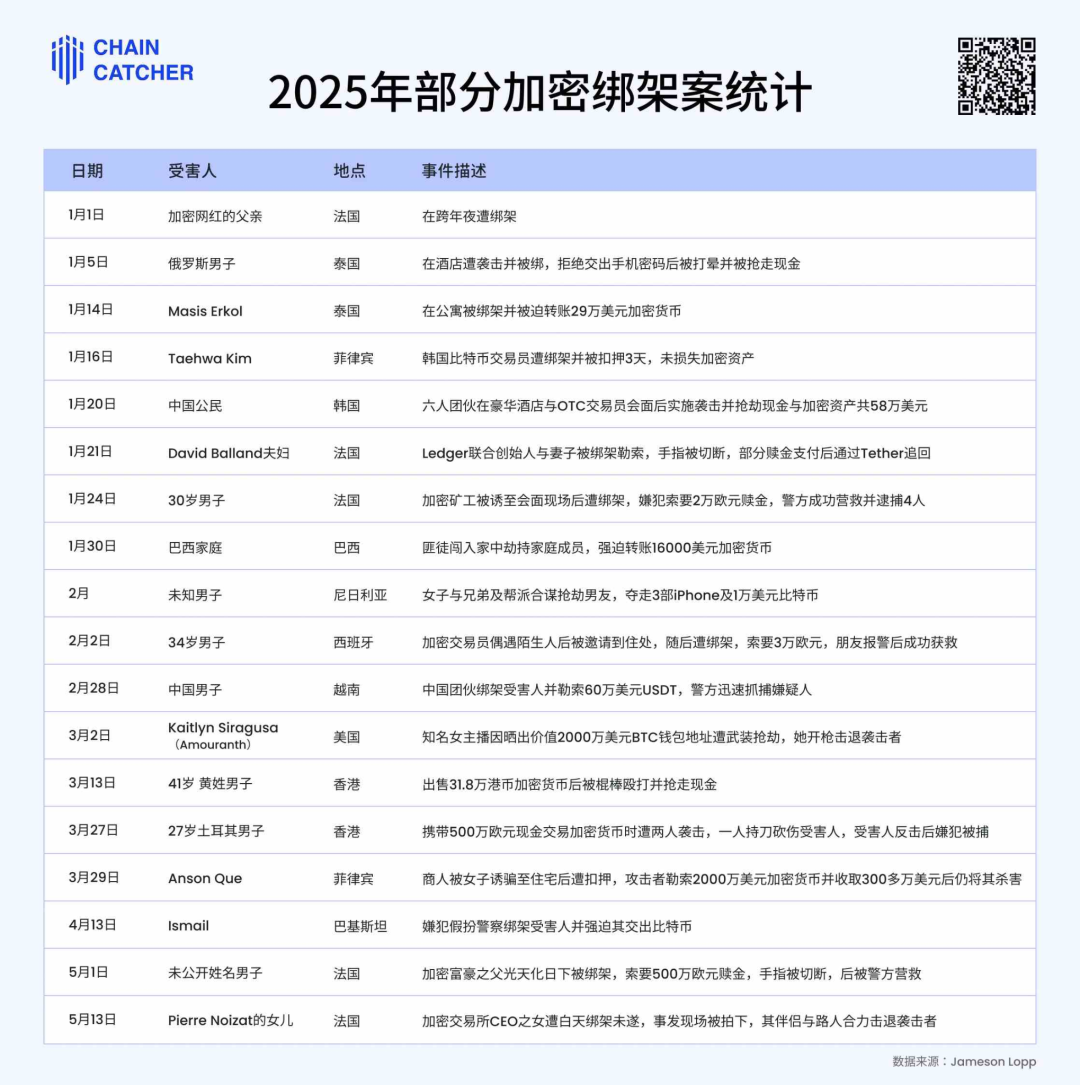
This is not groundless worry. Since the beginning of this year, crypto practitioners/users have encountered many incidents that threaten their personal safety. Given that the leaked data includes names, addresses, contact information, account data, ID photos, etc., relevant users also need to be vigilant and pay attention to safety offline.
In short, be skeptical and keep verifying. For any emergency operation, be sure to ask the other party to prove their identity and verify it independently through official channels to avoid making irreversible decisions under pressure. For more security advice and new attack methods, see the Blockchain Dark Forest Self-Guard Handbook (https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/).
Summarize
This incident once again exposed that in the face of increasingly sophisticated social engineering attack techniques, the industry still has obvious shortcomings in protecting customer data and assets. It is worth noting that even if the relevant positions on the platform do not have financial authority and lack sufficient security awareness and capabilities, serious consequences may occur due to unintentional leakage or subversion. As the platform continues to expand, the complexity of personnel security management and control has increased, and it has become one of the most difficult risks to overcome in the industry. Therefore, while strengthening the on-chain security mechanism, the platform must also systematically build a "social engineering defense system" covering internal personnel and outsourced services, and incorporate human risks into the overall security strategy.
In addition, once it is discovered that the attack is not an isolated incident, but an organized, large-scale and continuous threat, the platform should respond immediately, proactively check for potential vulnerabilities, remind users to take precautions, and control the scope of damage. Only by responding at both the technical and organizational levels can we truly maintain trust and bottom line in an increasingly complex security environment.







