Author: Lisa&Liz
Editor: Liz
background
Recently, the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) announced sanctions against Russia-based Aeza Group and its affiliated entities for providing hosting services for ransomware and information-stealing tools.
(https://home.treasury.gov/news/press-releases/sb0185)
The sanctions cover Aeza Group and its UK front company Aeza International Ltd., two Russian subsidiaries (Aeza Logistic LLC and Cloud Solutions LLC), four executives (CEO Arsenii Penzev, Director Yurii Bozoyan, Technical Director Vladimir Gast, and Administrator Igor Knyazev), and a crypto wallet (TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F).
“Cybercriminals continue to rely heavily on bulletproof hosting providers like Aeza Group to launch devastating ransomware attacks, steal U.S. technology, and sell black market narcotics,” said Bradley T. Smith, Acting Under Secretary of the Treasury for Terrorism and Financial Intelligence. “Treasury will continue to work closely with the United Kingdom and other international partners to uncover the key nodes, infrastructure, and actors that support this criminal ecosystem.”
This sanction action indicates that international law enforcement agencies are extending their focus from the attackers themselves to the technical infrastructure and service providers behind them. This article will sort out the background and operation mode of Aeza Group, and combine the analysis of the on-chain anti-money laundering and tracking tool MistTrack to restore its role in the criminal ecosystem.
Who is Aeza Group?
(https://www.pcmag.com/news/us-sanctions-russian-web-hosting-provider-aeza-for-fueling-malware)
Aeza Group is a bulletproof hosting (BPH) service provider headquartered in St. Petersburg, Russia. It has long provided dedicated servers and anonymous hosting services to cybercrime groups such as ransomware gangs, infostealers operators, and illegal drug trading platforms.
Its clients include: notorious information stealing tool operators such as Lumma and Meduza, which have launched attacks on the US defense industrial base and global technology companies; ransomware and data theft gangs BianLian and RedLine; and Blacksprut, a well-known Russian dark web drug market. Aeza not only provides hosting services for Blacksprut, but also participates in the construction of its technical architecture. According to OFAC, Blacksprut is widely used for the global distribution of fentanyl and other synthetic drugs, posing a serious threat to public safety.
MistTrack Analysis
According to the analysis of MistTrack, an on-chain anti-money laundering and tracking platform, the sanctioned address (TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F) has been active since 2023 and has received more than US$350,000 in USDT.
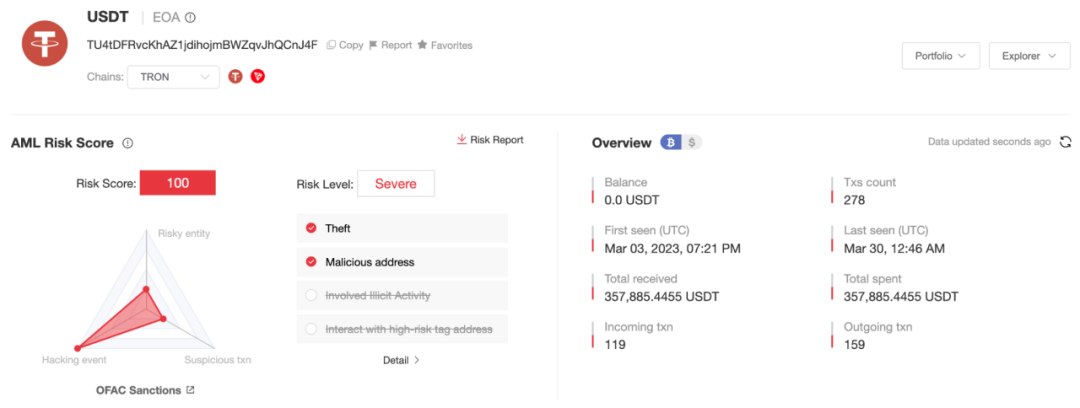
According to MistTrack analysis, this address interacts with the following objects:
- Transferring assets to multiple well-known trading platforms/OTCs, such as Cryptomus, WhiteBIT, etc., for fund laundering;
- Associated with sanctioned entities, such as Garantex and Lumma;
- Associated with the Stealer-as-a-Service platform promoted on Telegram;
- Linked to addresses associated with the dark web drug market Blacksprut.
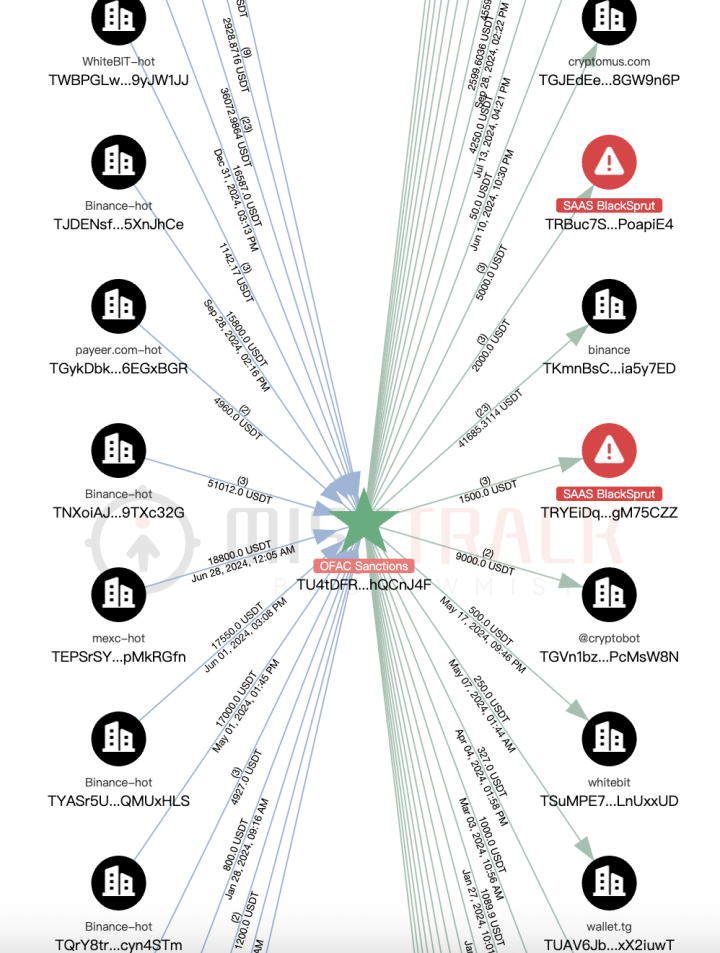
According to MistTrack counterparty function analysis, the proportion of the interaction objects of this address is as follows:
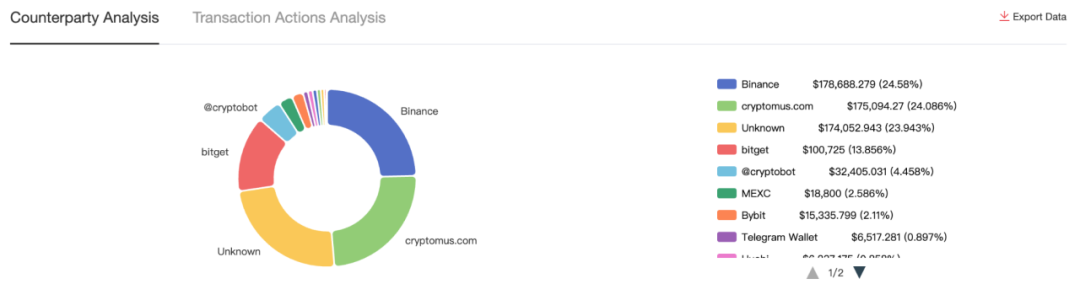
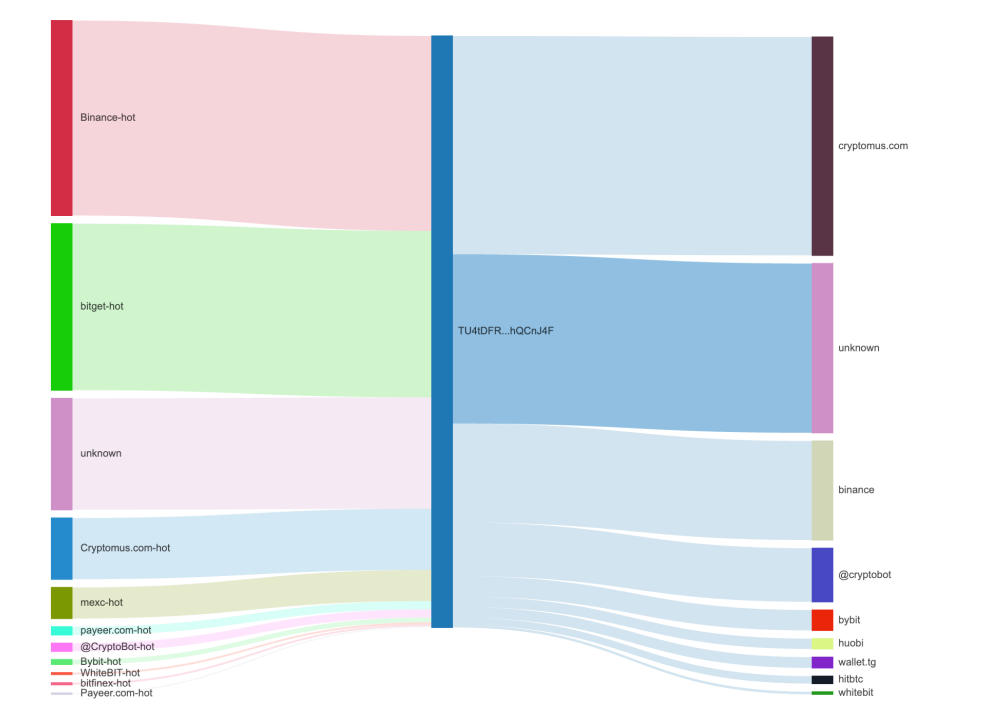
In addition, we also found that on July 2, Aeza's Telegram was still active, and the administrator released an alternative URL in case users could not successfully log in to the main site:
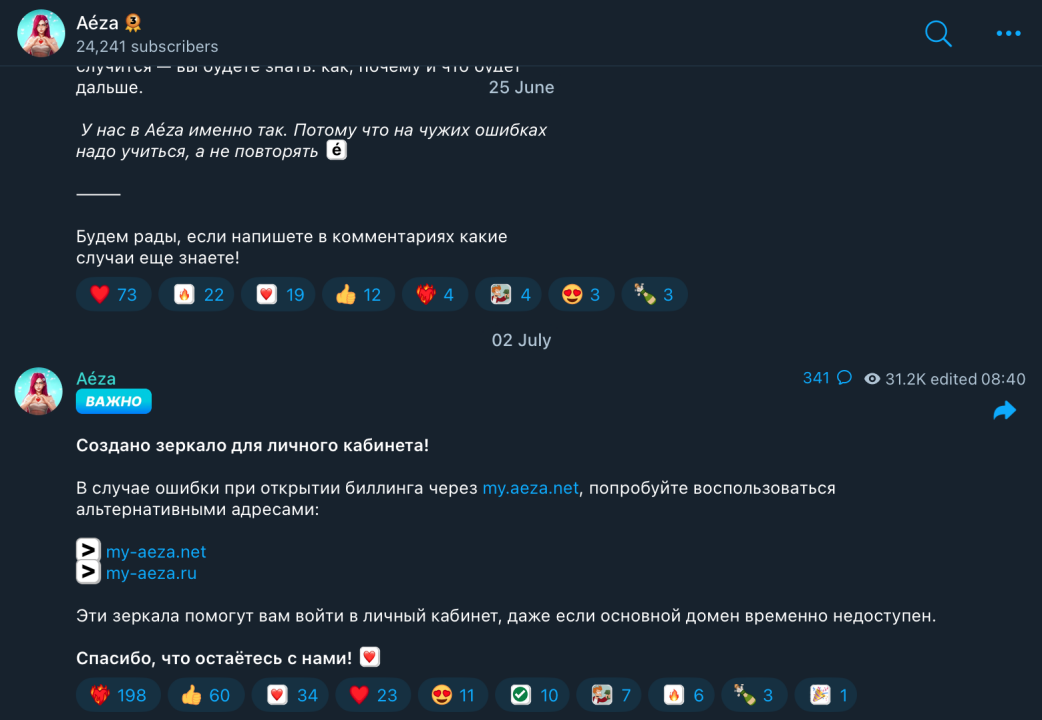
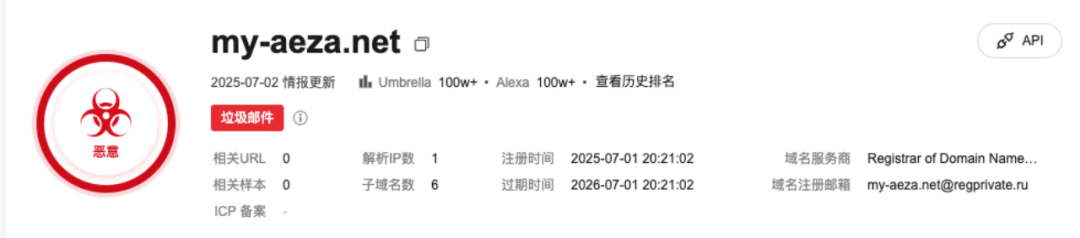
Upon inquiry, it was found that the two alternative URLs were created on the same day that OFAC announced sanctions against Aeza.
Conclusion
The sanctions against Aeza Group show that global regulators are extending their targets from attackers to the technical service networks behind them. Custodians, anonymous communication tools, and payment channels are becoming new focuses of compliance crackdowns. For enterprises, exchanges, and service providers, KYC/KYT is no longer an "optional question". If they accidentally establish business connections with high-risk targets, they may face the risk of joint sanctions.







